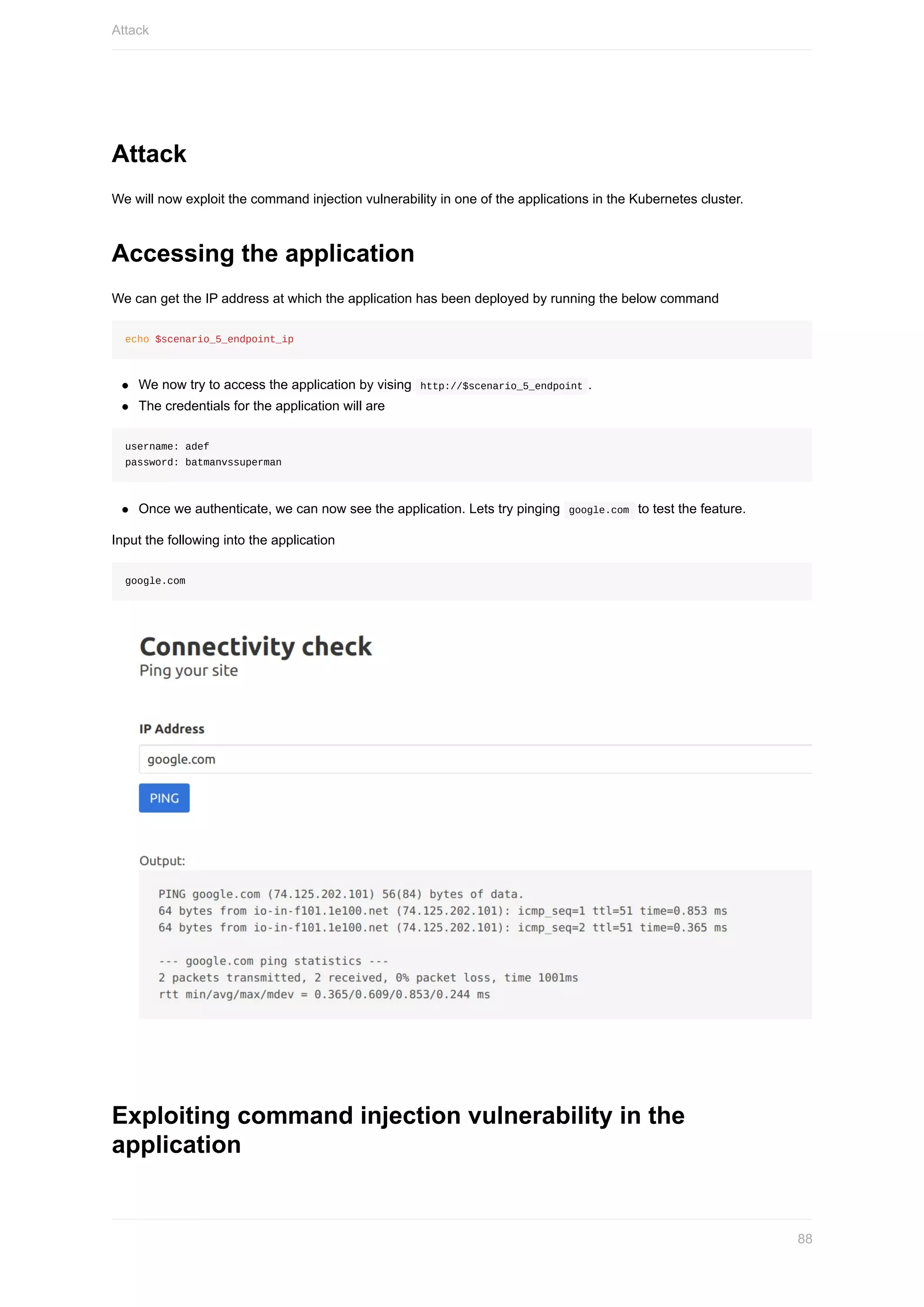
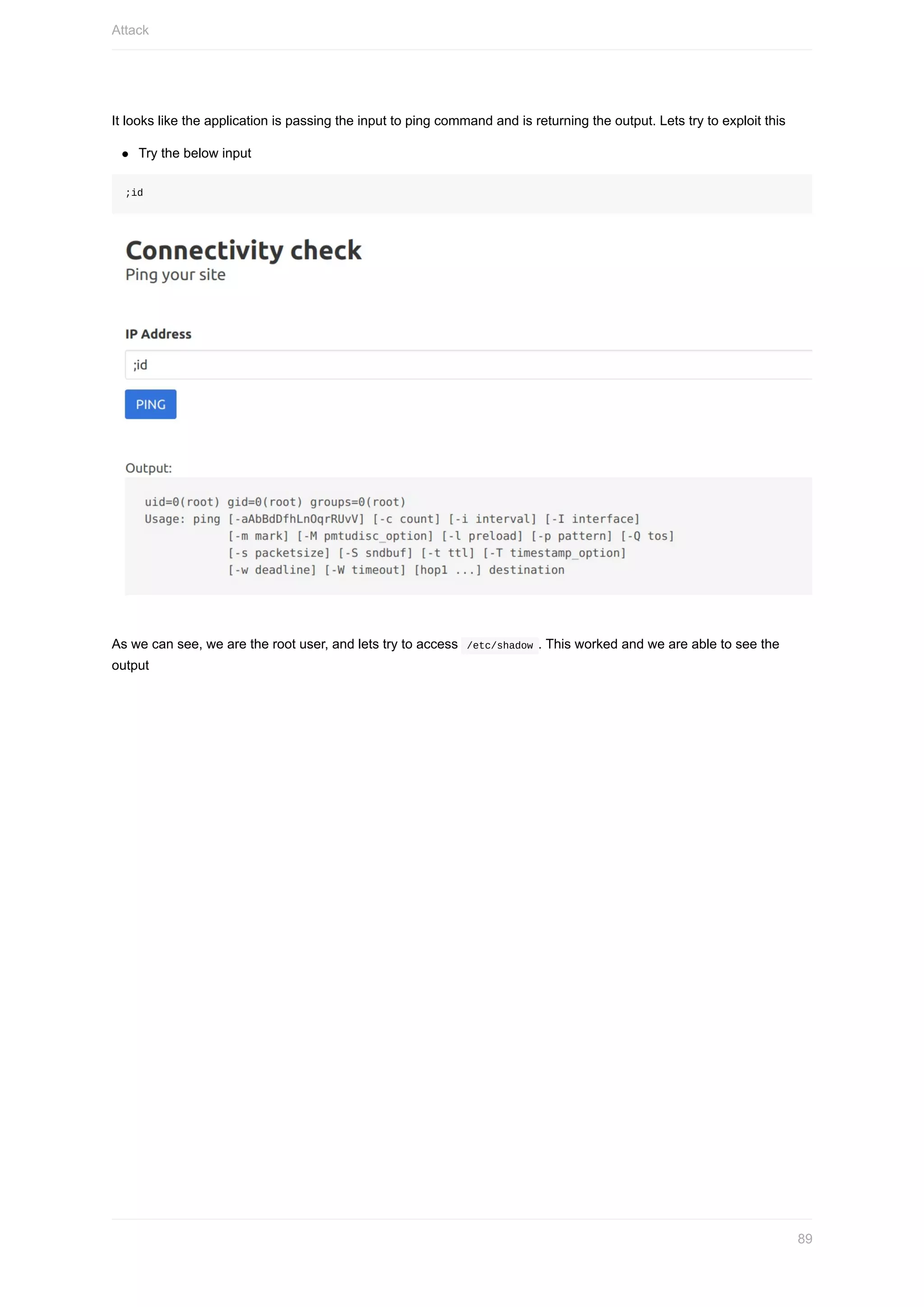
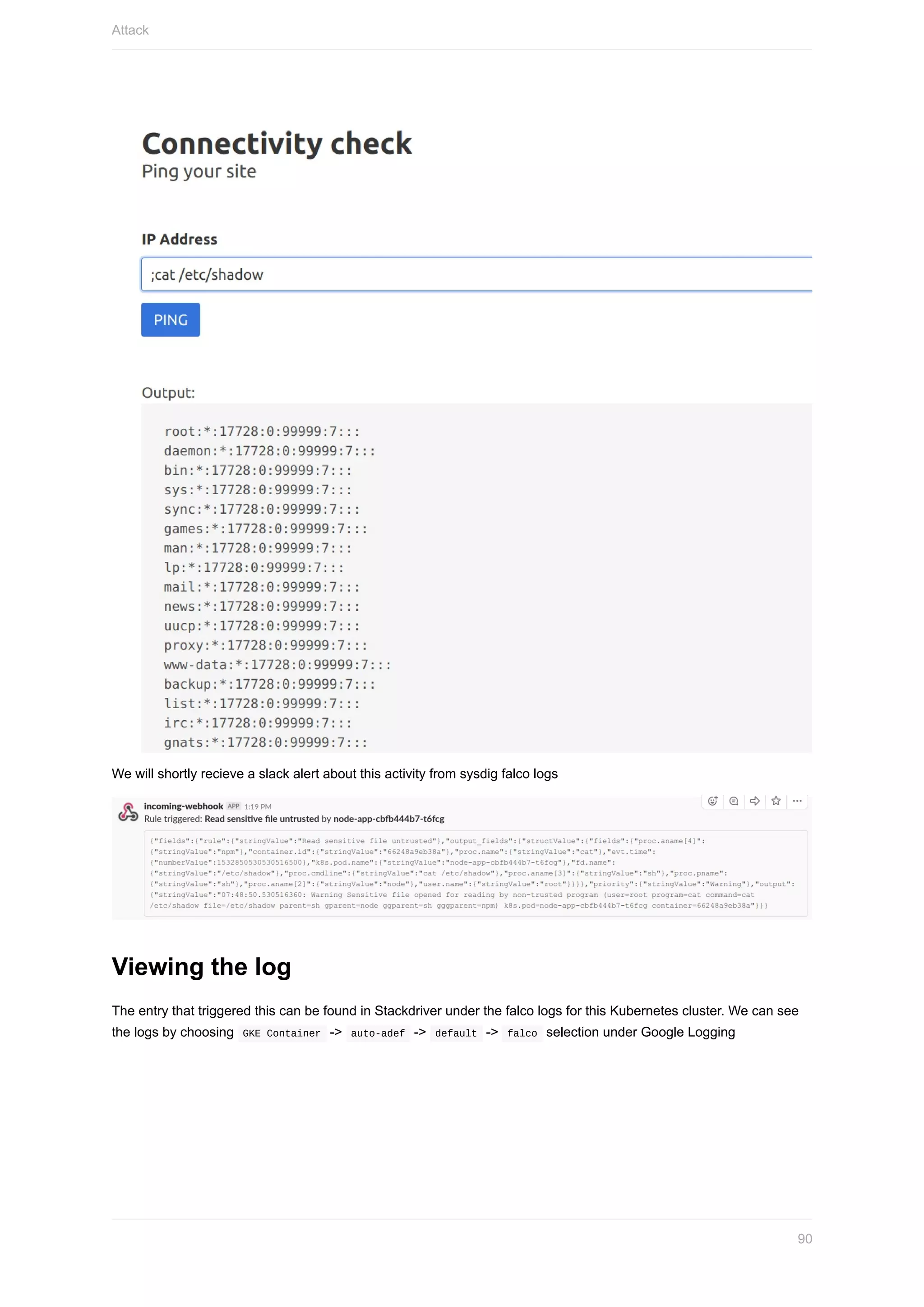
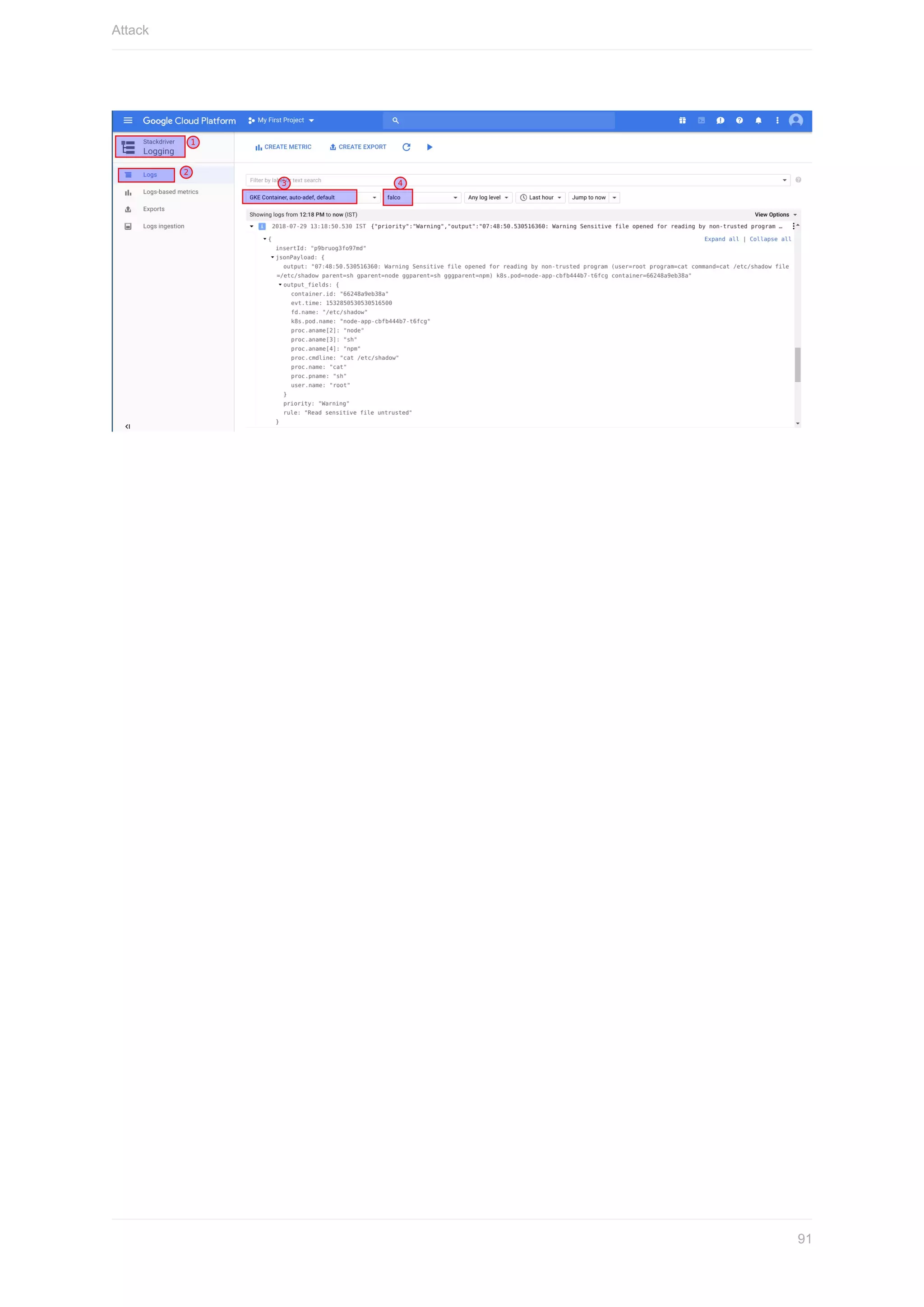
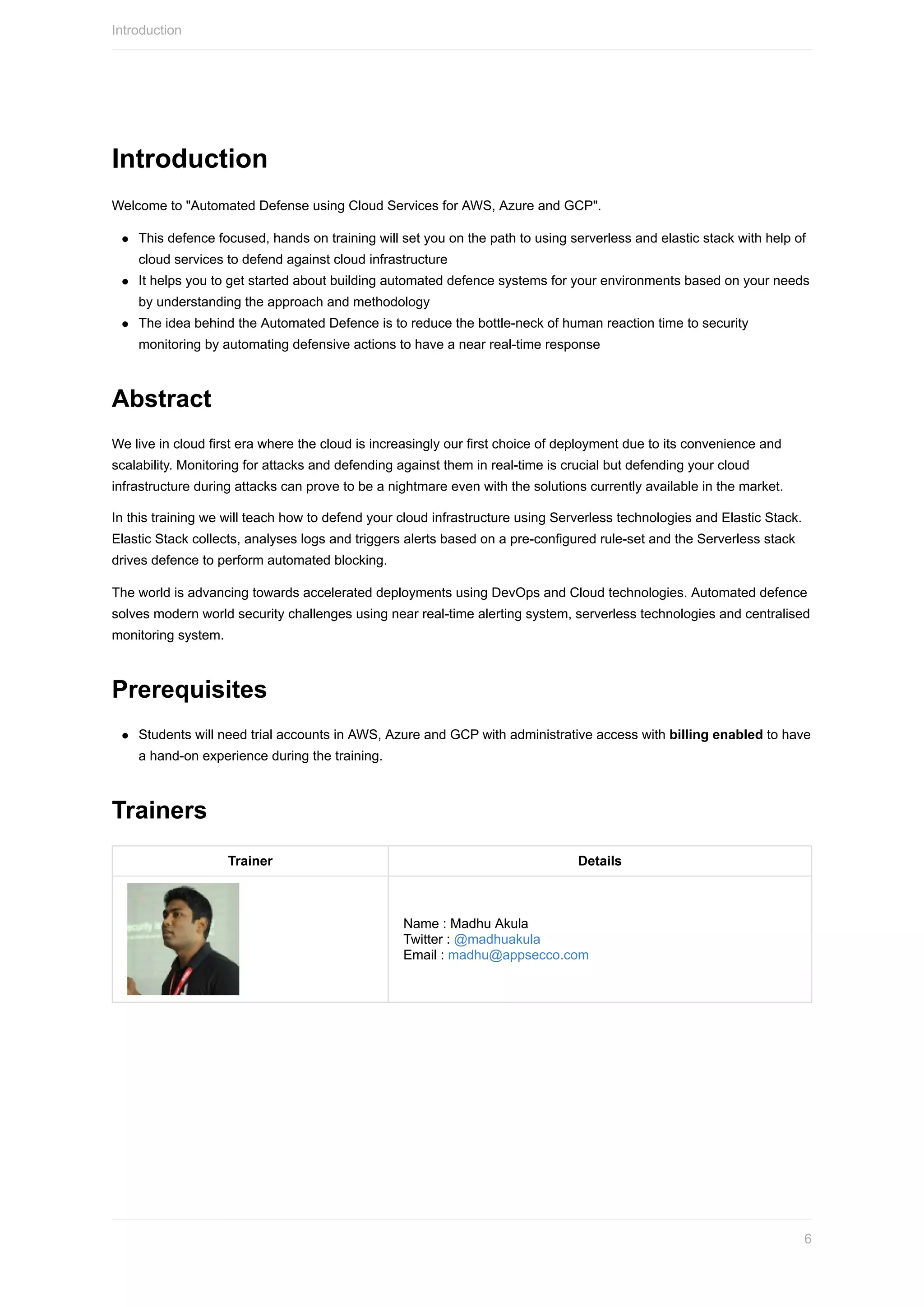
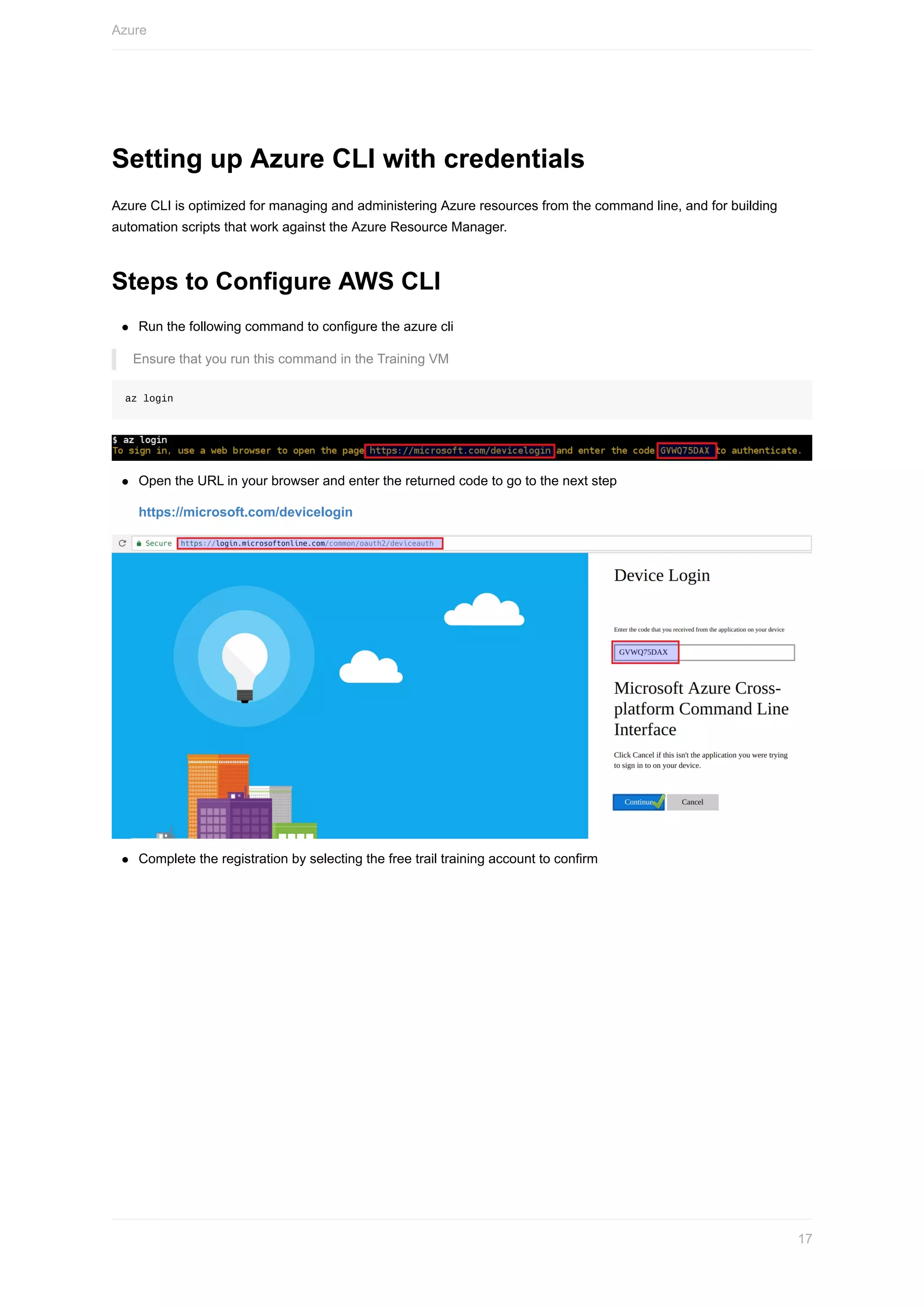
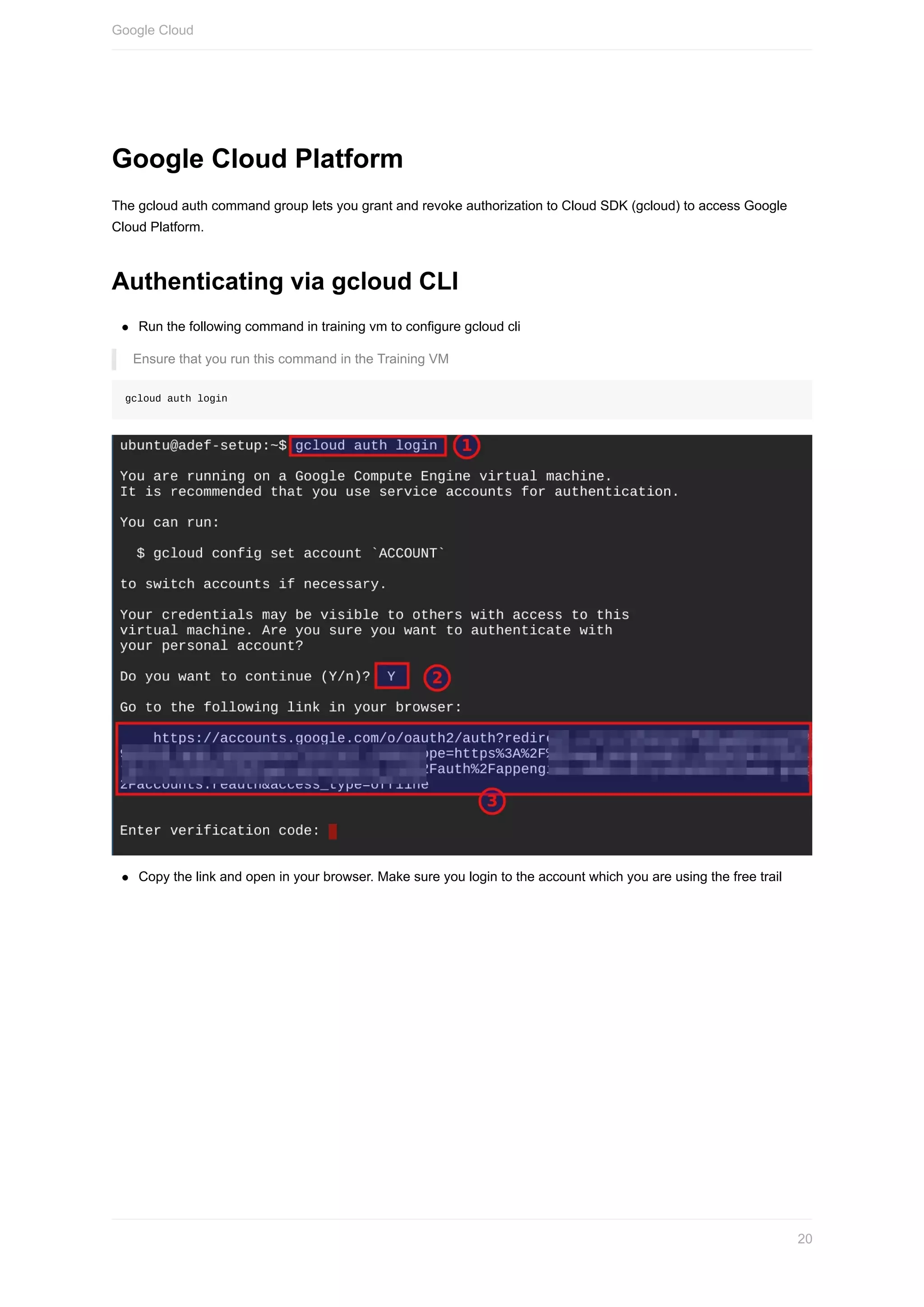
Here are the steps to set up the Azure CLI:
1. Install the Azure CLI using pip:
```
pip install azure-cli
```
2. Log in to your Azure account:
```
az login
```
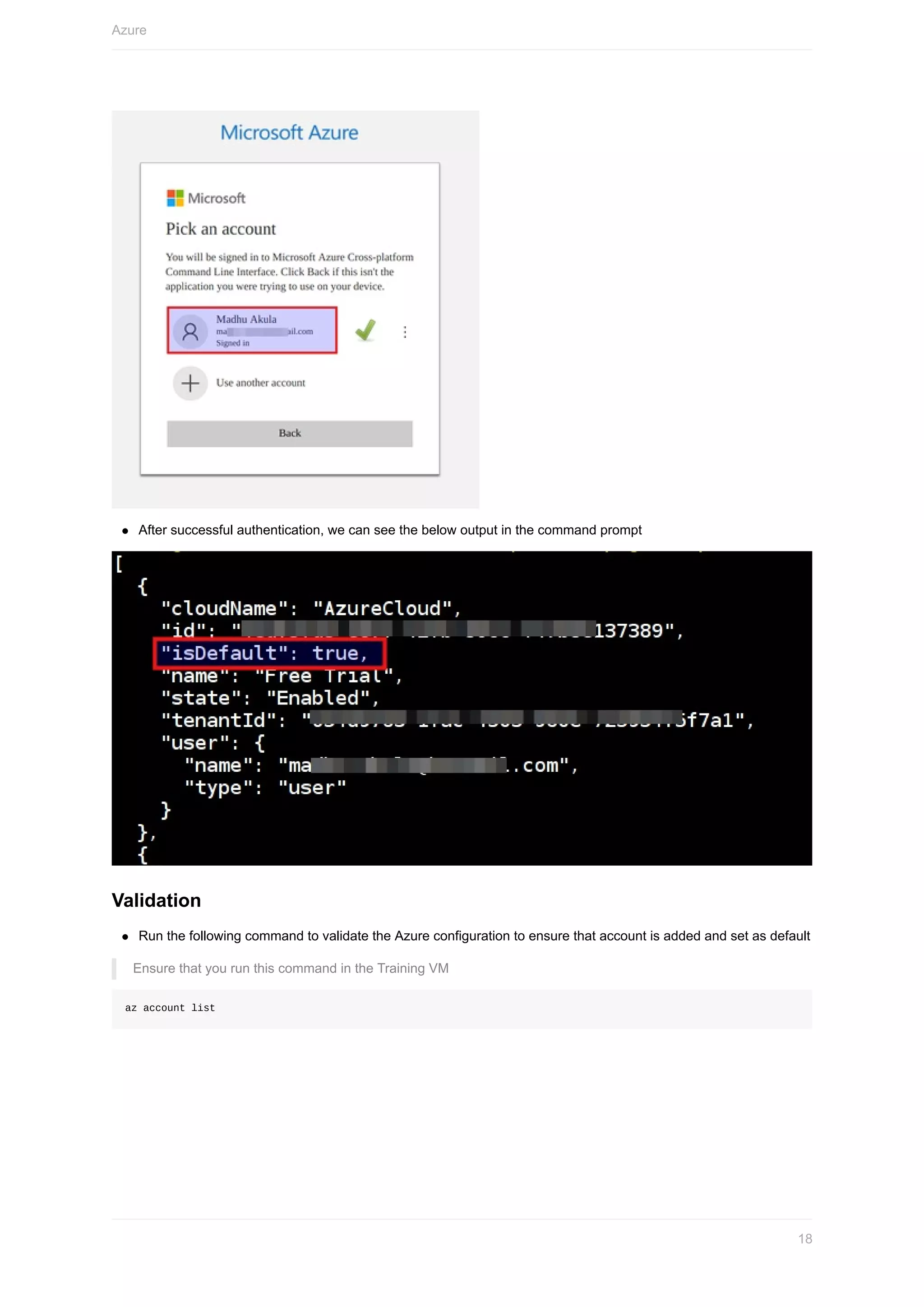
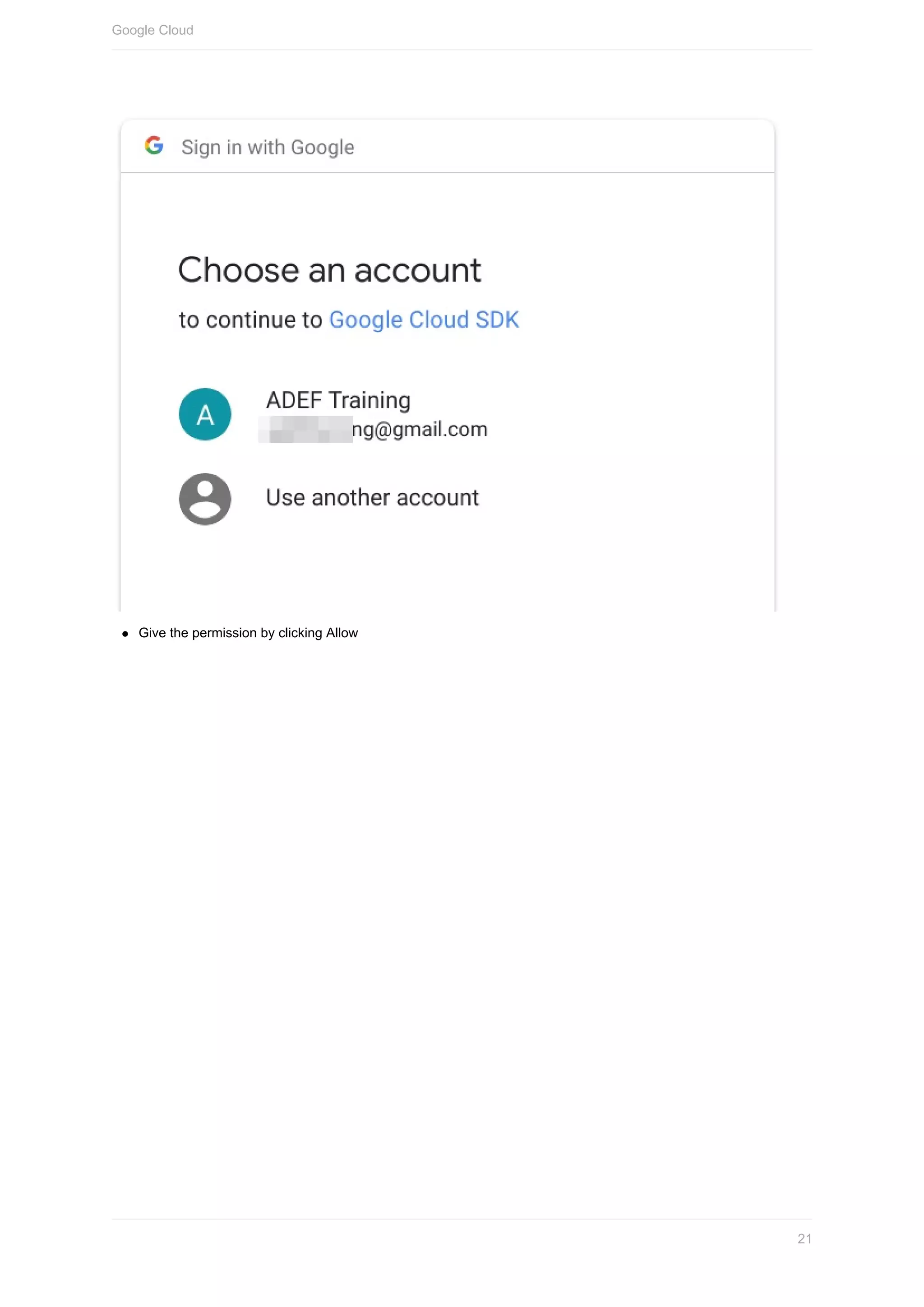
3. Follow the prompts to log in through a browser and authenticate with your credentials.
4. Verify your login was successful by running:
```
az account show
```
5. You can now run Azure CLI commands to manage your Azure resources.
Some key points:
- The Azure CLI credentials are stored locally so you only need to log in once per session.
- You can have multiple subscriptions configured by running `az account




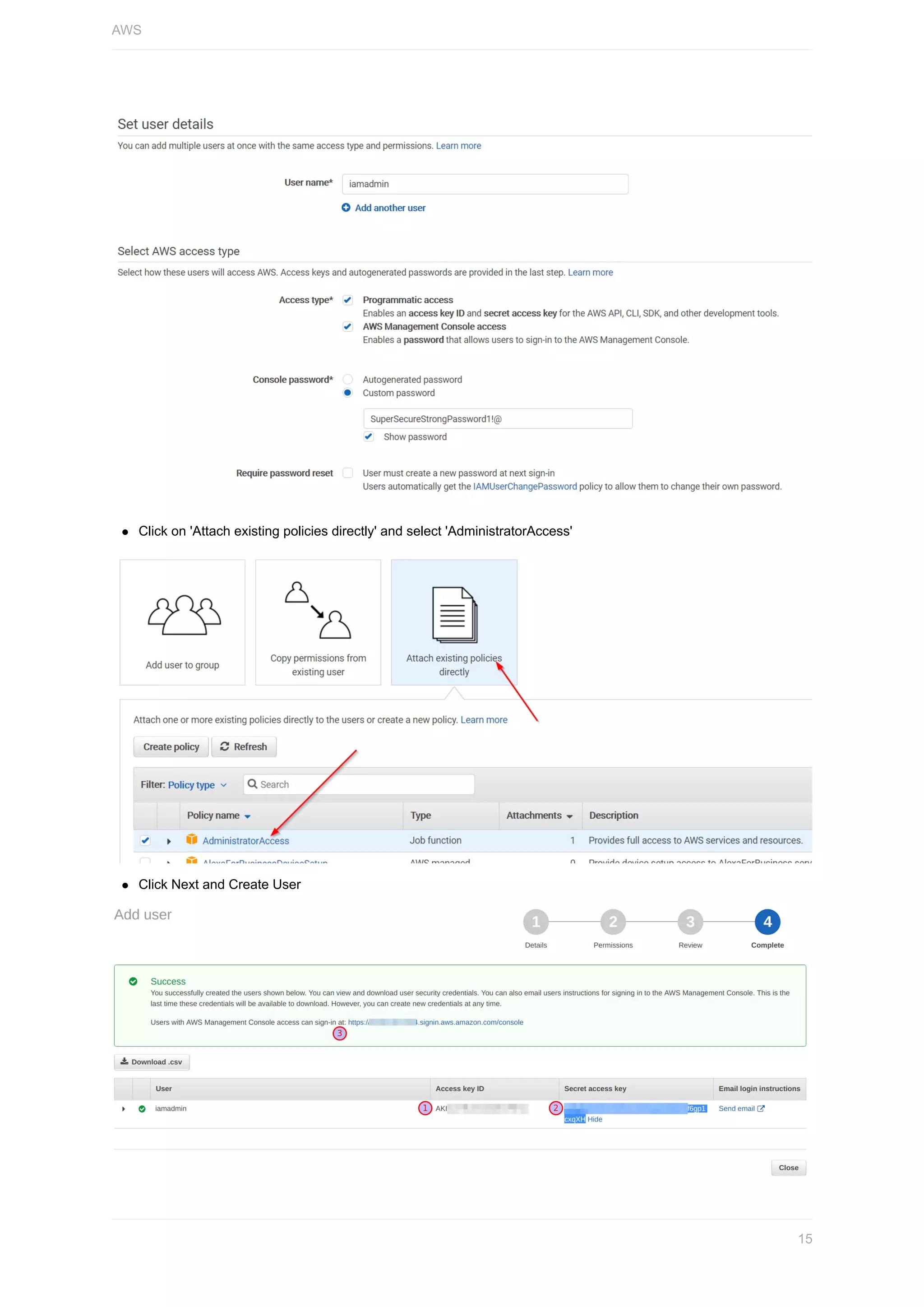
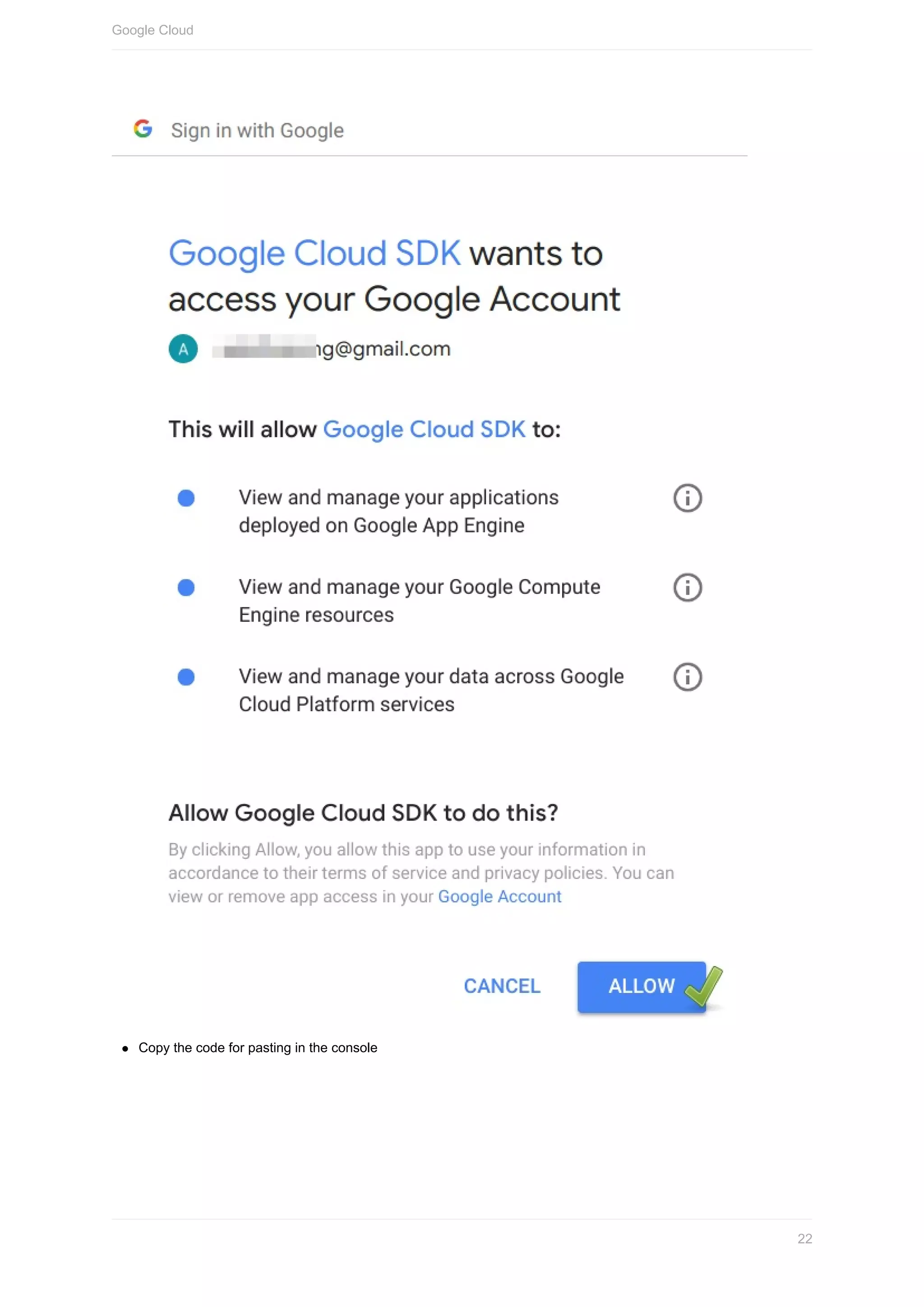
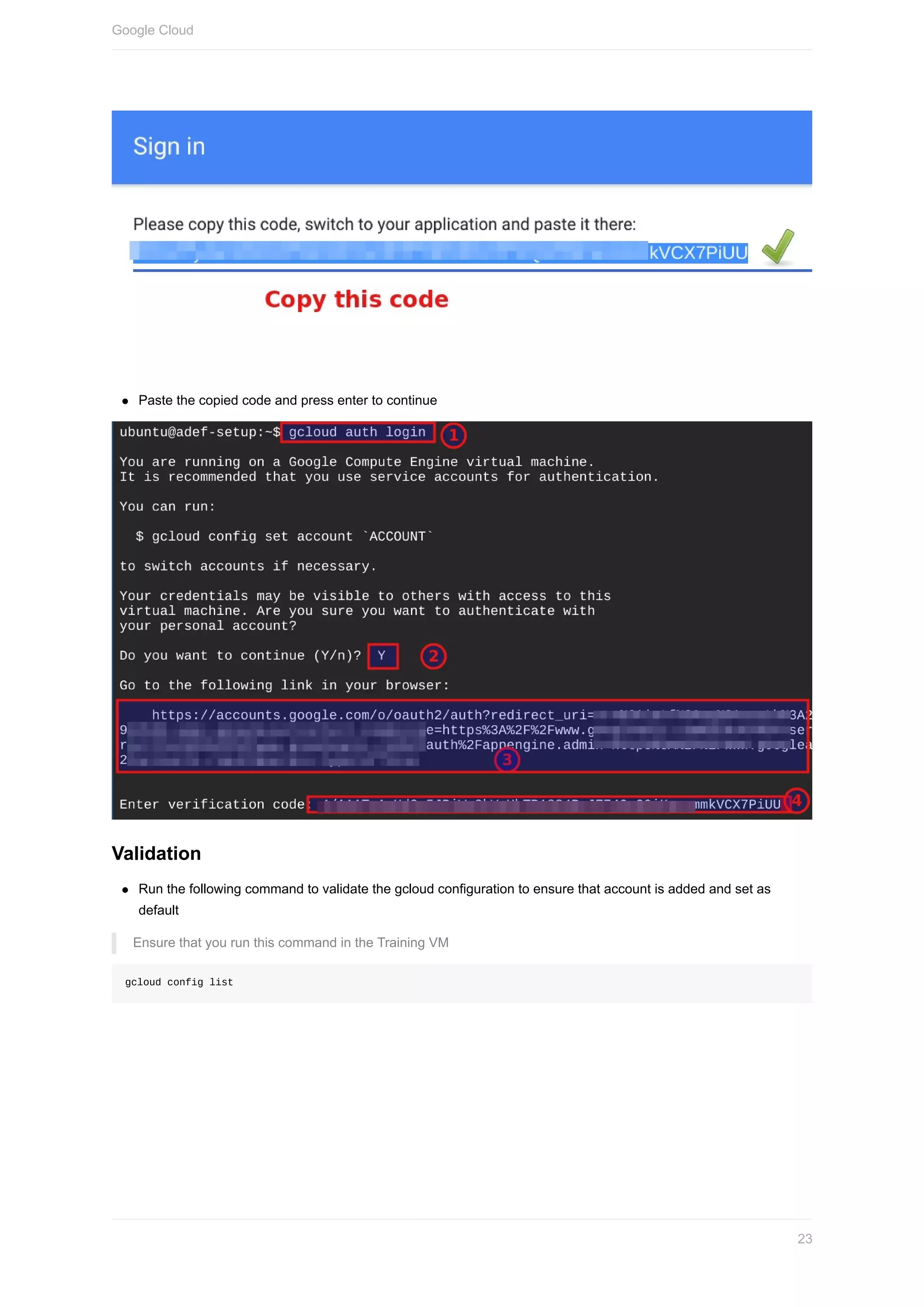
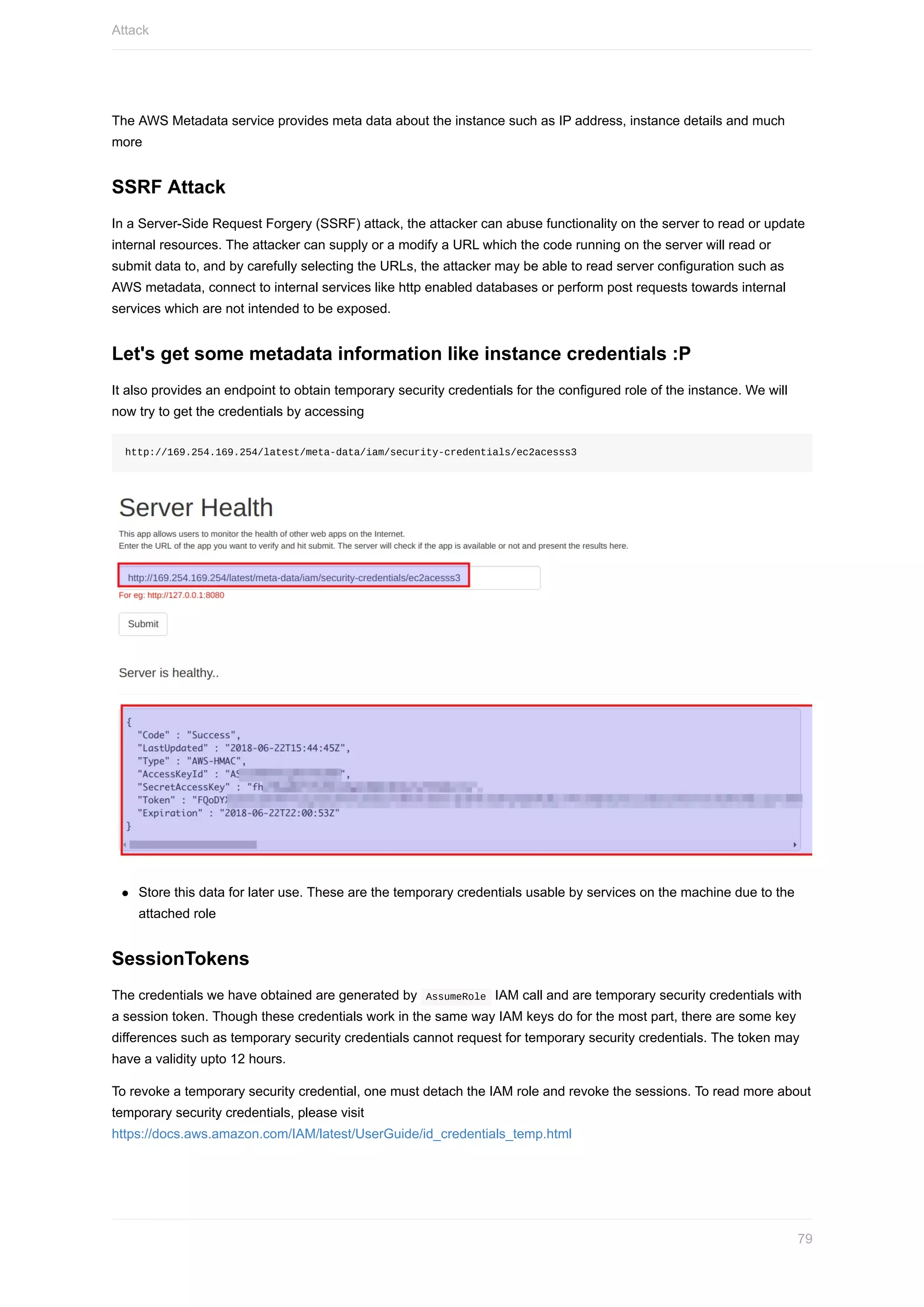
![Copy and save the following in your text editor for later use
1. Access key ID
2. Secret access key
3. Unique sign in URL (Bookmark this link)
Steps to Configure AWS CLI
Run the following command to configure the aws cli
Ensure that you run this command in the Training VM
aws configure
You will need to provide the access key ID and secret access key
Type the following values
Default region name [None]: us-east-1 (YOU MUST PROVIDE us-east-1 )
Default output format [None]: json
These credentials get stored at ~/.aws/credentials
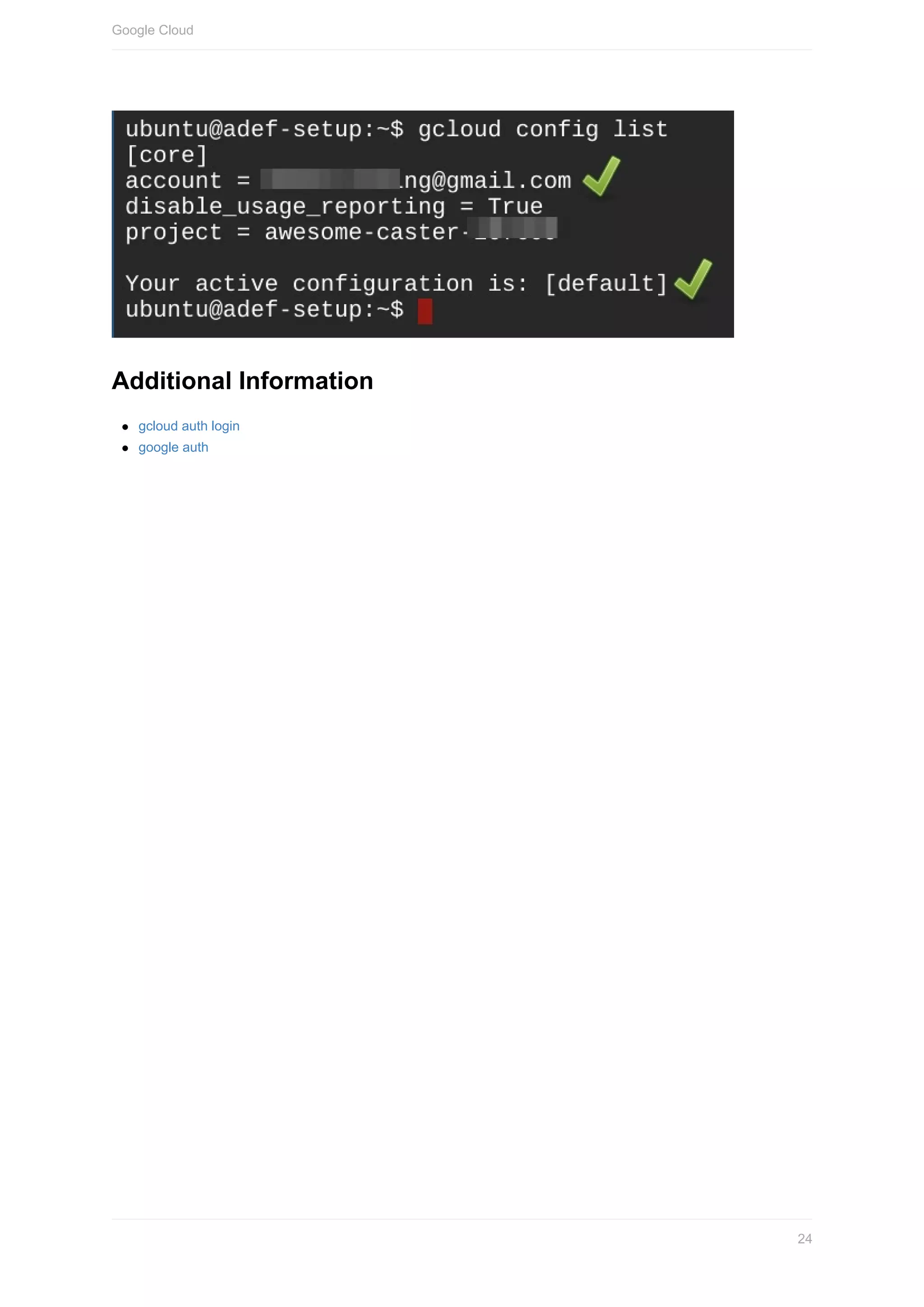
Validation
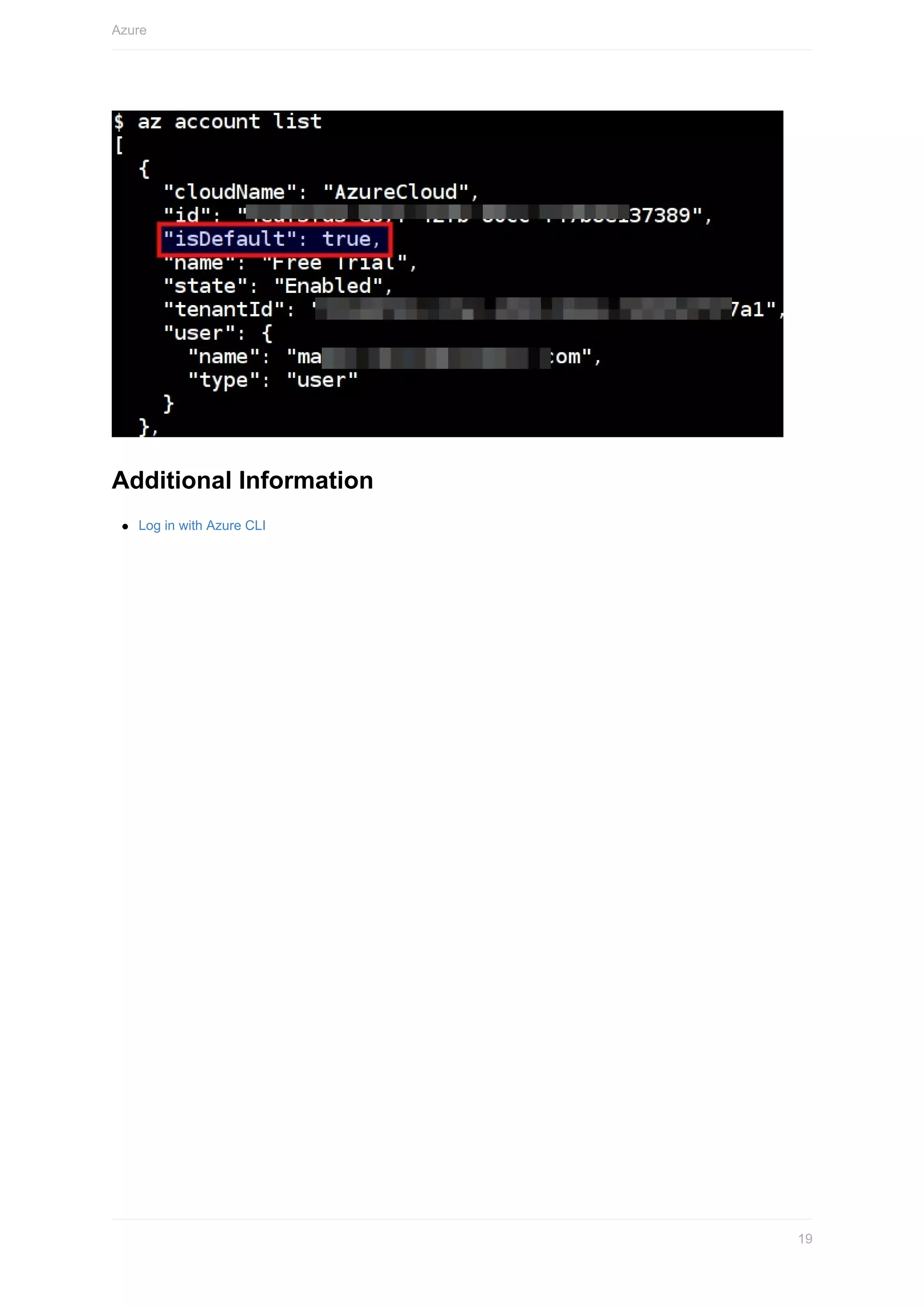
Run the following command to validate the AWS configuration to ensure that account is added and set as default
Ensure that you run this command in the Training VM
aws sts get-caller-identity
Additional Information
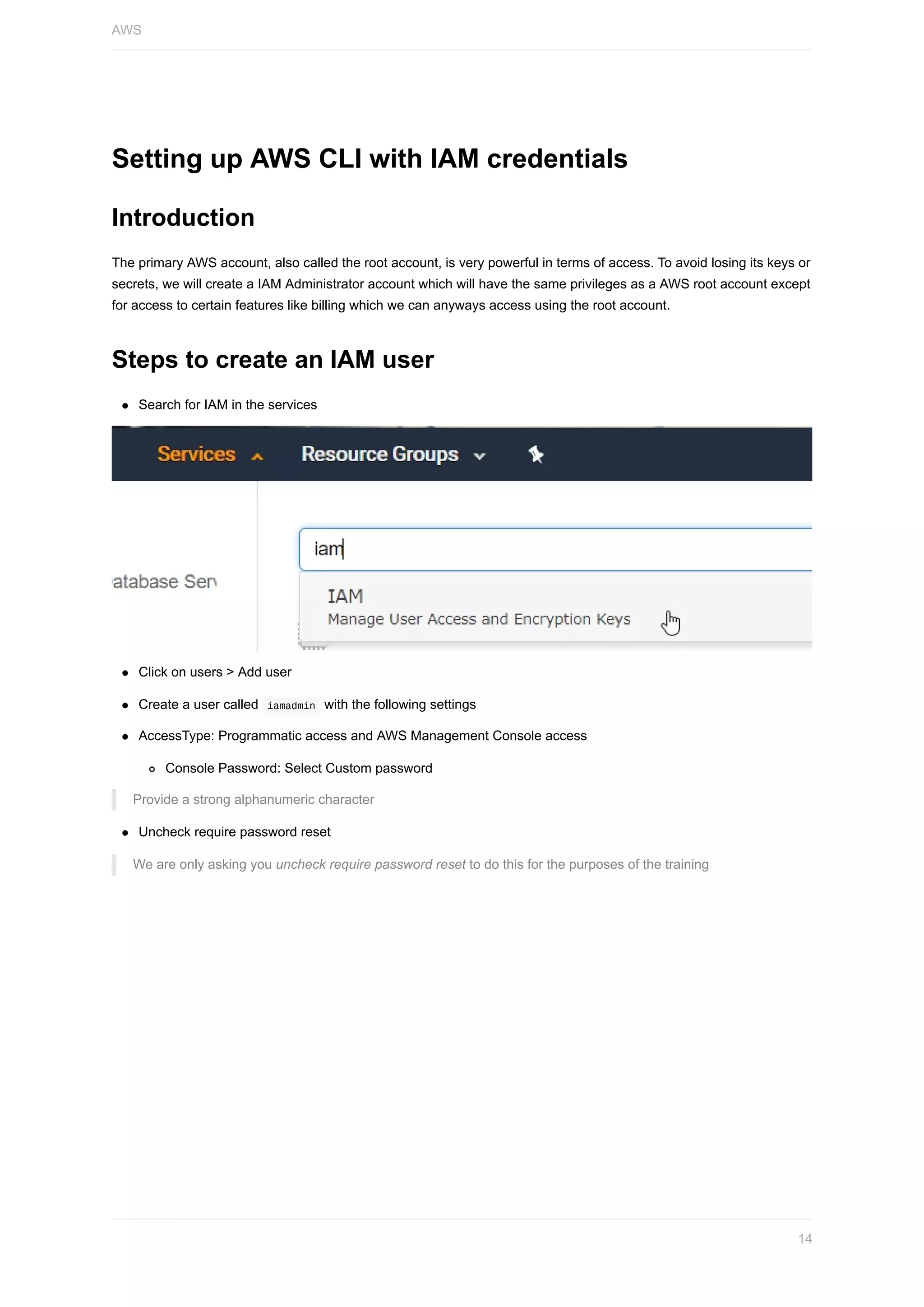
Setting up access using CLI
AWS
16](https://image.slidesharecdn.com/madhuakula-automateddefenseusingcloudserviceawsazuregcp-190227051351/75/SACON-Madhu-Akula-Automated-Defense-Using-Cloud-Service-Aws-Azure-Gcp-16-2048.jpg)



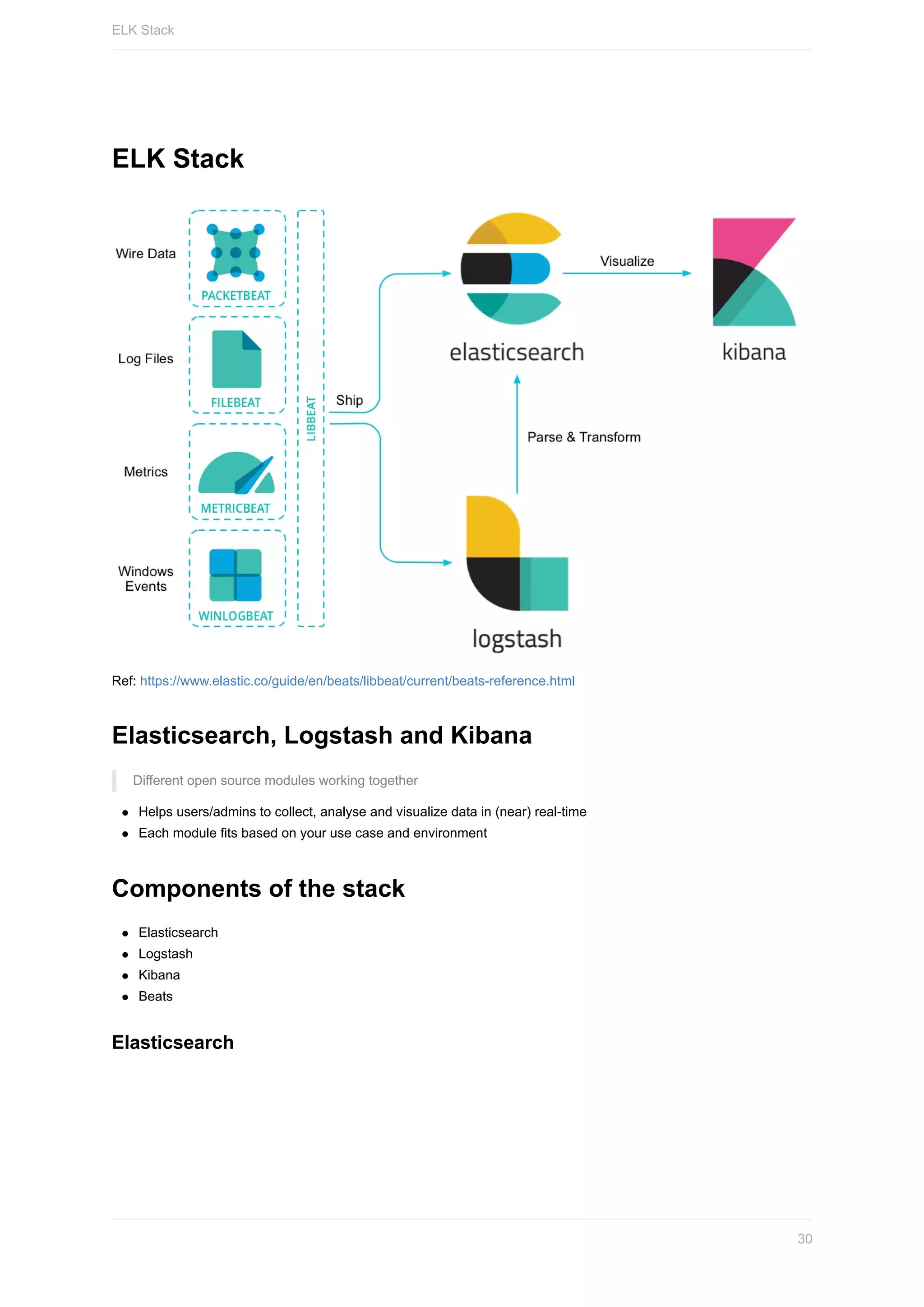
![Different types of Beats
Filebeat: Log Files
Metricbeat: Metrics
Packetbeat: Network Data
Winlogbeat: Windows Event Logs
Auditbeat: Audit Data
Heartbeat: Uptime Monitoring
Filebeat sample configuration
filebeat.inputs:
- type: log
enabled: true
paths:
- /var/log/auth.log
tags: ["sshlog"]
- type: log
enabled: true
paths:
- /var/log/nginx/access.log
tags: ["weblog"]
output.logstash:
hosts: ["localhost:5044"]
ELK Stack for Security Monitoring & Alerting
It helps to parse large amount of log data
We can aggregate and correlate the data from different types of log formats
Centralized way to look into entire logs
Provides near real-time search and visualization capabilities
ELK Reference Guide
We can use the below Gitbook with detailed instructions for references to the ELK stack setup and usage.
https://appsecco.com/books/elk-workshop
ELK Stack
33](https://image.slidesharecdn.com/madhuakula-automateddefenseusingcloudserviceawsazuregcp-190227051351/75/SACON-Madhu-Akula-Automated-Defense-Using-Cloud-Service-Aws-Azure-Gcp-33-2048.jpg)
![Alerting
We can set up a notification system to let users/admins know that a pattern match has occurred.
Logstash output plugin alerting via (Email, Pager duty, JIRA, etc.)
An open source alerting for elasticsearch by Yelp called elastalert
Another open source project by Etsy 411
X-Pack (commerical offering by Elastic)
Custom scripts
ElastAlert
ElastAlert is a simple framework for alerting on anomalies, spikes, or other patterns of interest from data in
Elasticsearch.
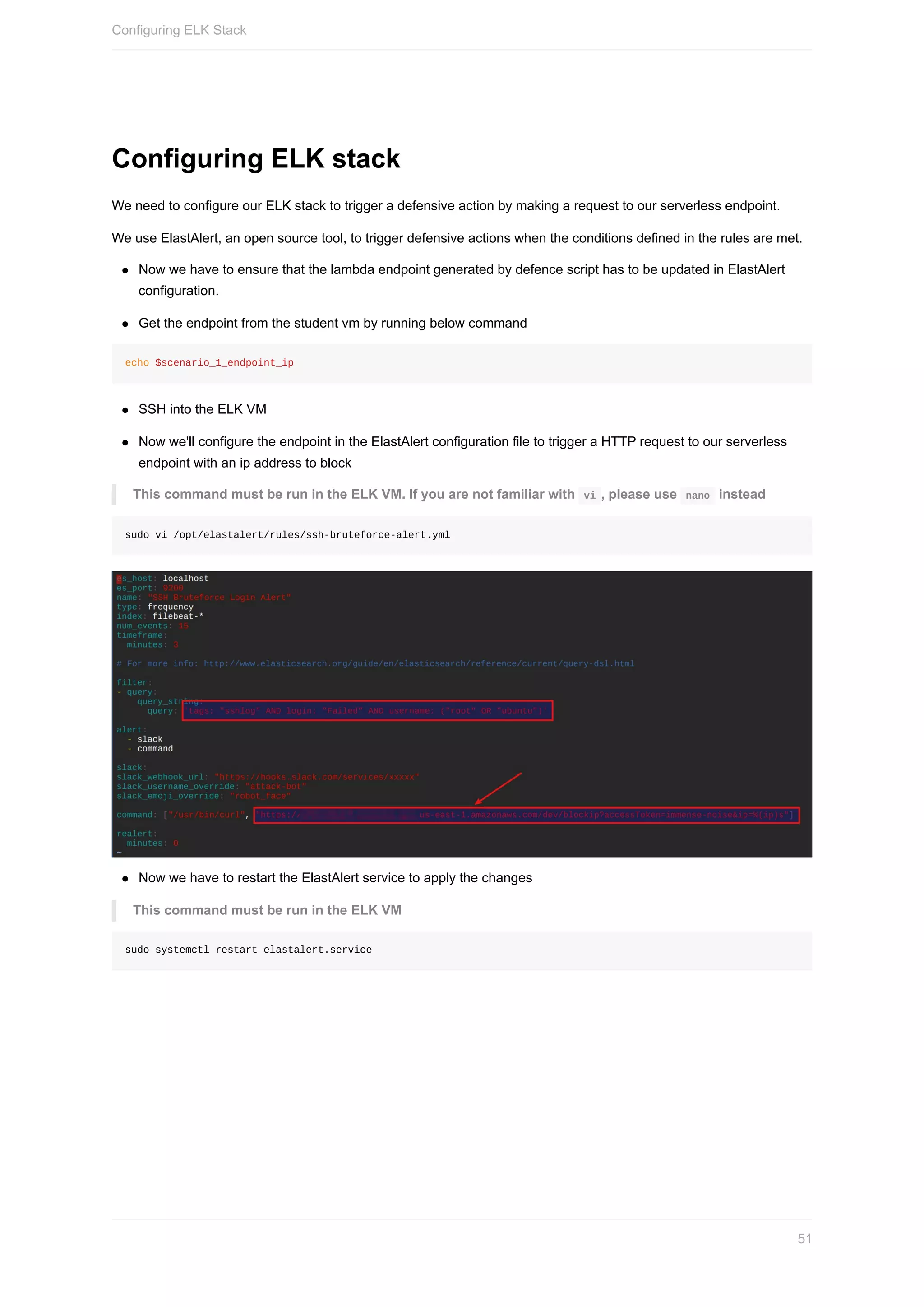
Simple ElastAlert rule to detect ssh bruteforce attacks
es_host: localhost
es_port: 9200
name: "SSH Bruteforce Login Alert"
type: frequency
index: filebeat-*
num_events: 12
timeframe:
minutes: 3
# For more info:
# http://www.elasticsearch.org/guide/en/elasticsearch/reference/current/query-dsl.html
filter:
- query:
query_string:
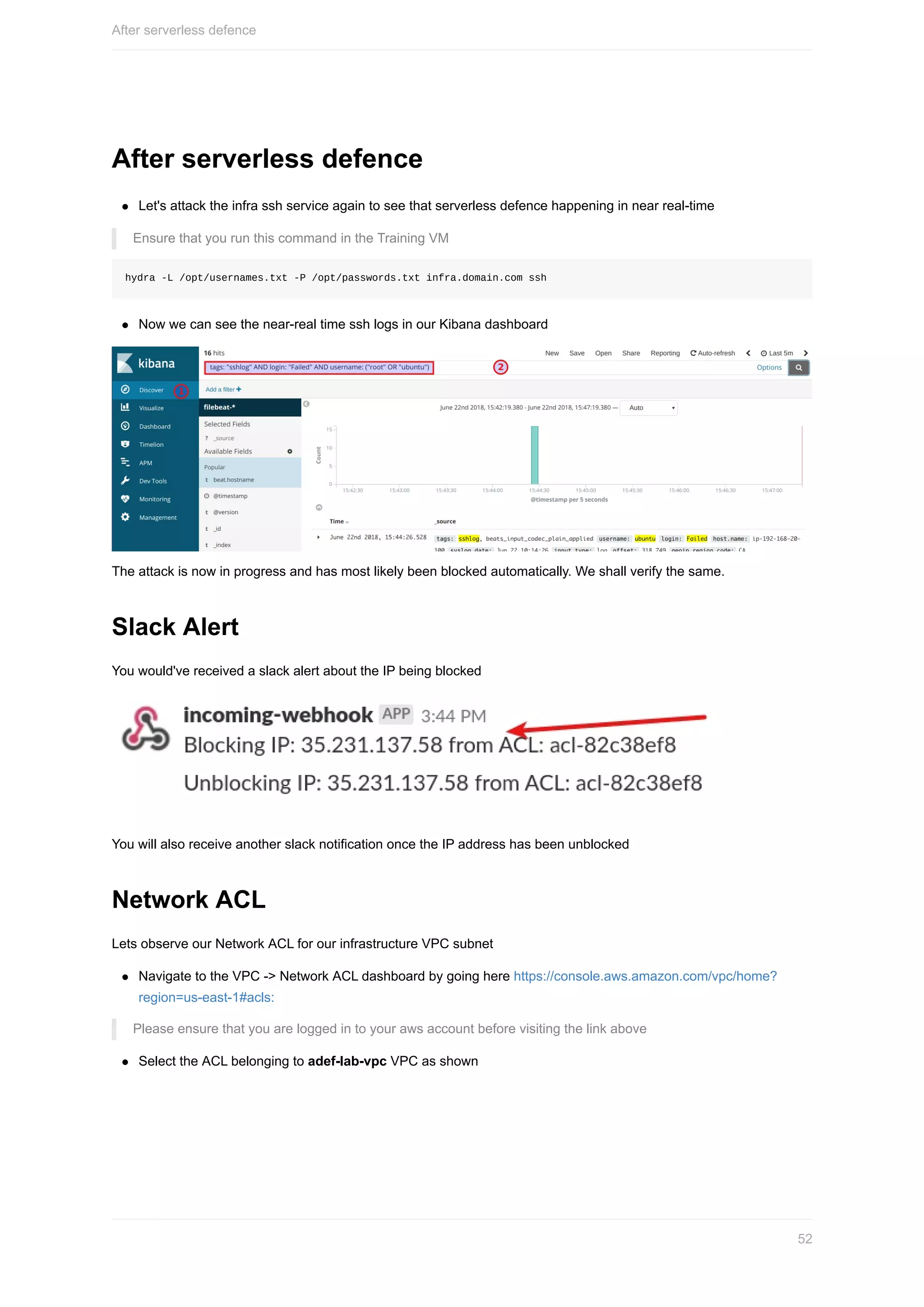
query: 'tags: "sshlog" AND login: "Failed" AND username: ("root" OR "ubuntu")'
alert:
- slack
- command
slack:
slack_webhook_url: "https://hooks.slack.com/services/xxxxx"
slack_username_override: "attack-bot"
slack_emoji_override: "robot_face"
command: ["/usr/bin/curl", "https://LAMBDAENDPOINTGOESHERE/%(ip)s"]
realert:
minutes: 0
Rule Types
Any
Blacklist
Whitelist
Change
Frequency
Spike
Flatline
New Term
Alerting
34](https://image.slidesharecdn.com/madhuakula-automateddefenseusingcloudserviceawsazuregcp-190227051351/75/SACON-Madhu-Akula-Automated-Defense-Using-Cloud-Service-Aws-Azure-Gcp-34-2048.jpg)












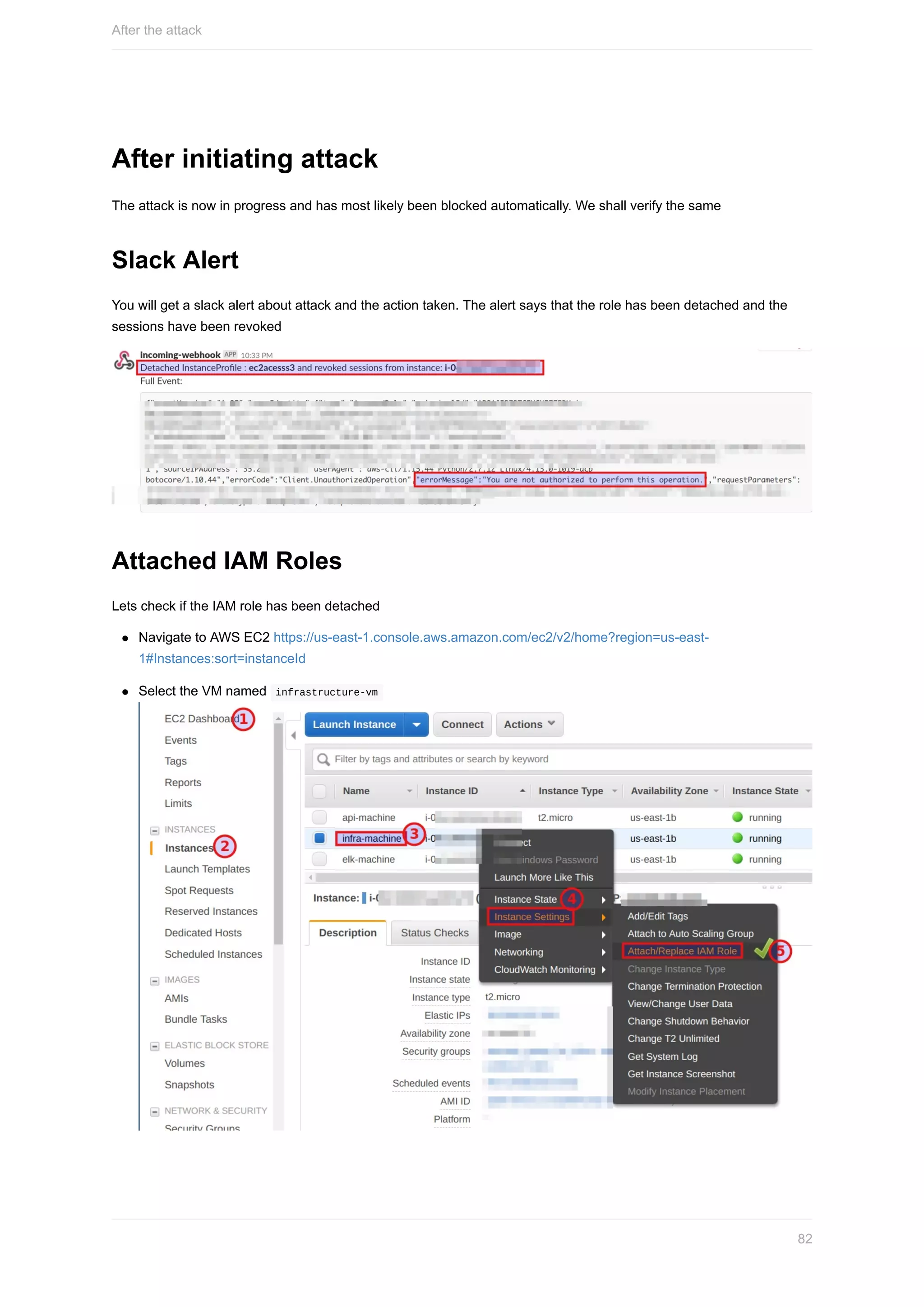
![Using the stolen IAM Credentials
Lets use the stolen IAM credentials. We can do that by adding the credentials under an AWS cli profile in our training
VM
Configure the credentials found by
Ensure that you run this command in the Training VM
aws configure --profile ssrfkey
As we got temporary session token, we have to edit ~/.aws/credentials and add the session token
[ssrfkey]
aws_access_key_id = xxxxxxxxxxxxxxxxxxx
aws_secret_access_key = xxxxxxxxxxxxxxxxxxx
aws_session_token = xxxxxxxxxxxxxxxxxxx
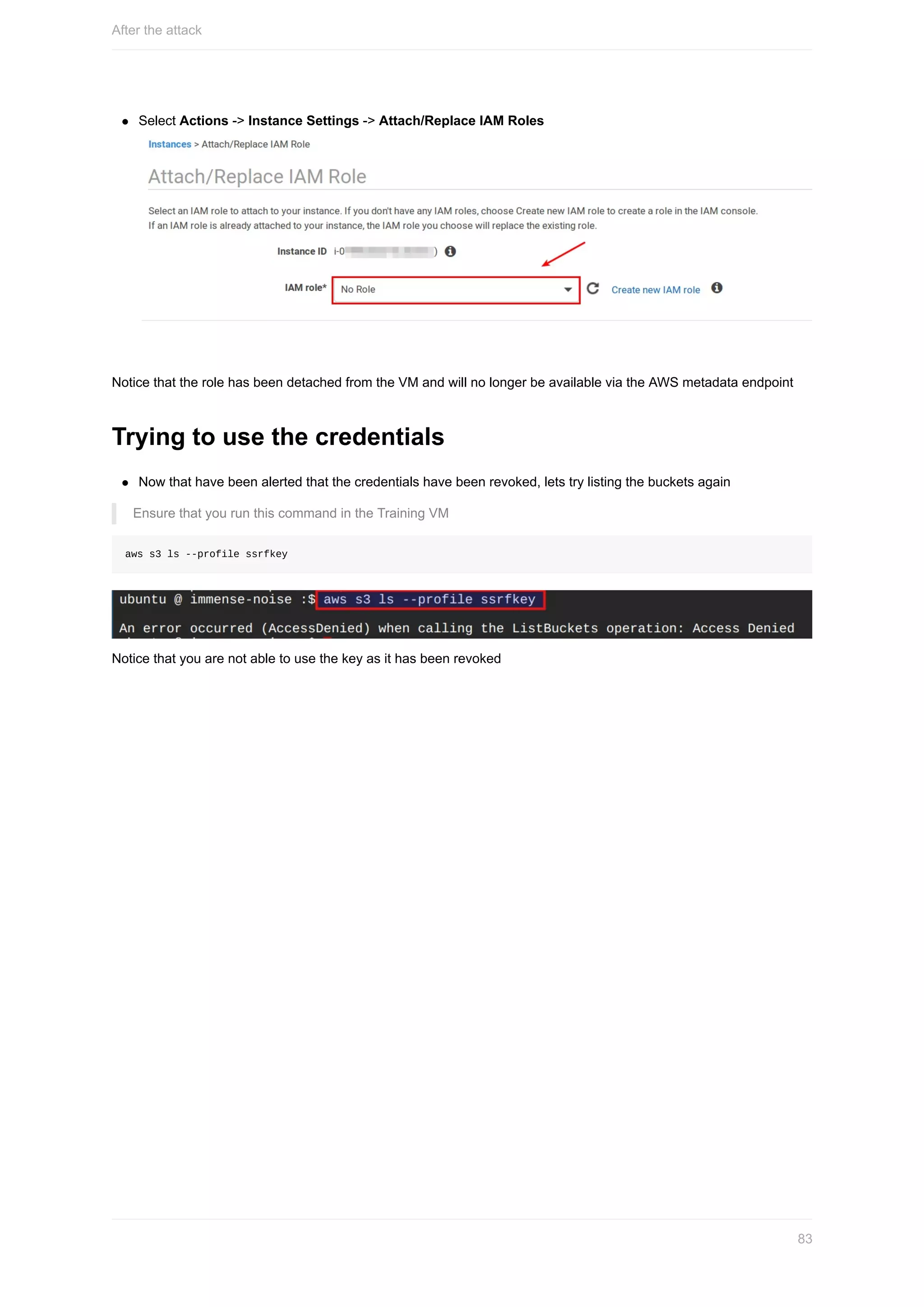
Lets try listing the S3 buckets under the AWS account using the found key
Ensure that you run this command in the Training VM
aws s3 ls --profile ssrfkey
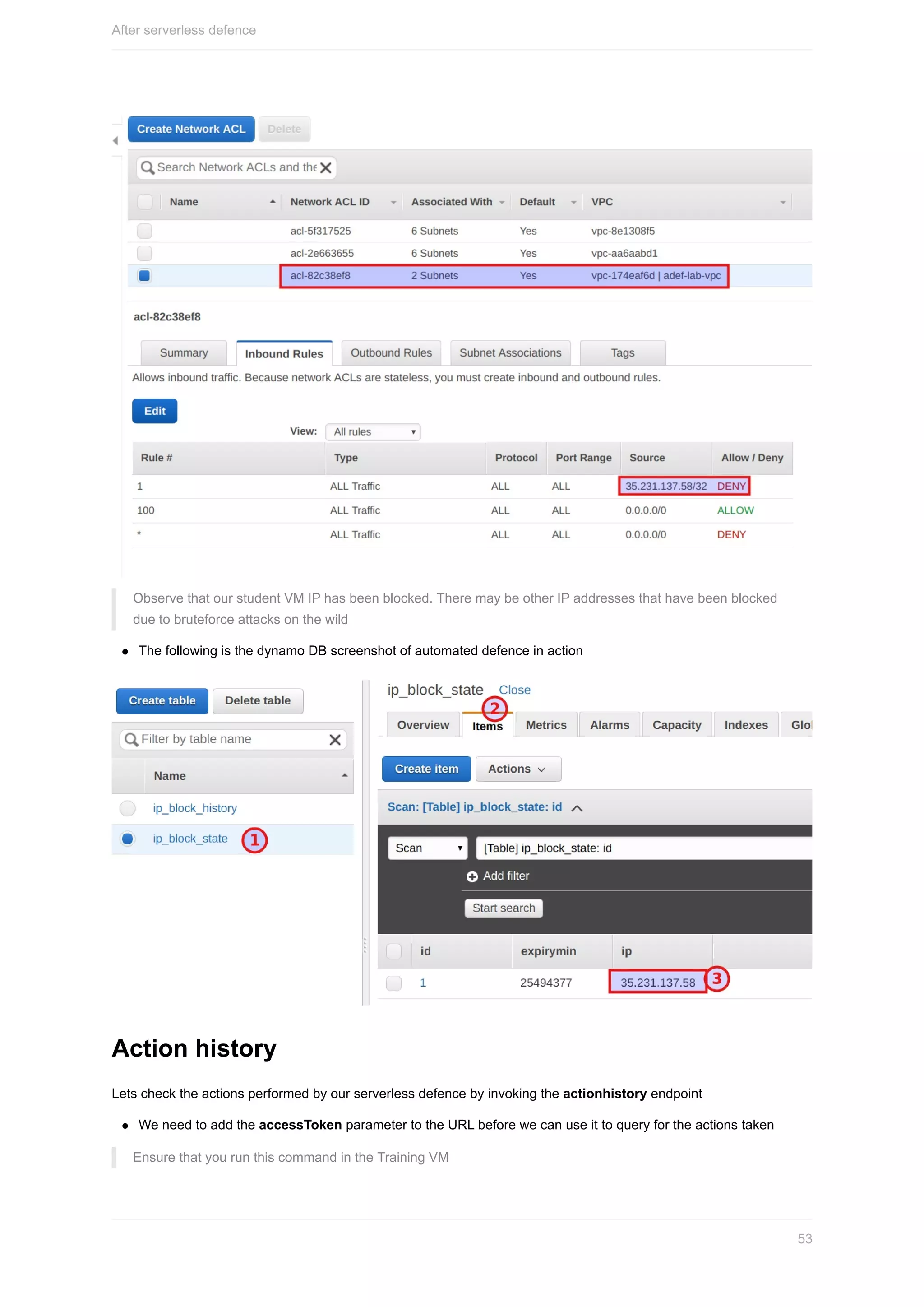
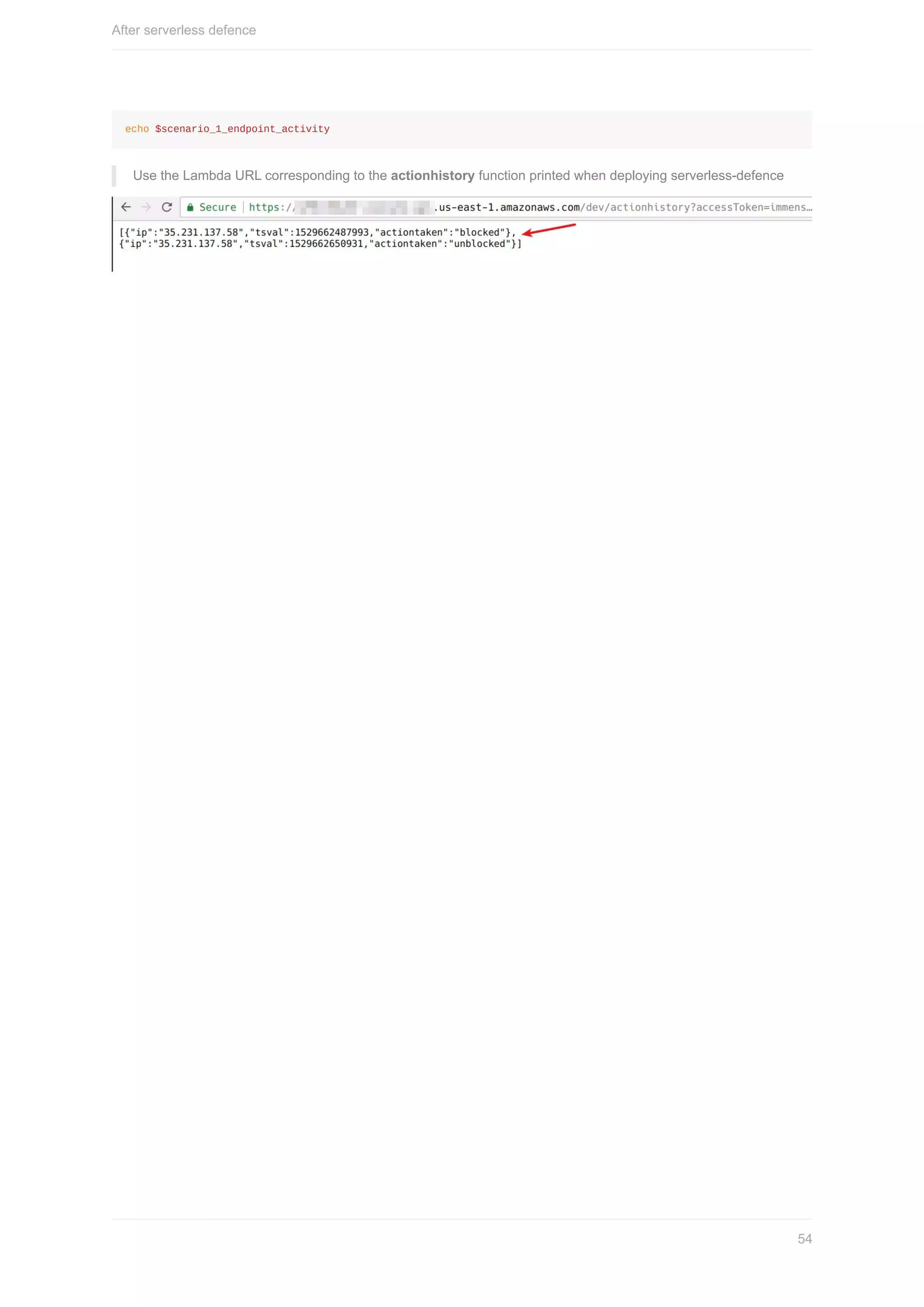
You can see that you are able list the s3 buckets under the account
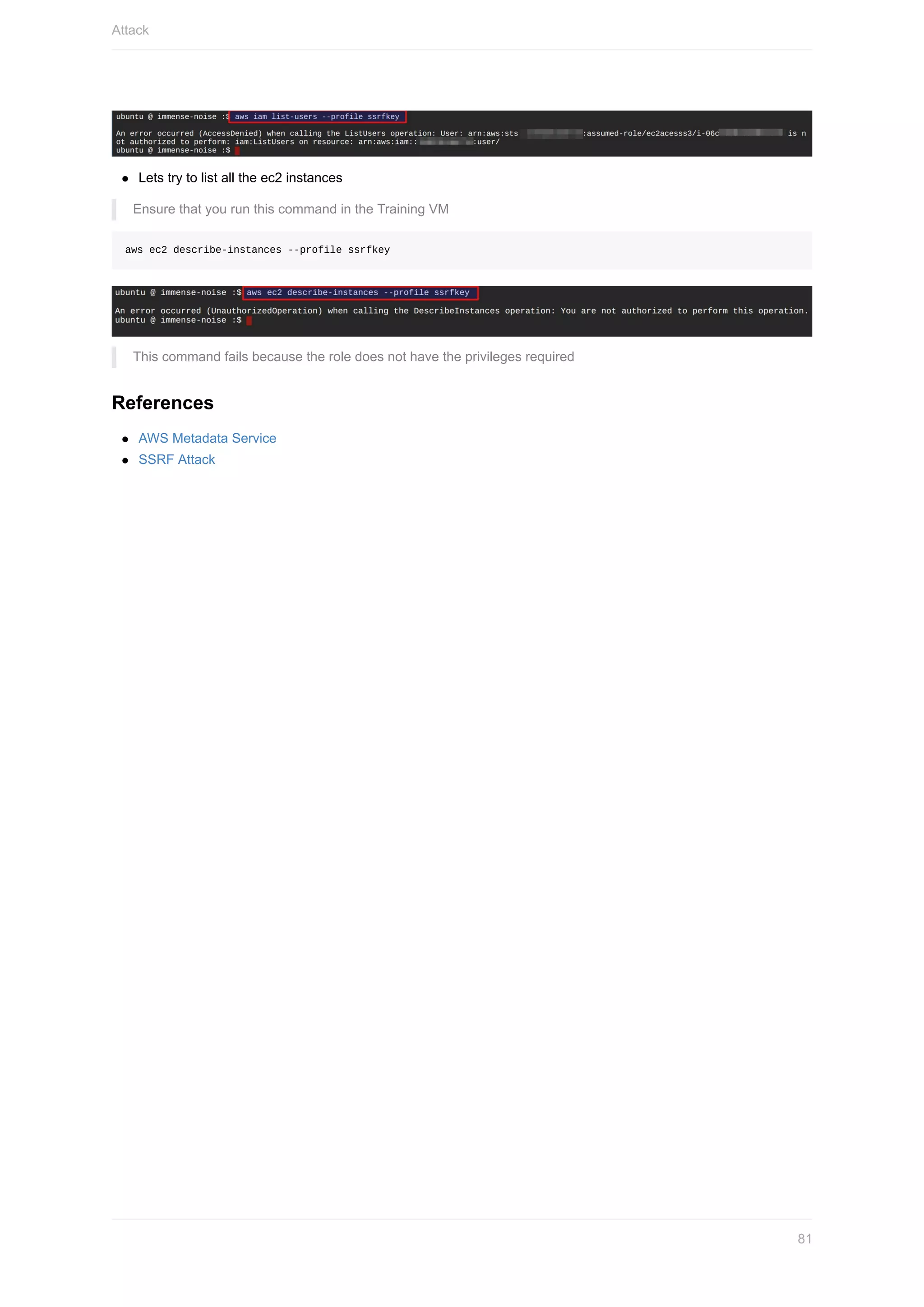
Lets try to enumerate further by listing all IAM users
Ensure that you run this command in the Training VM
aws iam list-users --profile ssrfkey
Attack
80](https://image.slidesharecdn.com/madhuakula-automateddefenseusingcloudserviceawsazuregcp-190227051351/75/SACON-Madhu-Akula-Automated-Defense-Using-Cloud-Service-Aws-Azure-Gcp-80-2048.jpg)