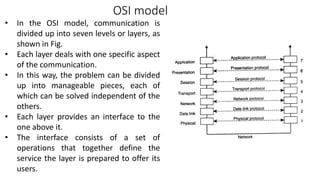
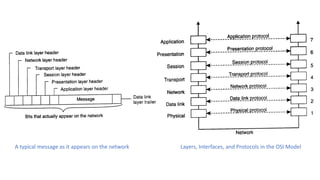
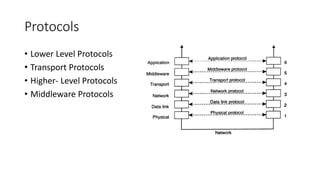
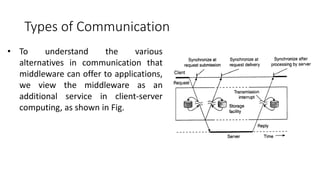
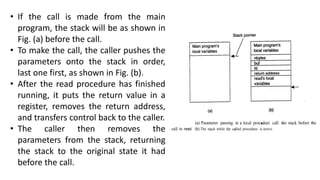
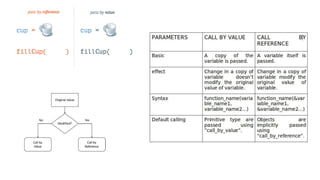
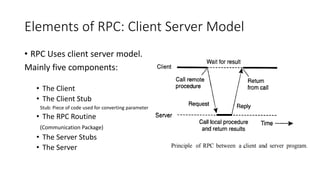
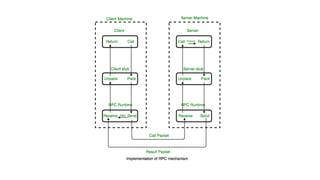
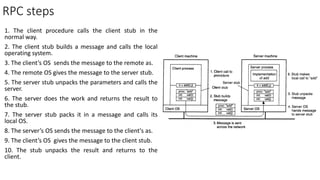
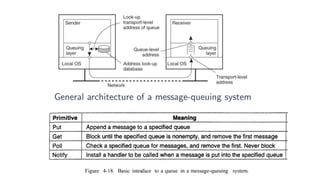
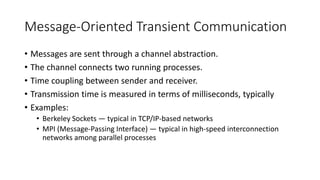
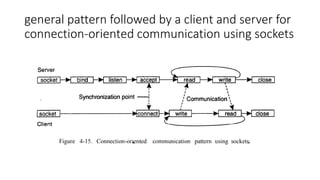
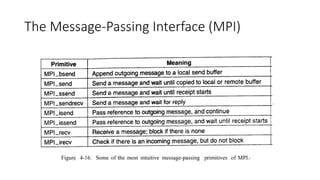
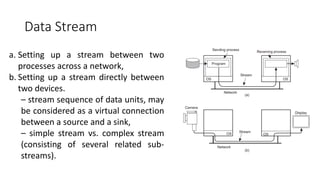
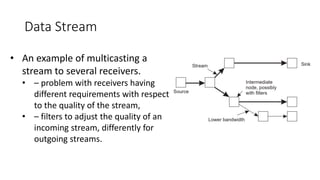
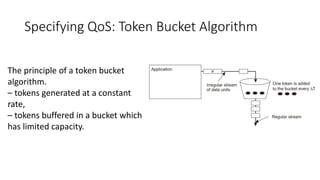
This document provides an overview of communication in distributed systems. It discusses various communication models including remote procedure call, message-oriented middleware, and data streaming. It also covers fundamental communication concepts like protocols, layers in the OSI model, and widely-used protocols at each layer like TCP/IP. The document examines both connection-oriented and connectionless protocols and how communication works at the physical, data link, network, transport, and application layers.