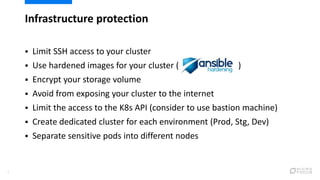
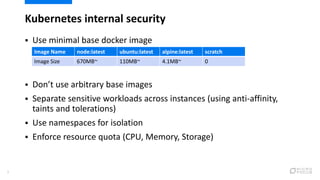
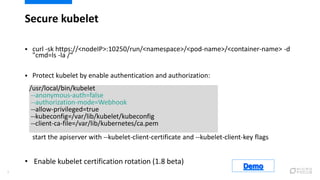
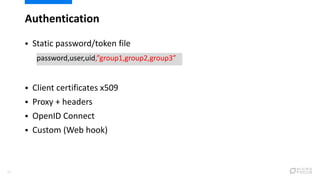
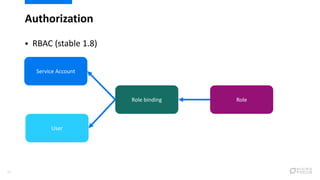
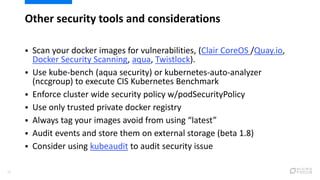
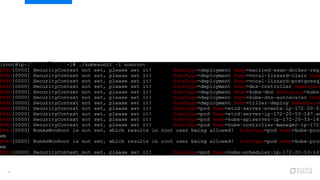
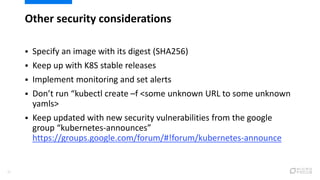
This document provides an overview of best practices for securing Kubernetes clusters. It discusses infrastructure protection, Kubernetes internal security, authentication and authorization options, network security, secrets management, container runtime security, and other security tools. Specific recommendations include limiting SSH access, using hardened images, encrypting storage, restricting API access, separating workloads, enabling authentication, implementing role-based access control, using network policies, securely managing secrets, scanning images for vulnerabilities, and auditing events.









![17
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: read-pods
namespace: default
subjects:
- kind: User
name: Bob
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: Role
name: pod-reader
apiGroup: rbac.authorization.k8s.io
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: default
name: pod-reader
rules:
- apiGroups: [""]
group
resources: ["pods"]
verbs: ["get", "watch", "list"]](https://image.slidesharecdn.com/finaldisp-180110085121/85/K8s-security-best-practices-17-320.jpg)









![Thanks and credit
39
My Wife
All K8s contributors
Hacking and Hardening Kubernetes Clusters by Example [I] - Brad Geesaman -
https://goo.gl/komeXN
Running containers securely with Google Container Engine, Alex Mohr and
Jessica Frazelle - https://goo.gl/AFhTyp
Shipping in Pirate-Infested Waters: Practical Attack and Defense in Kubernetes
[A] - Greg Castle - https://goo.gl/WFDrrv
Compliance and Identity Management in Kubernetes [I] Marc Boorshtein -
https://goo.gl/Jf7Rkh
Securing K8s Microservices with Calico Network Policies, Vadim Solvey -
https://goo.gl/rWGGXM](https://image.slidesharecdn.com/finaldisp-180110085121/85/K8s-security-best-practices-39-320.jpg)