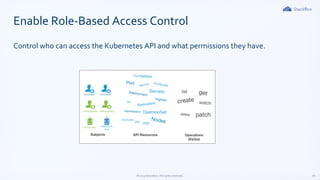
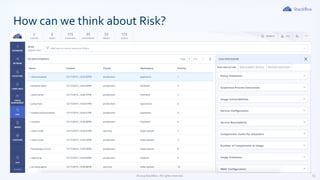
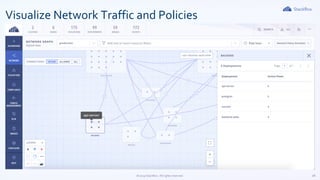
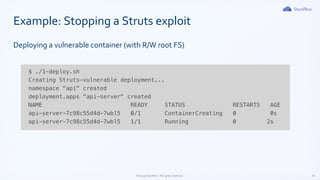
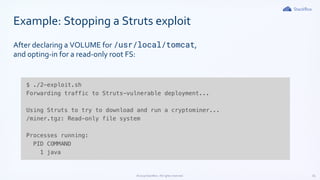
The document outlines Kubernetes security best practices, emphasizing the importance of maintaining up-to-date versions, hardening node security, and implementing role-based access control. It discusses workload best practices such as using namespaces for resource tracking and network policies for compliance, along with the reduction of image sizes for security. Additionally, it highlights configurations like read-only file systems and Linux capabilities management to enhance the security of Kubernetes environments.