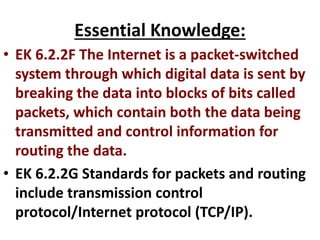
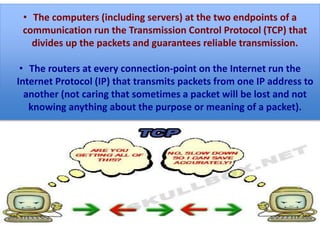
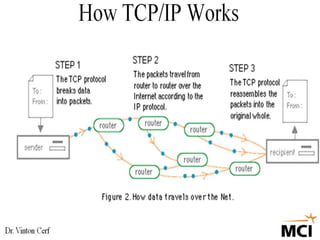
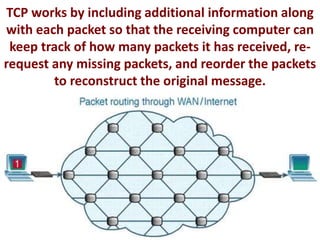
The document discusses how TCP guarantees reliable transmission of data over the internet. It explains that TCP breaks messages into packets and tracks which packets are received successfully, resending any lost packets and assembling the data in the right order. This allows communication to work reliably even though the underlying internet protocol (IP) is sometimes unreliable and packets can get lost. The document also mentions how TCP includes additional header information with each packet to help the receiver reconstruct the original message properly.




![Learning Objectives:
1. LO 6.1.1 Explain the abstractions in the
Internet and how the Internet functions.
[P3]
2. LO 6.2.1 Explain characteristics of the
Internet and the systems built on it. [P5]
3. LO 6.2.2 Explain how the characteristics of
the Internet influence the systems built on
it. [P4]](https://image.slidesharecdn.com/lesson4-170217164523/85/Lesson4-9-c-u4l3-tcp-transmission-control-protocol-11-320.jpg)