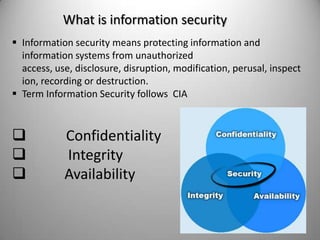
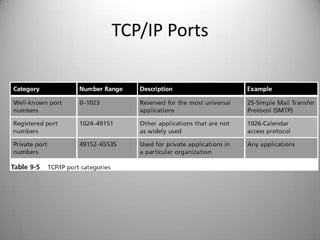
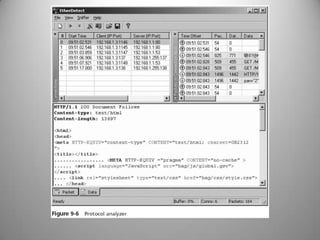
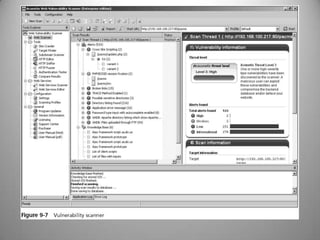
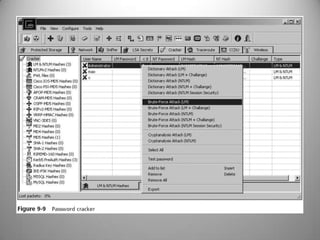
The document discusses the concepts of hacking and ethical hacking, highlighting the differences between white hat, black hat, and gray hat hackers. It defines information security and its principles of confidentiality, integrity, and availability, along with essential terminology related to threats, vulnerabilities, and attacks. Additionally, it explains various tools used for identifying vulnerabilities, including vulnerability scanning, penetration testing, and password crack techniques.