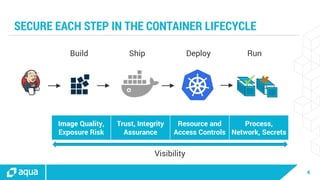
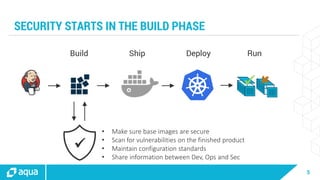
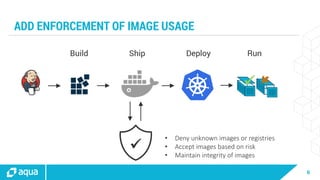
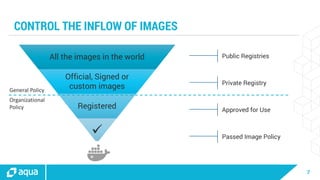
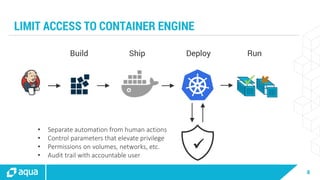
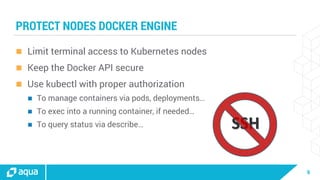
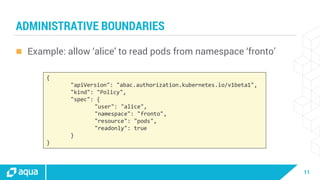
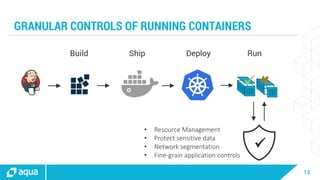
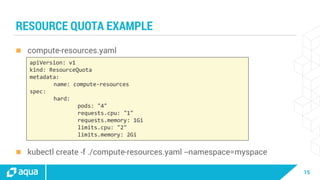
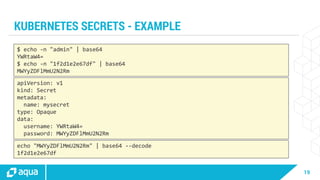
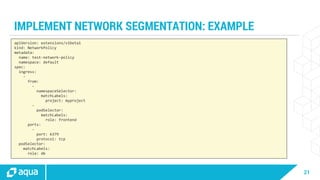
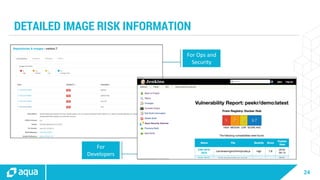
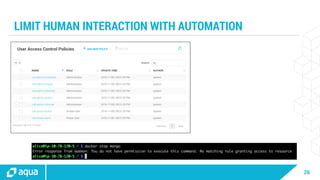
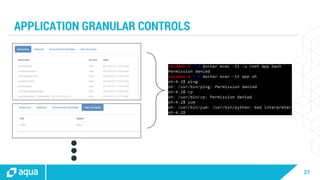
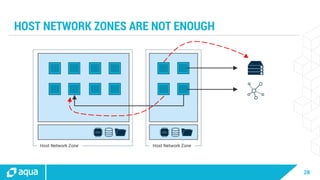
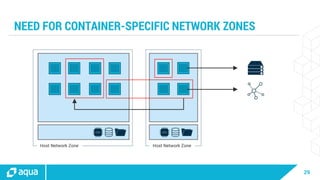
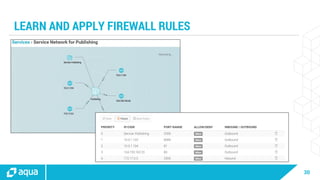
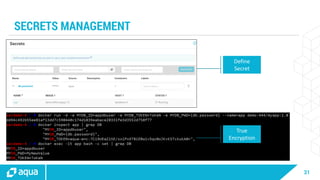
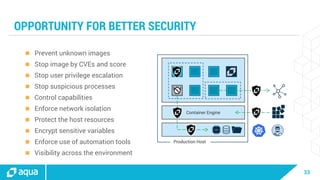
The document discusses security best practices for managing containers in Kubernetes, emphasizing the importance of securing each phase of the container lifecycle and implementing strict access controls. It outlines the need for secure images from trusted sources, effective network segmentation, and proper secrets management to mitigate risks. Additionally, it highlights the necessity for resource quotas and compliance with regulatory requirements to enhance overall security in containerized environments.