Embed presentation
Download as PDF, PPTX






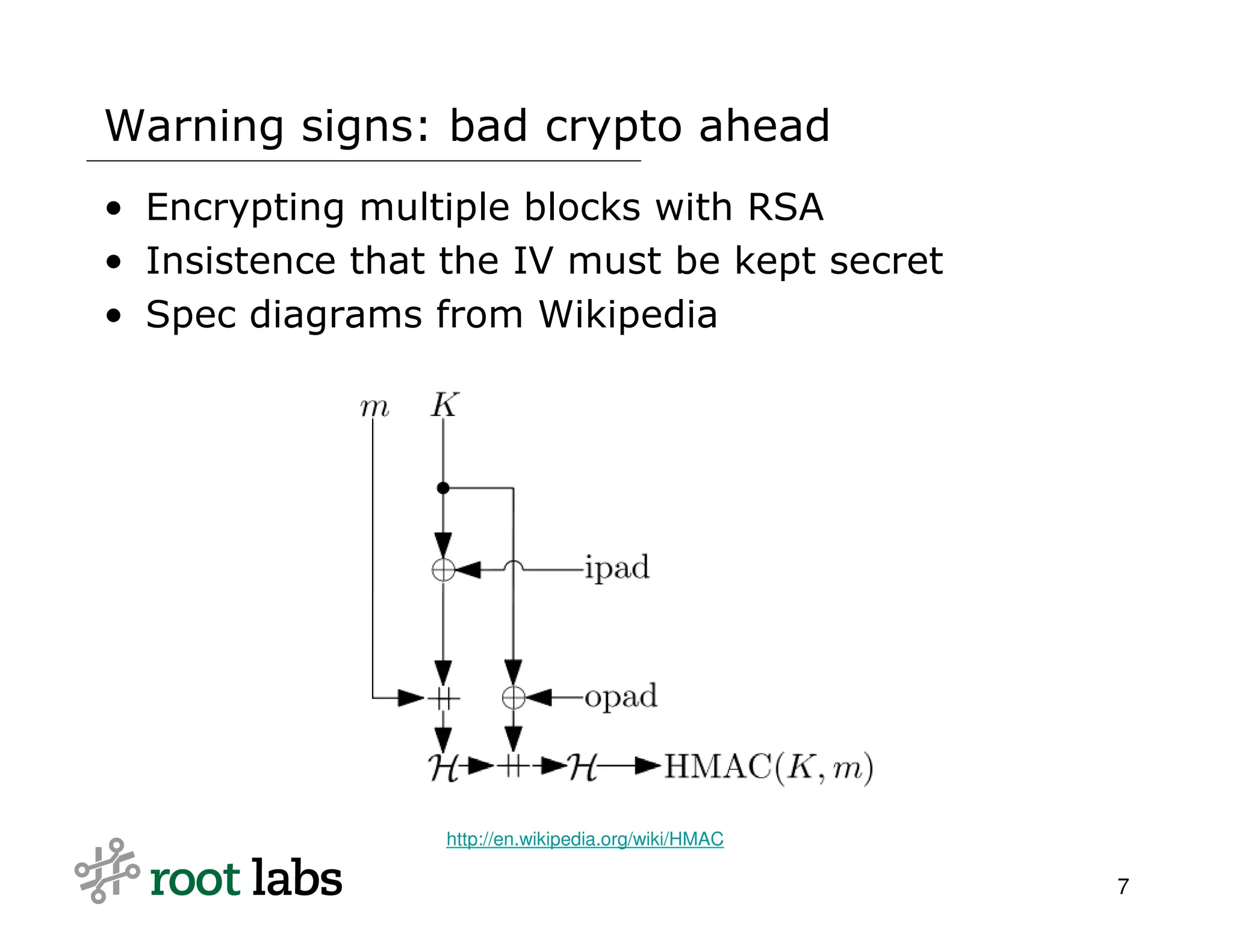





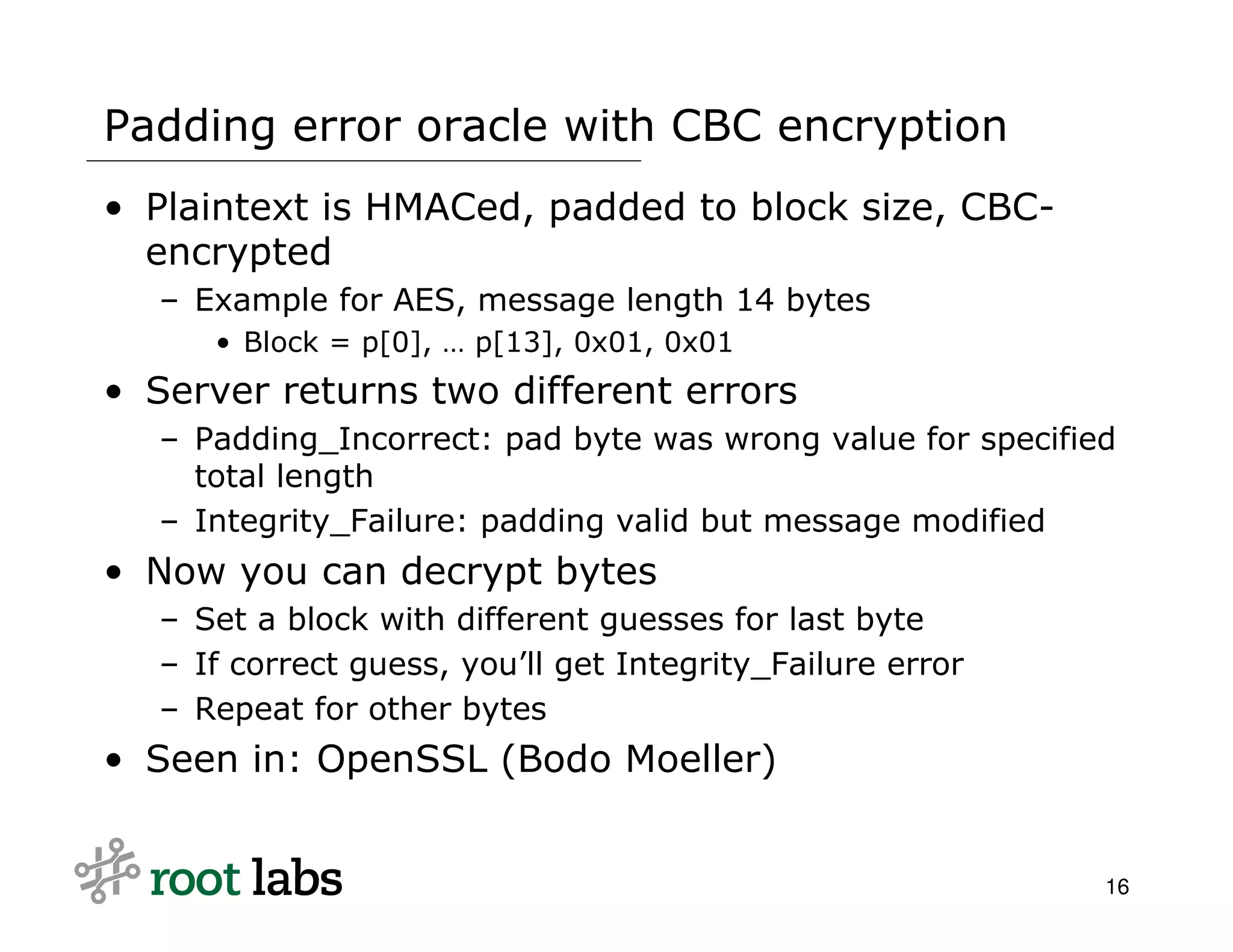



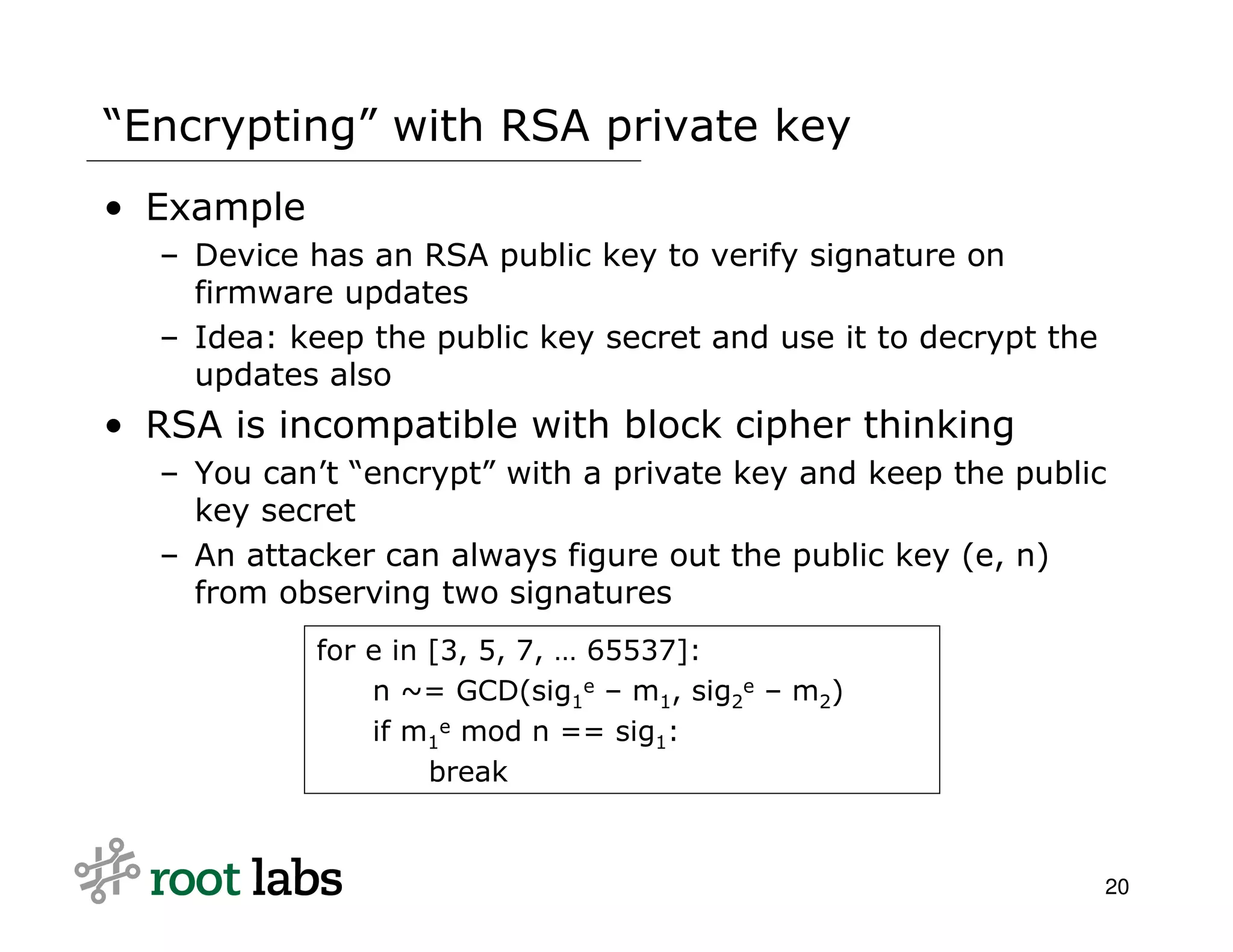
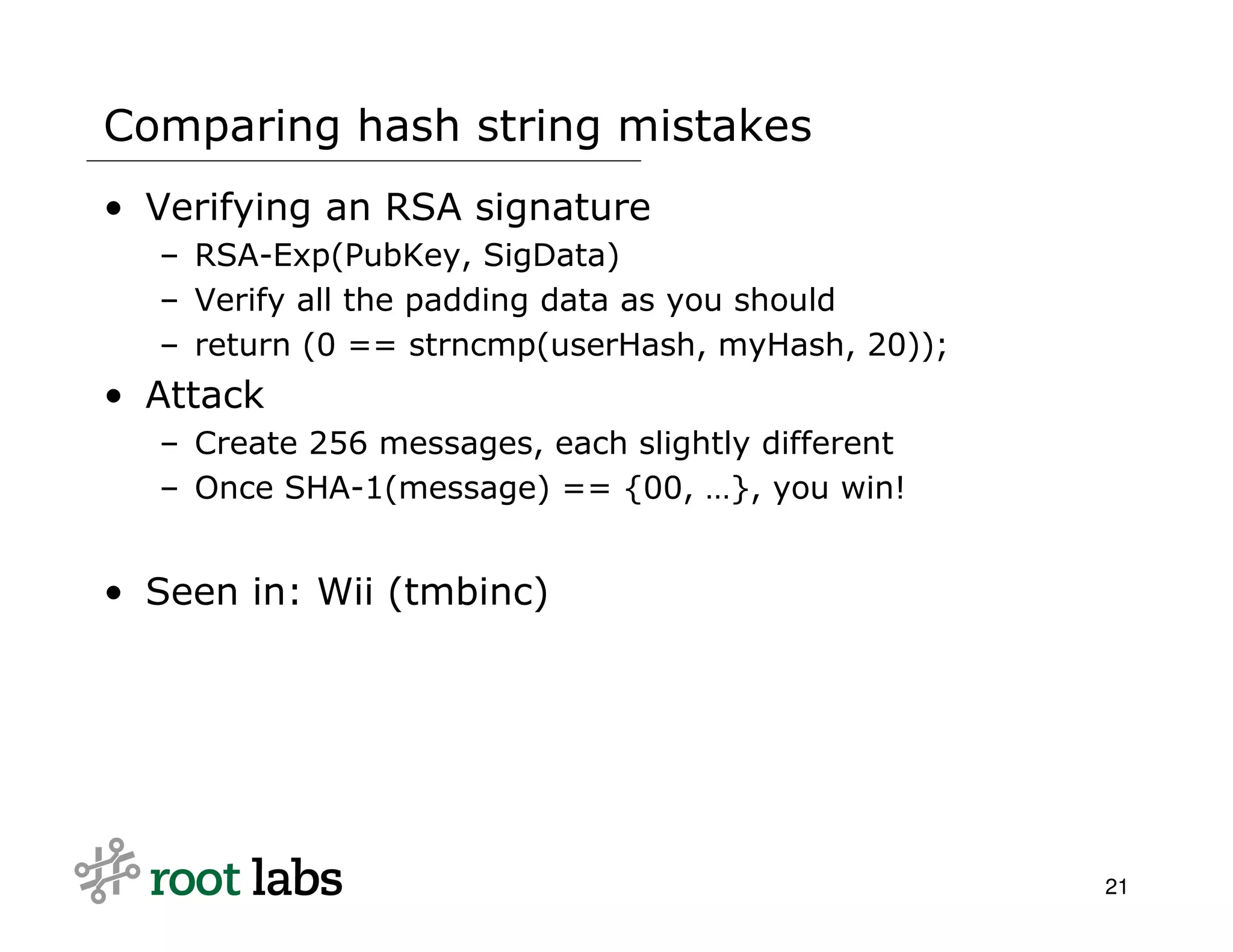
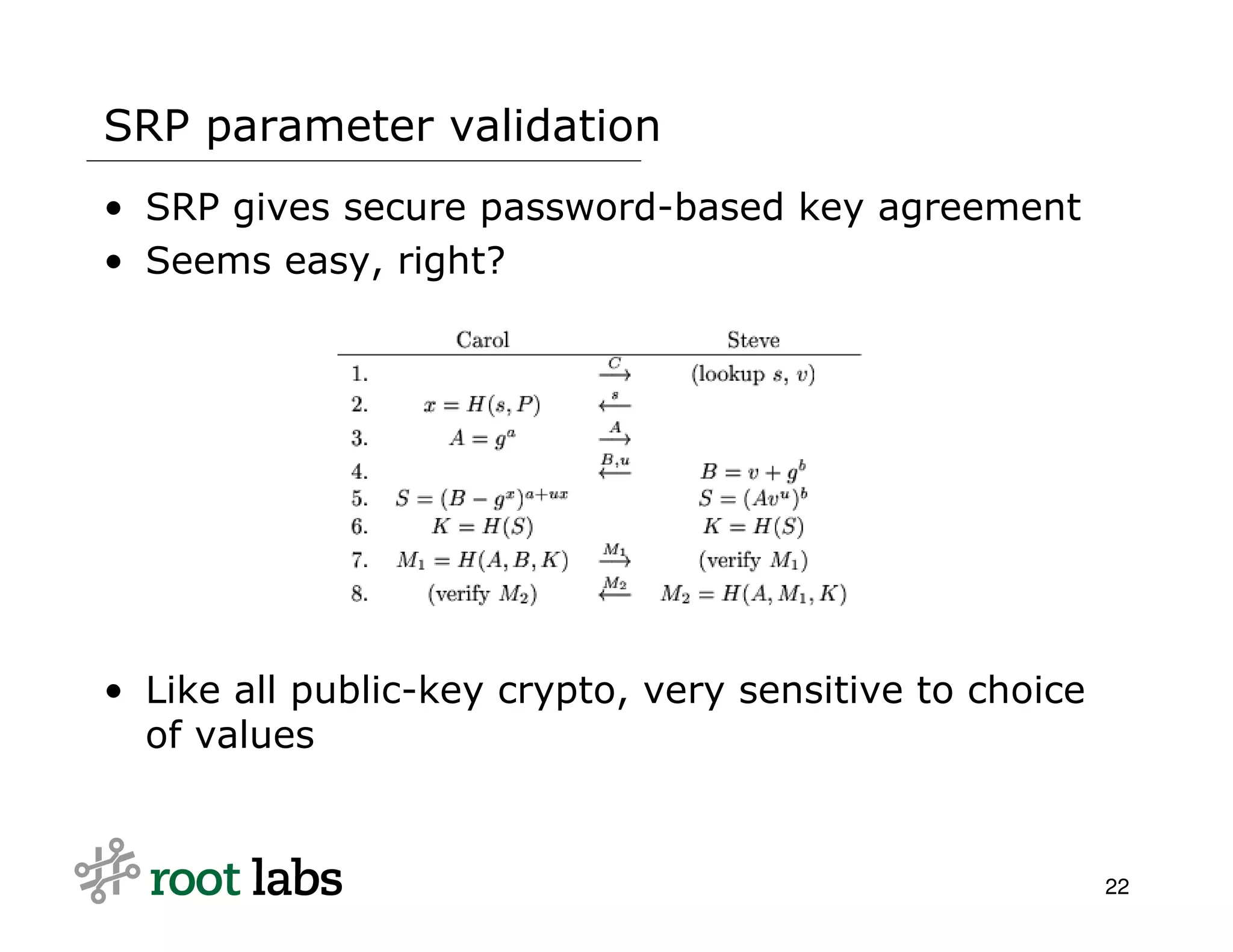
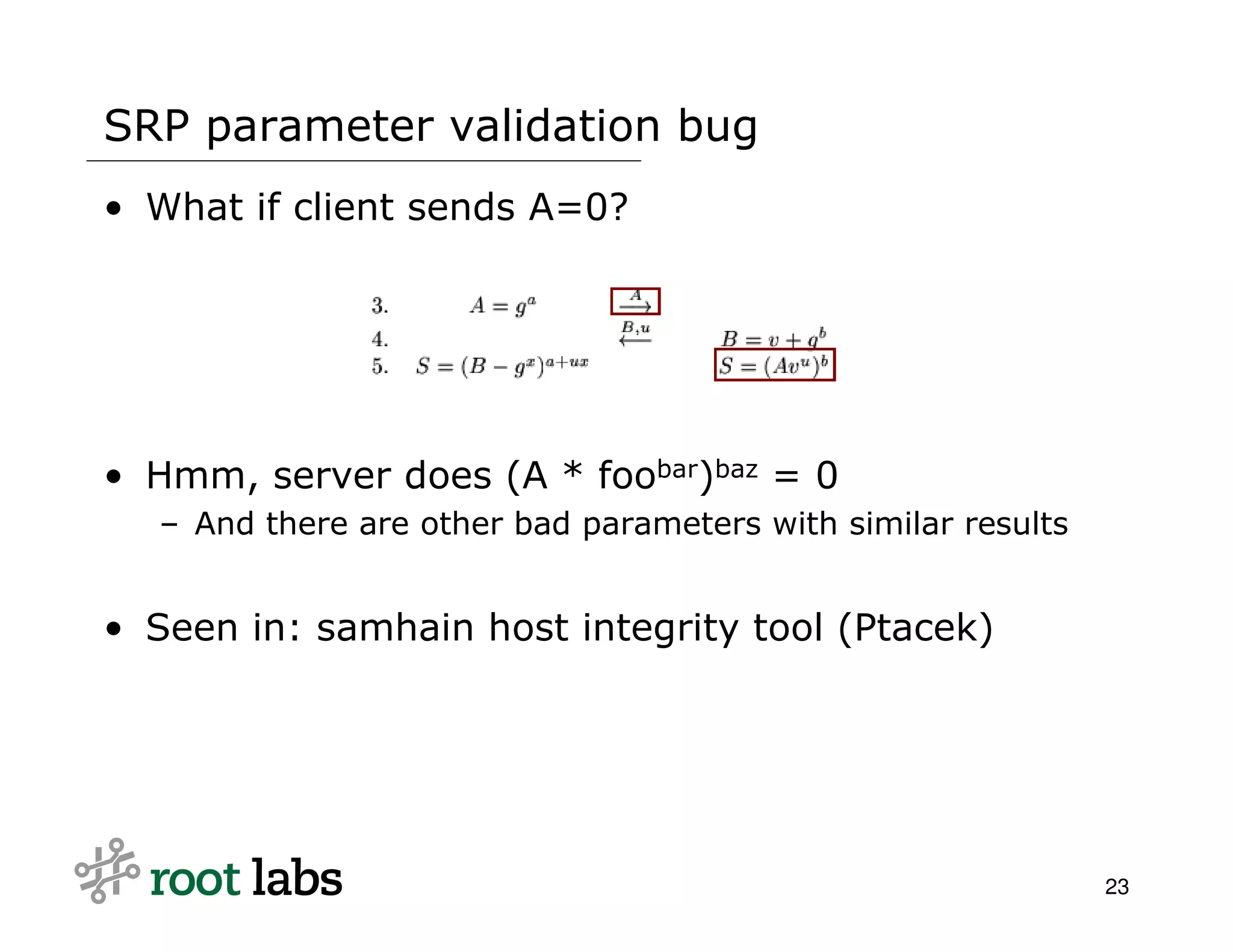



The document discusses the risks and complexities of implementing cryptographic systems, emphasizing the importance of using established libraries and protocols like SSL and GPG to avoid common pitfalls. It highlights various vulnerabilities and warning signs associated with poor cryptographic practices, as well as the necessity for thorough review and validation of cryptographic code. The author advises against designing custom cryptography, advocating instead for high-level libraries and third-party reviews to ensure security.

























