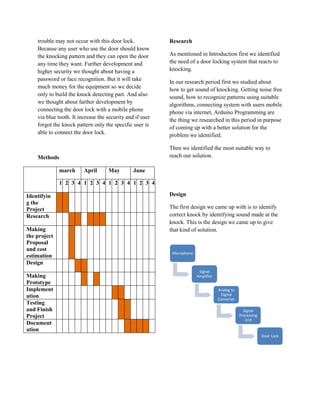
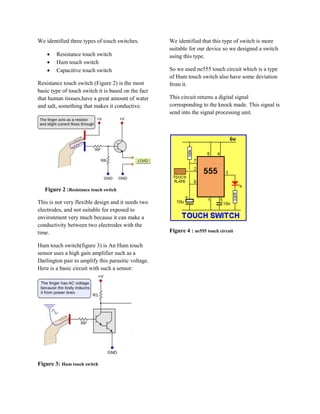
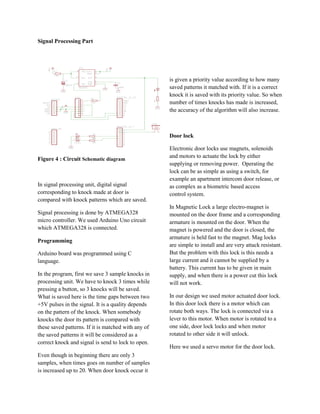
The document describes a knock detecting door lock system that uses pattern recognition to unlock the door based on a user's unique knocking pattern. The system was designed to improve security over traditional key-based locks by only allowing those who know the correct pattern to open the door. The initial design used a microphone and sound processing but was changed to instead use touch sensors due to issues with noise. The final system design detects knocking patterns through touch sensors and unlocks the door if the pattern matches what is programmed by the user.