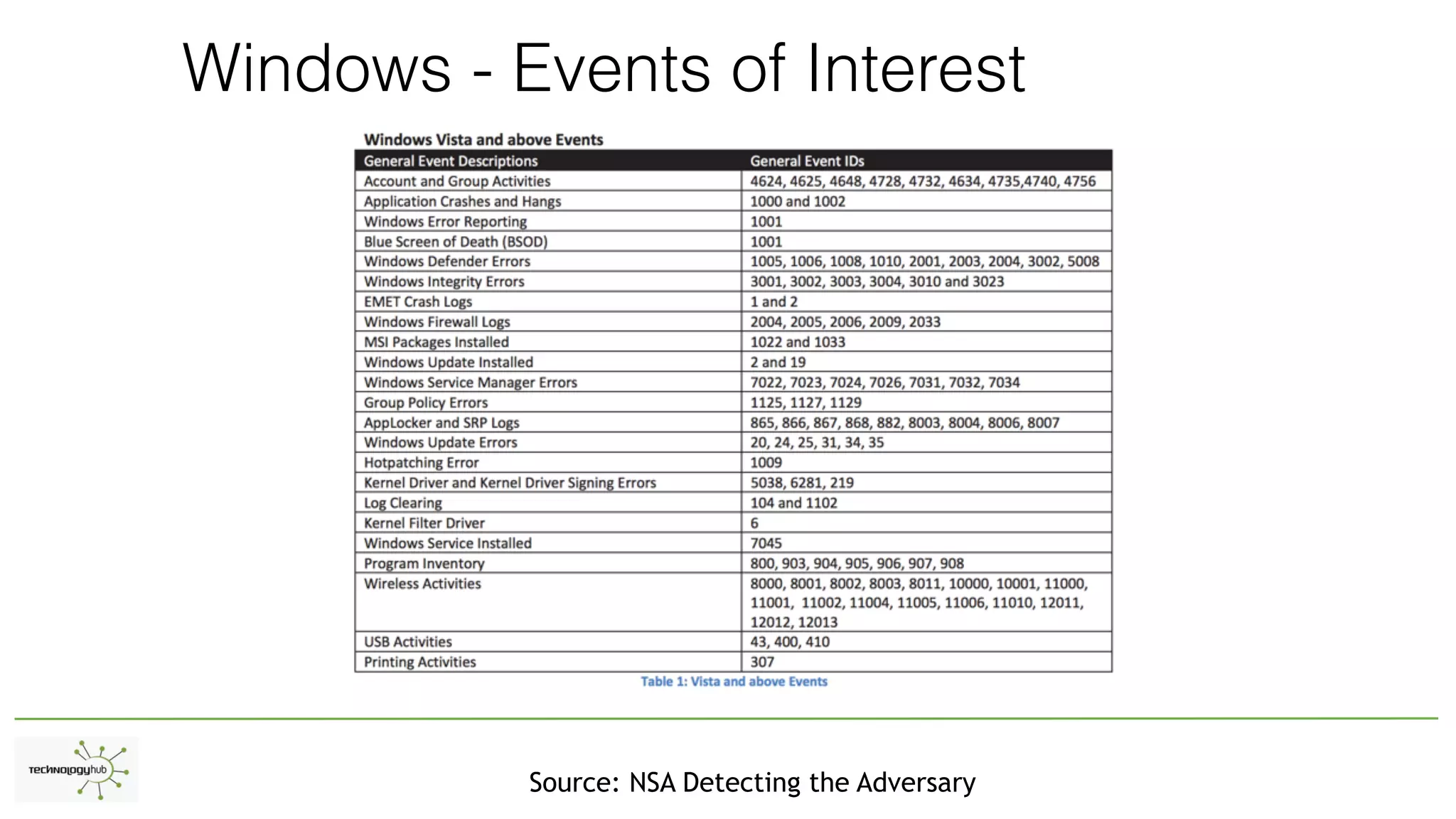
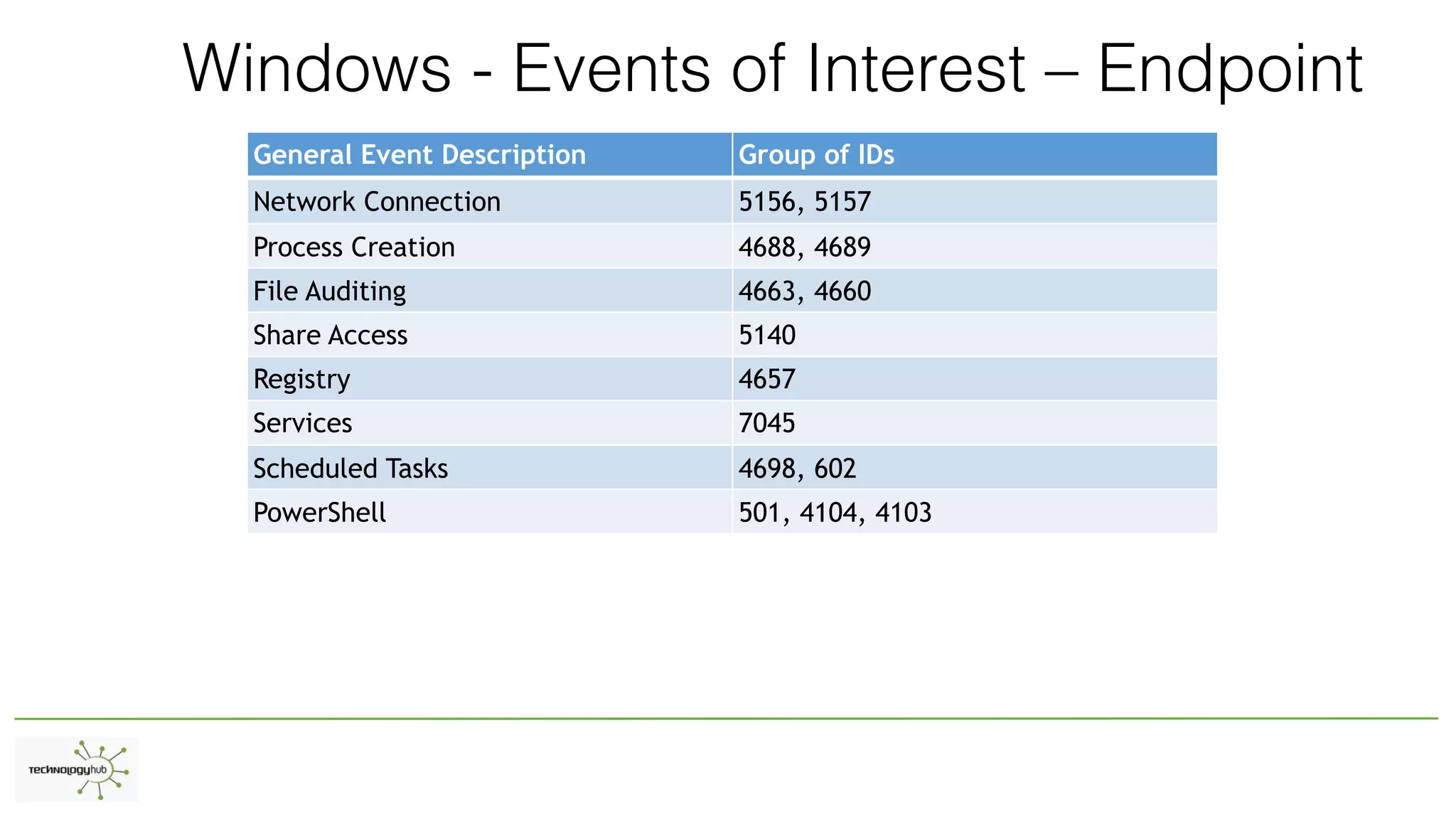
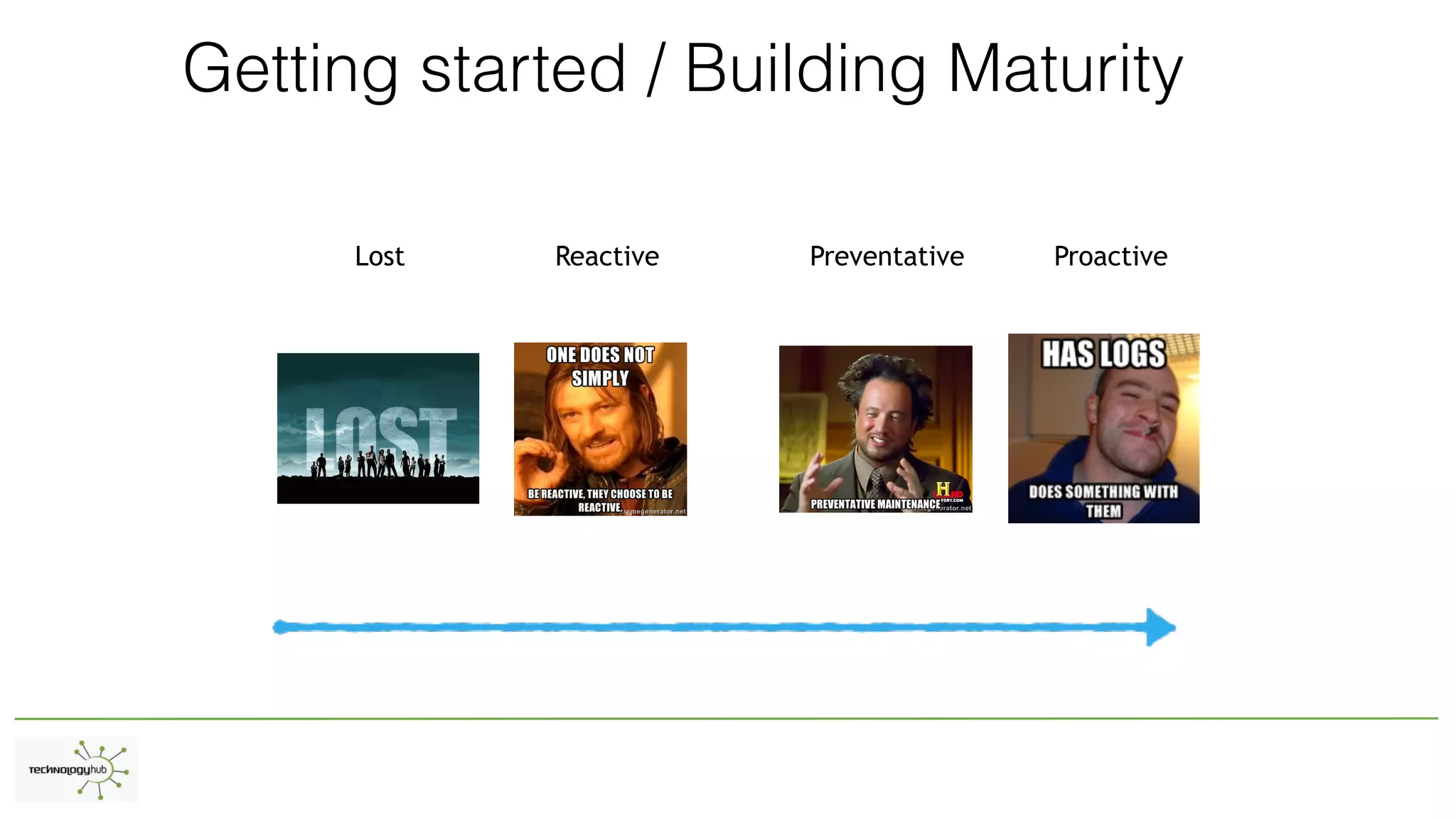
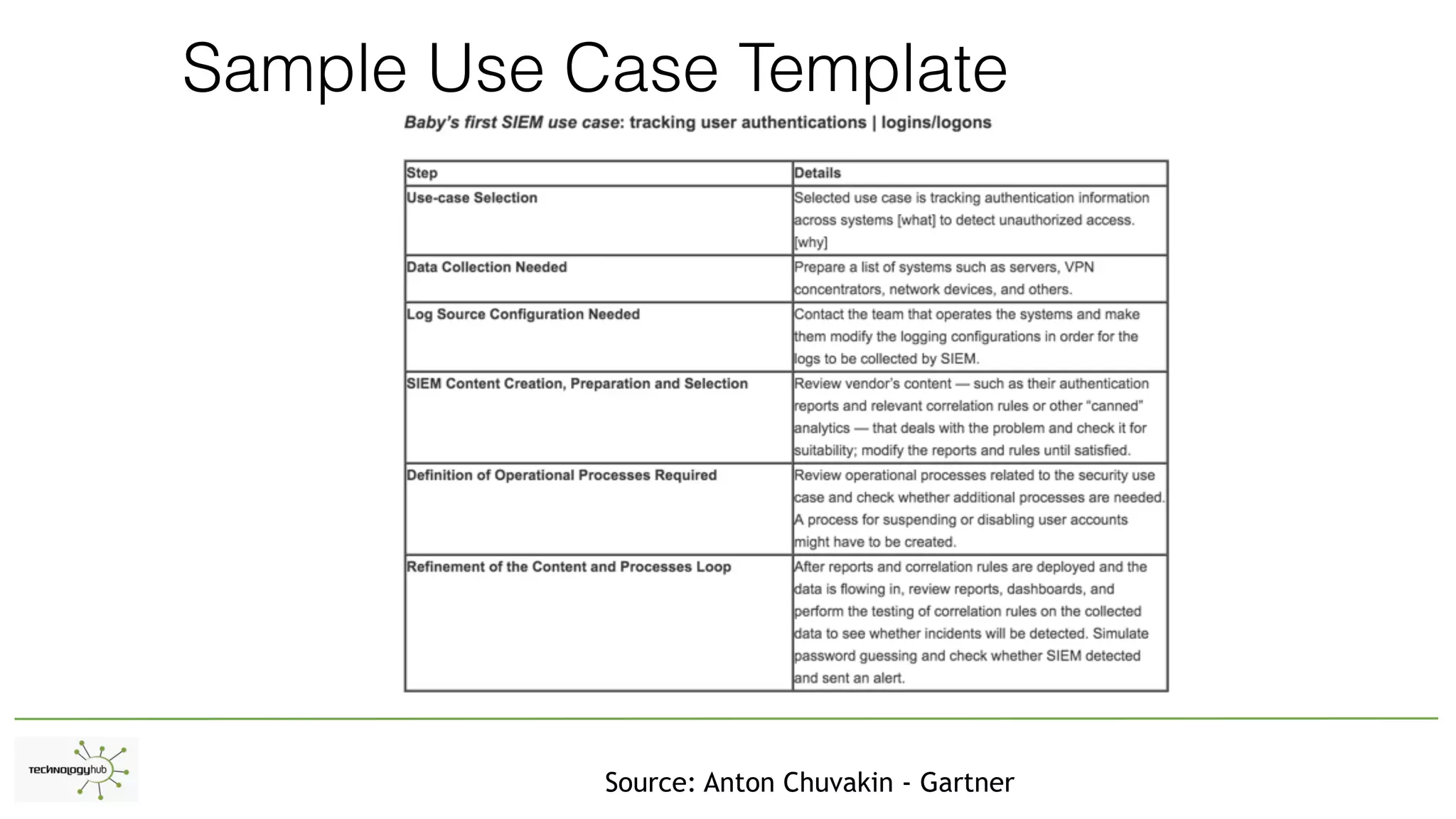
The document discusses the distinctions between logging, alerting, and hunting in information security, emphasizing the importance of proper data collection and analysis to detect adversaries. It outlines various types of logging (Windows and non-Windows) and highlights the need for effective alerting mechanisms that provide high-fidelity signals without overwhelming staff. The document also addresses the maturity stages of an organization's security posture, moving from lost to proactive defense capabilities.