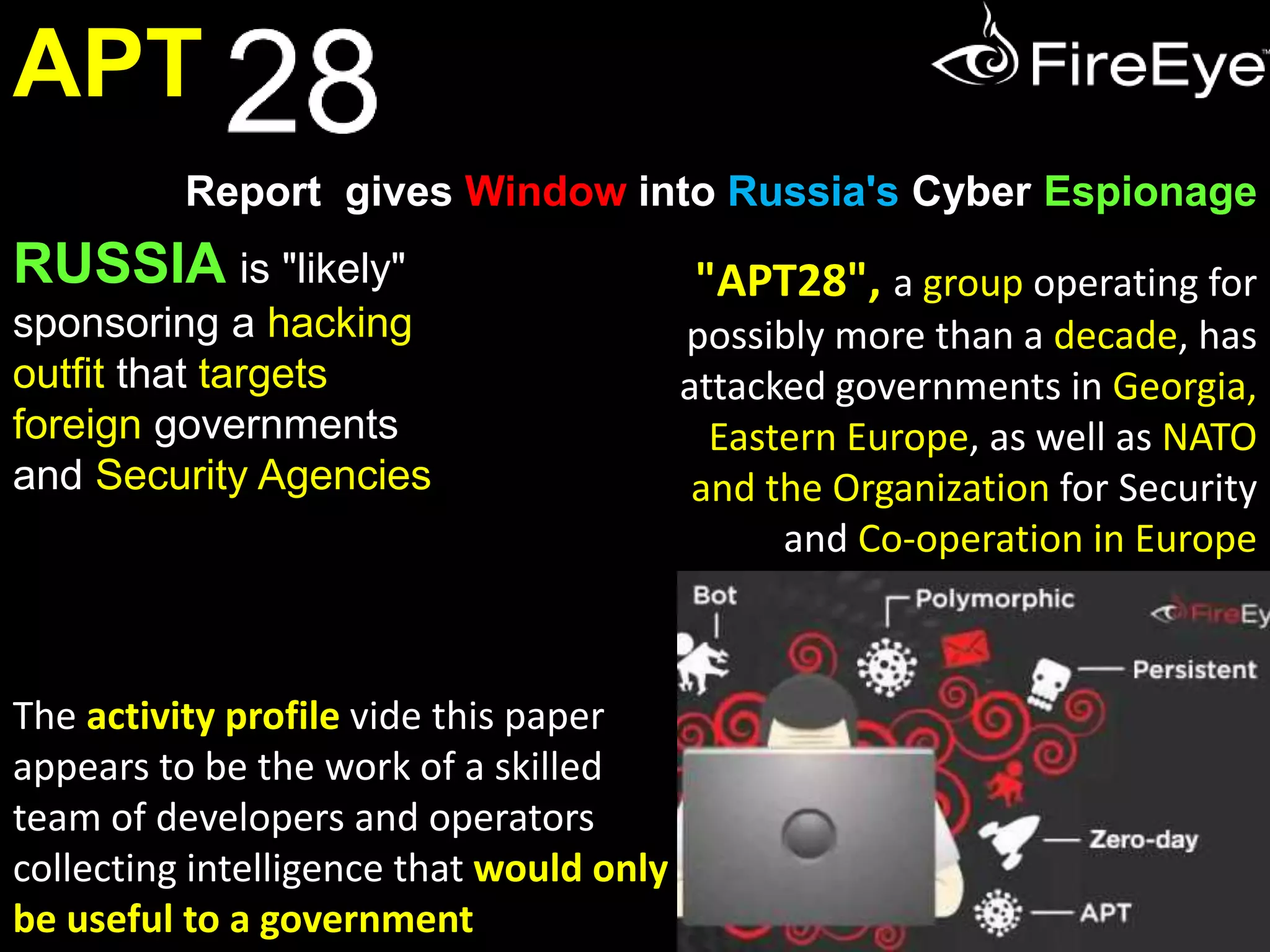
The document discusses APT28, a Russian cyber espionage group targeting foreign governments and security agencies, particularly in Eastern Europe and NATO. The group's operations are characterized by sophisticated malware and tailored spear phishing tactics to gather intelligence and insider information relevant to Russian interests. APT28's activities indicate a systematic approach with tools that have evolved over the years, reflecting connections to the Russian government and its strategic objectives.



















![APT28 has registered domains
similar to those of legitimate
Eastern European (next slide…)
These domain registrations not
only suggest that APT28 is
interested in Eastern European
political affairs, but also that the
group targets Eastern European
governments directly. In addition, APT28 used
one domain for command
and control sessions
(baltichost[.]org) that
was themed after the
Baltic Host exercises.
Baltic Host is a multinational logistics planning
exercise, hosted annually since 2009 by one of
the three Baltic States (Estonia, Latvia, and
Lithuania, all three of which are on Russia’s
border) on a rotational basis.](https://image.slidesharecdn.com/apt28-141130092434-conversion-gate02/75/APT-28-Cyber-Espionage-and-the-Russian-Government-30-2048.jpg)