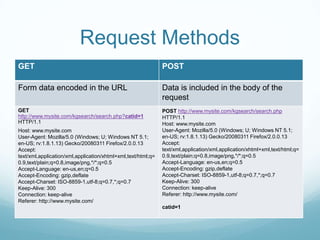
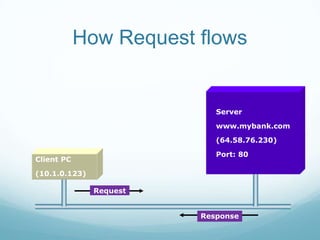
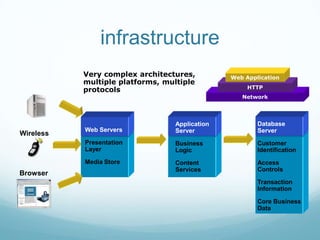
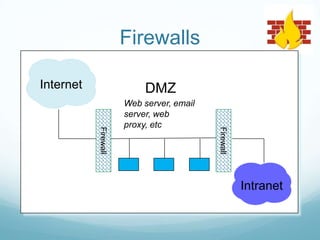
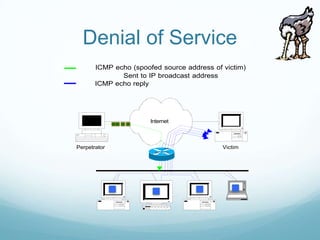
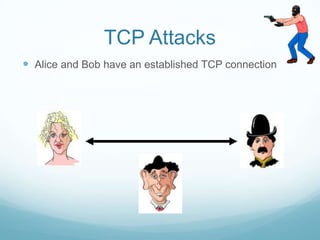
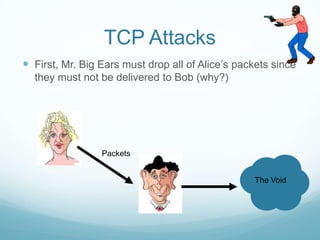
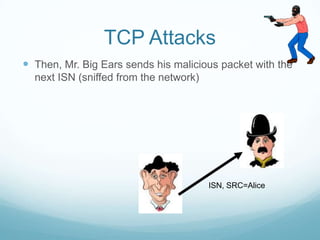
The document provides an overview of web application and network security. It begins with definitions of web applications and how requests are made via protocols like HTTP and HTTPS. It then covers common security attacks such as denial of service attacks, TCP hijacking, and packet sniffing. The document discusses countermeasures for these attacks like firewalls, intrusion detection systems, and encryption. It also covers vulnerabilities in web applications like SQL injection, cross-site scripting, and input validation issues. The key information is on common security attacks against web applications and networks and their corresponding countermeasures.