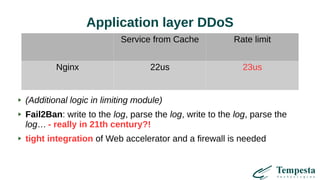
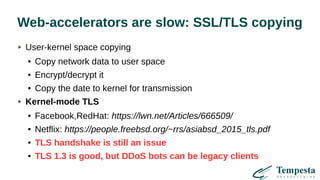
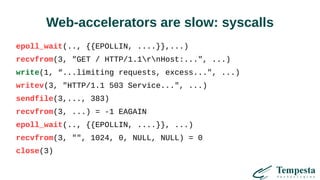
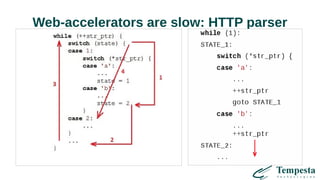
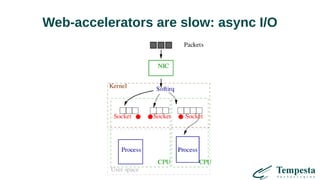
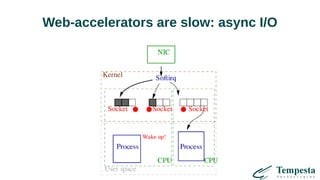
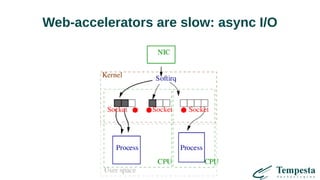
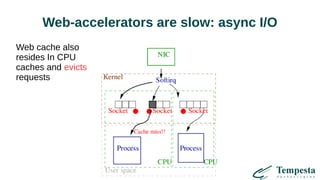
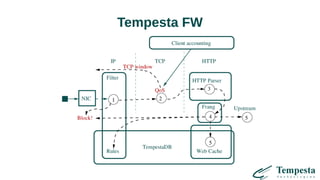
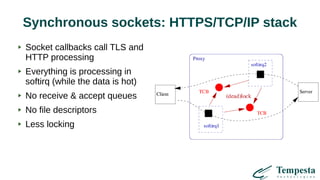
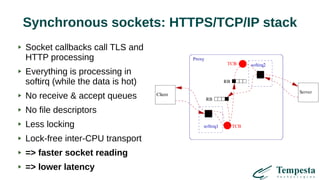
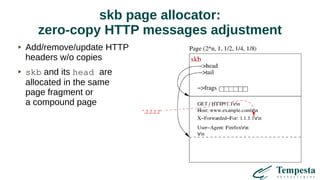
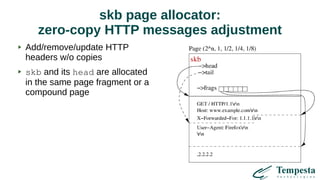
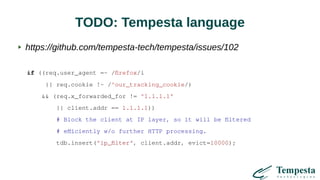
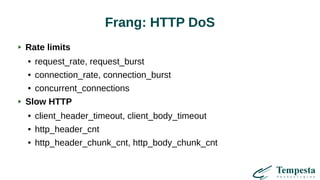
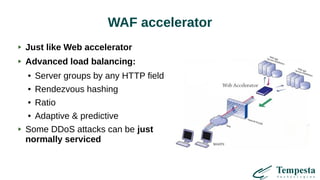
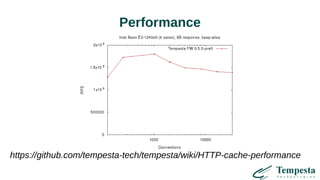
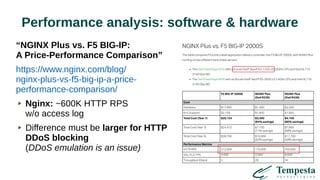
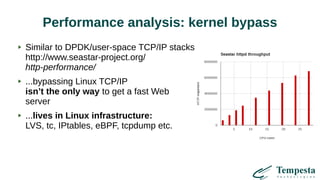
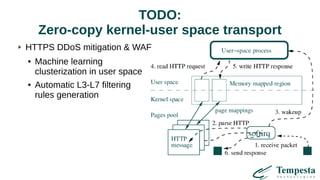
The document discusses HTTP DDoS mitigation strategies utilizing a kernel HTTPS/TCP/IP stack by Tempesta Technologies. It emphasizes the need for fast HTTP processing, advanced filtering, and tight integration between web accelerators and firewalls to effectively handle various DDoS attack vectors. Furthermore, it highlights challenges with traditional web accelerators and proposes kernel-level enhancements to improve performance and mitigate DDoS threats more efficiently.