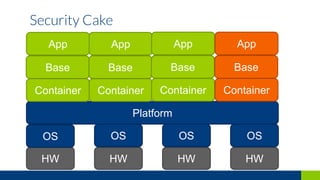
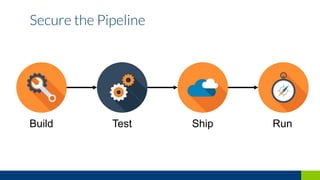
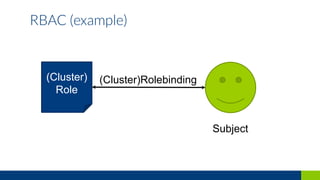
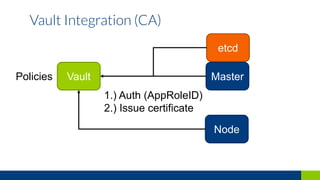
This document discusses how to secure a Kubernetes platform. It covers setting up authentication and authorization using RBAC and certificates. It also discusses implementing network policies and pod security policies to restrict traffic and resources. Additional topics include integrating Vault for secrets management and using admission controllers and auditing to intercept and modify API requests for security purposes.