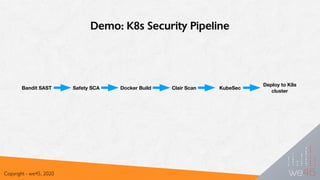
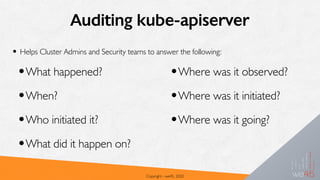
This document provides an overview of attacking and defending Kubernetes clusters. It begins with introductions to containers, container orchestration with Kubernetes, and Kubernetes architecture and components. It then discusses the Kubernetes threat model and common attack vectors such as compromising nodes, pods, and secrets. The document outlines Kubernetes authentication and authorization methods like RBAC and discusses admission controllers. It covers securing Kubernetes with practices like pod security policies and network policies. Finally, it notes some limitations and gotchas regarding secrets management in Kubernetes.



























![RBAC K8s Authorization
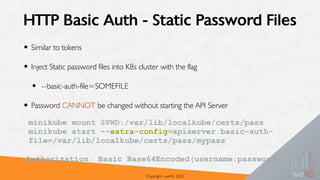
• RBAC Authorization refers to Roles that contain
rules of Permissions
• Permissions are only additive (No Deny)
• Easy to manage, when you have a a clearly defined
set of privileges for the roles
• Two Types:
• ClusterRole => Role that applies across the
Cluster (across Namespaces)
• Role => applies to Permissions that work
across a single namespace
kind: Role
apiVersion:
rbac.authorization.k8s.io/
v1
metadata:
namespace: default
name: pod-reader
rules:
- apiGroups: [""] # ""
indicates the core API
group
resources: ["pods"]
verbs: ["get", "watch",
"list"]](https://image.slidesharecdn.com/owasp-k8s-200202170430/85/Attacking-and-Defending-Kubernetes-Nithin-Jois-33-320.jpg)

























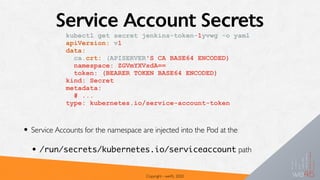
![Copyright - we45, 2020
{
"kind":"Event",
"apiVersion":"audit.k8s.io/v1beta1",
"metadata":{ "creationTimestamp":"2019-03-21T14:30:12Z" },
"level":"Metadata",
“timestamp":"2019-03-21T14:30:12Z",
"auditID":"442d9cc4-bfc5-4a59-b688-dcebe905ce55",
"stage":"RequestReceived",
"requestURI":"/api/v1/namespaces/default/services",
"verb":"list",
"user": {
"username":"example@example.org",
"groups":[ "system:authenticated" ]
},
"sourceIPs":[ "192.168.1.139" ],
"objectRef": {
"resource":"services",
"namespace":"default",
"apiVersion":"v1"
},
"requestReceivedTimestamp":"2019-03-21T14:30:12.720183Z",
"stageTimestamp":"2019-03-21T14:30:12.720183Z"
Audit Log Example](https://image.slidesharecdn.com/owasp-k8s-200202170430/85/Attacking-and-Defending-Kubernetes-Nithin-Jois-62-320.jpg)