The document discusses advanced persistent threats (APTs) and methods for fighting them using open source tools. It describes the characteristics of APTs and provides examples like the GhostNet and Aurora attacks. It also analyzes the Trojan.Hydraq used in Aurora. The key to fighting APTs is centralizing and correlating security data. Effective countermeasures include log monitoring, integrity monitoring, IDS/IPS, and analyzing suspicious network traffic and files to build a behavior matrix.





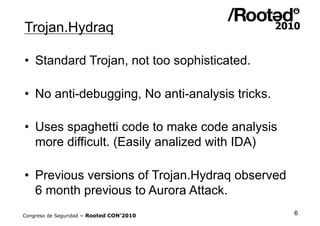
![Trojan.Hydraq
• Files:
– %System%[RANDOM].dll: Main backdoor
registered as a service.
– %System%acelpvc.dll: Remote access
capabilities (VNC).
– %System%VedioDriver.dll: Helps monitoring
keyboard and mouse activity.
Congreso de Seguridad ~ Rooted CON’2010 7](https://image.slidesharecdn.com/jaimeblasco-fightingaptwithostools-100328035248-phpapp01/85/Jaime-Blasco-Fighting-Advanced-Persistent-Threat-APT-with-Open-Source-Tools-RootedCON-2010-7-320.jpg)

![Trojan.Hydraq
• C&C communication:
– Encrypted protocol on port 443 (not SSL)
[ ff ff ff ff ff ff 00 00 fe ff ff ff ff ff ff ff ff ff 88 ff ]
Source: McAfee Labs
Congreso de Seguridad ~ Rooted CON’2010 9](https://image.slidesharecdn.com/jaimeblasco-fightingaptwithostools-100328035248-phpapp01/85/Jaime-Blasco-Fighting-Advanced-Persistent-Threat-APT-with-Open-Source-Tools-RootedCON-2010-9-320.jpg)

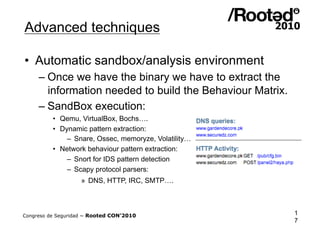
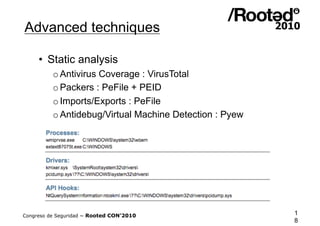
![Advanced techniques
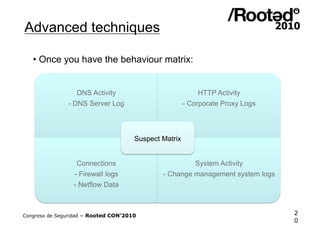
• Build the behaviour matrix, example:
[ Process_Creation, test.exe]
[ DNS_Query, www.securedz.com]
[ HTTP_Request, POST, /panel2/haya.php]
[ Driver_Loaded, wowsub.sys]
[ IDS_Pattern, Snort, 2008576]
Congreso de Seguridad ~ Rooted CON’2010 1
9](https://image.slidesharecdn.com/jaimeblasco-fightingaptwithostools-100328035248-phpapp01/85/Jaime-Blasco-Fighting-Advanced-Persistent-Threat-APT-with-Open-Source-Tools-RootedCON-2010-19-320.jpg)