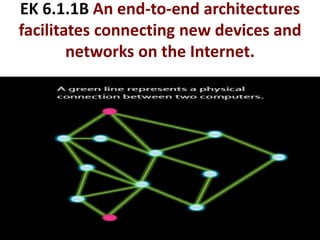
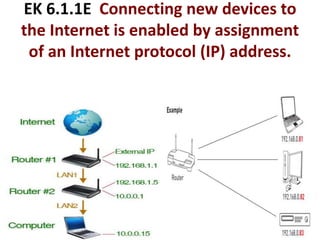
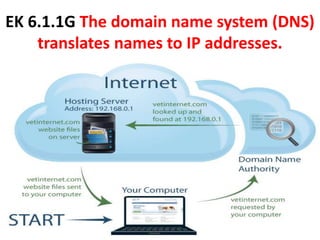
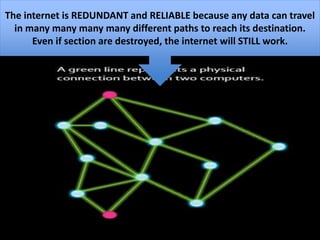
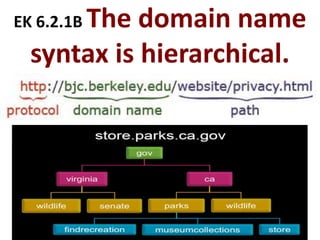
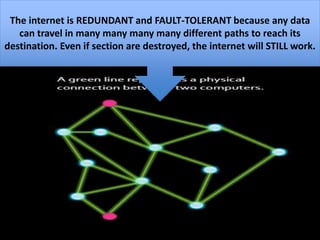
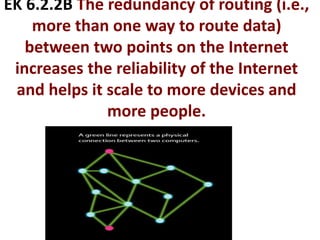
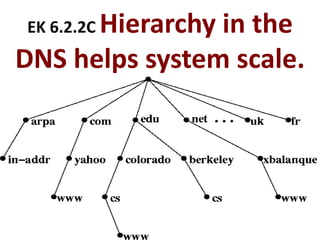
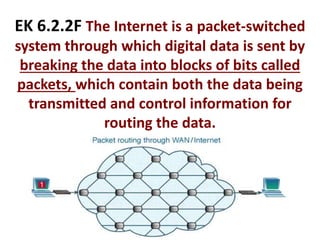
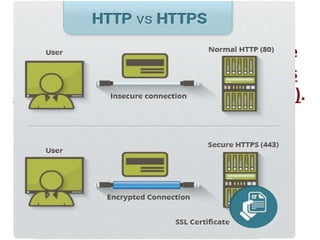
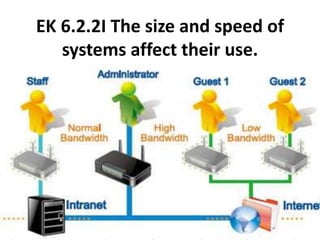
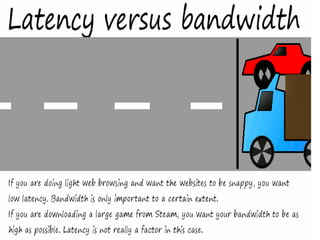
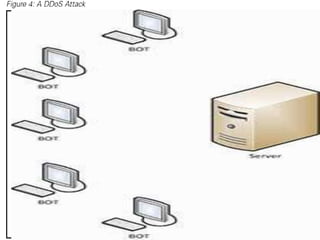
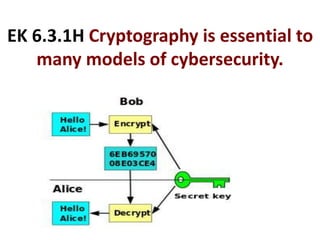
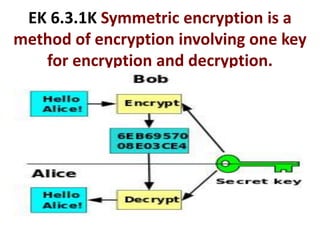
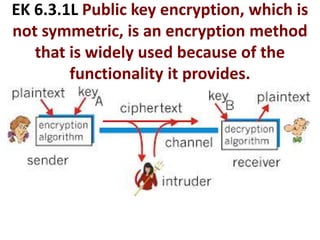
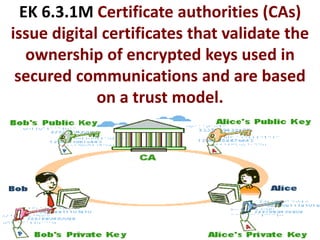
The document provides an overview of key concepts related to the internet. It discusses how the internet connects devices globally using an end-to-end architecture. Devices connect and communicate using IP addresses and protocols. Standards like HTTP, IP, and SMTP are developed by the Internet Engineering Task Force. The internet has a hierarchical and redundant structure which allows data to reach its destination along multiple paths, increasing reliability. This hierarchy and redundancy helps the internet scale to support more devices. The document also discusses security and trust issues on the internet like DDoS attacks, viruses, cryptography, and the role of certificate authorities.