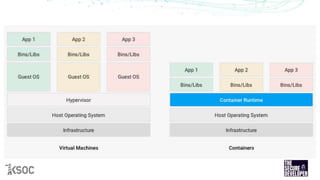
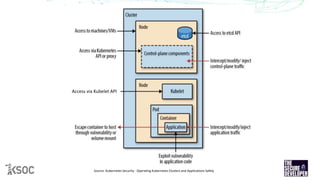
The document provides an overview of Kubernetes security, highlighting the nature of containers and their vulnerabilities, such as privilege escalation and the risk of container breakout. It discusses various threat models associated with Kubernetes, including user compromises, application vulnerabilities, and misconfigurations, along with best practices for securing Kubernetes environments. Emphasis is placed on the necessity for ongoing security assessments, effective access controls, and leveraging tools like Open Policy Agent for policy enforcement.


































![role.yaml
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: development
name: pod-reader
rules:
- apiGroups: [""]
resources: [”pods"]
verbs: ["get", "list"]](https://image.slidesharecdn.com/the-state-of-kubernetes-security-190926171334/85/The-State-of-Kubernetes-Security-37-320.jpg)




















![@jimmesta
jimmy[at]ksoc.com](https://image.slidesharecdn.com/the-state-of-kubernetes-security-190926171334/85/The-State-of-Kubernetes-Security-60-320.jpg)