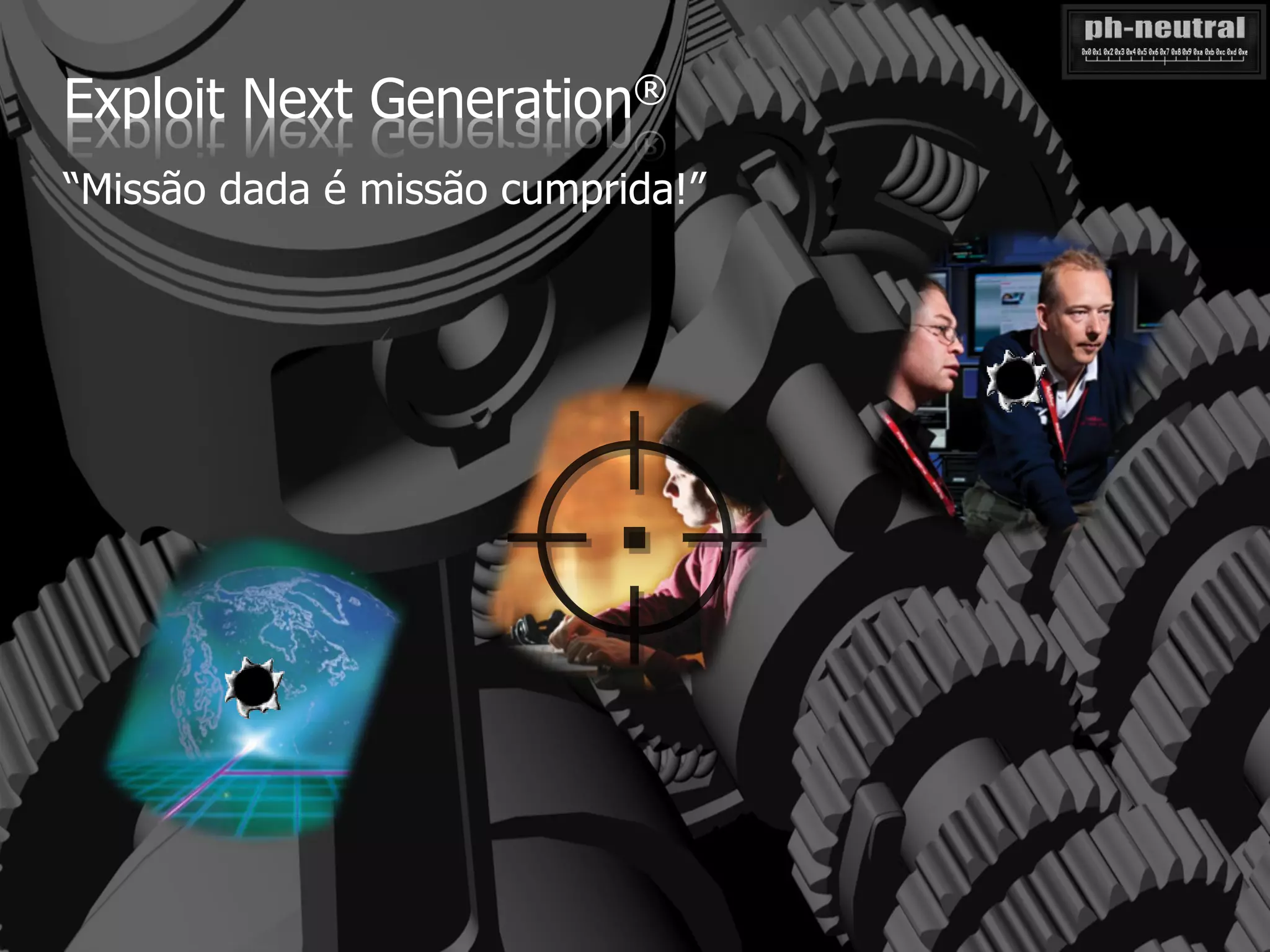
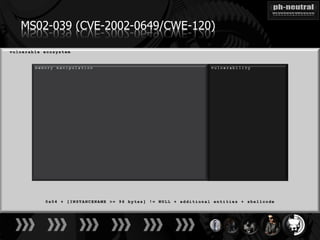
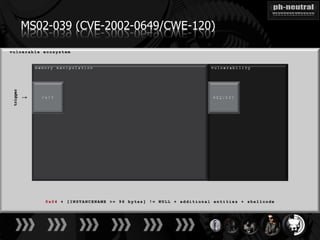
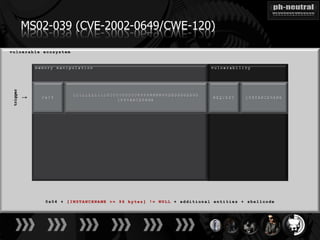
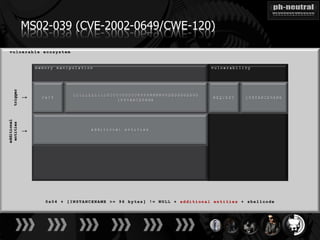
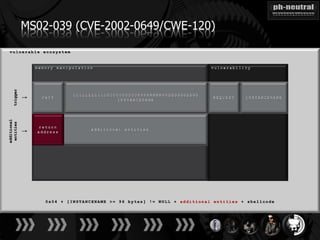
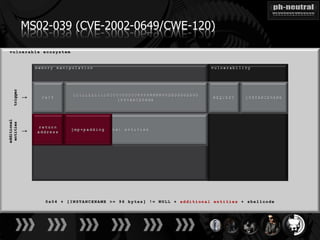
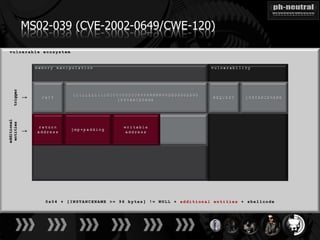
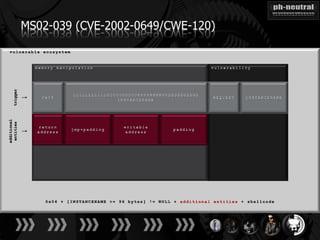
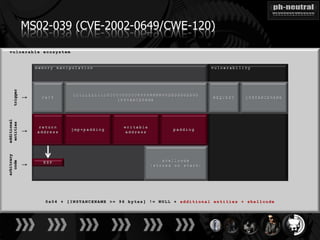
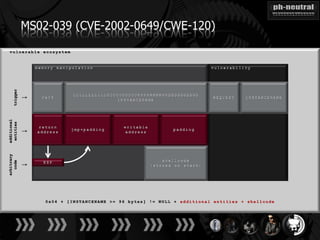
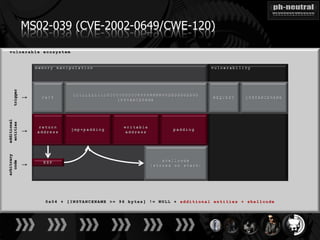
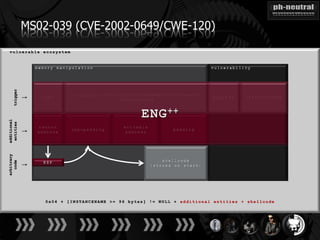
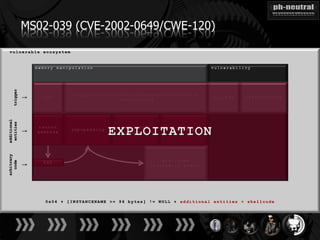
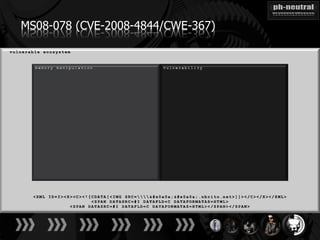
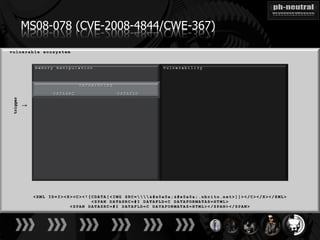
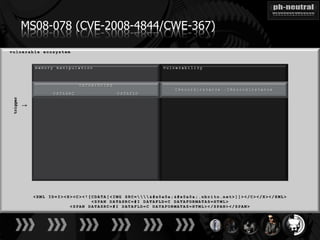
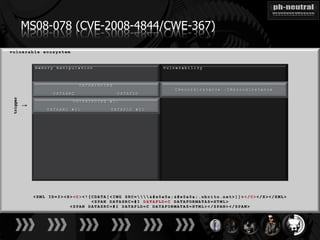
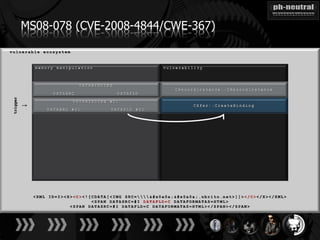
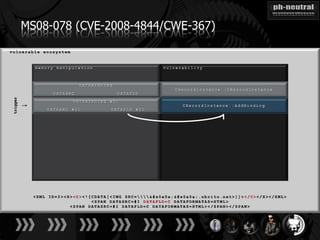
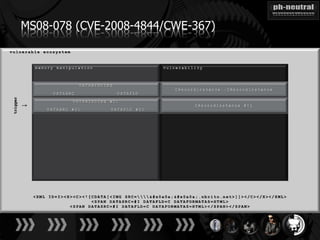
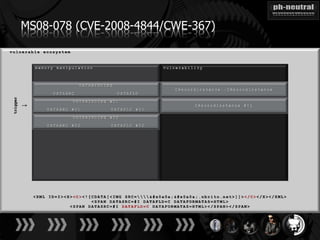
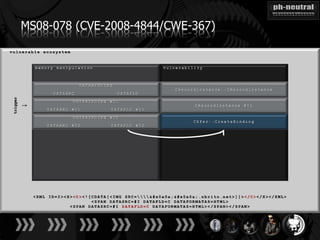
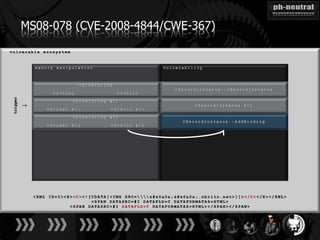
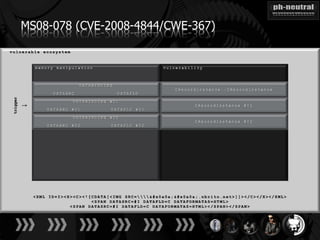
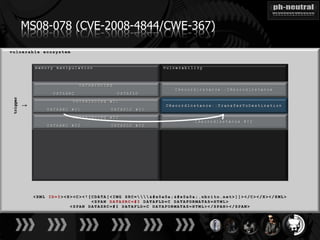
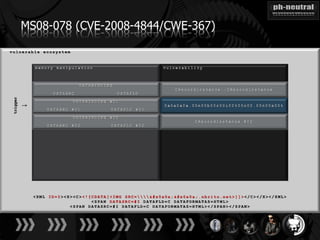
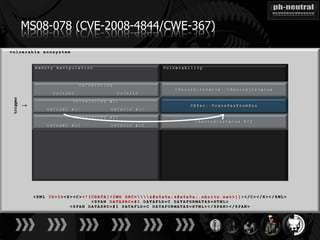
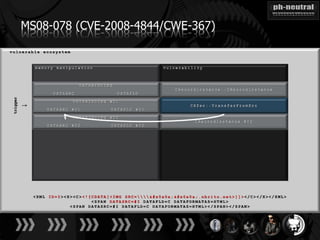
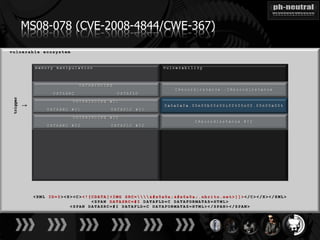
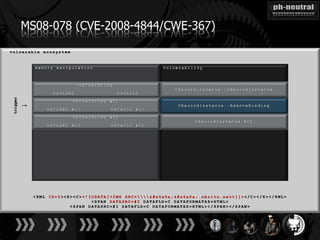
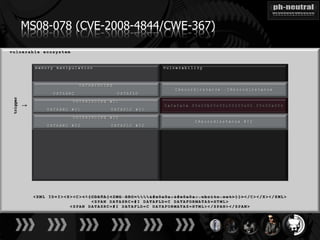
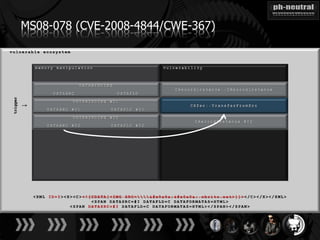
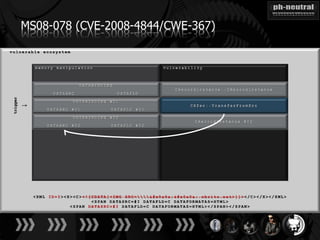
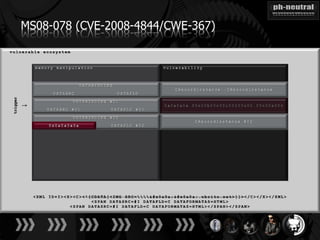
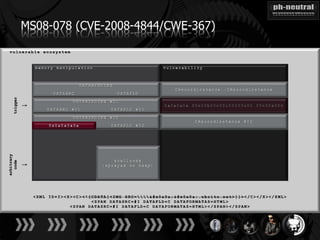
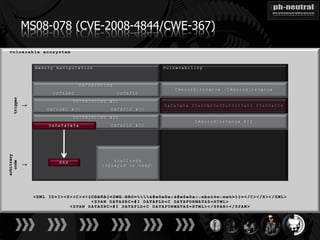
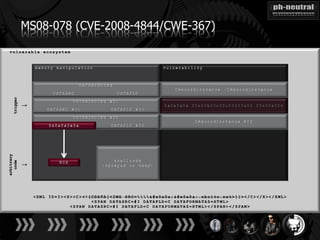
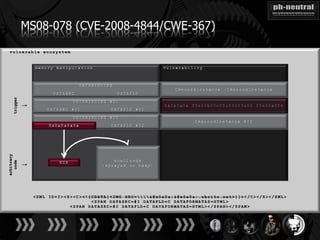
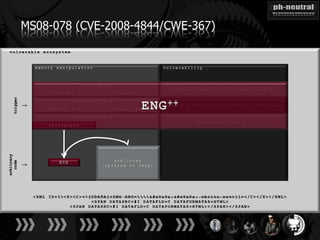
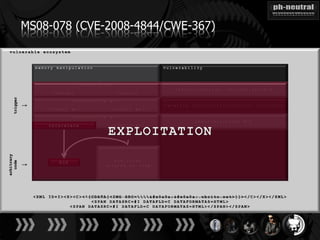
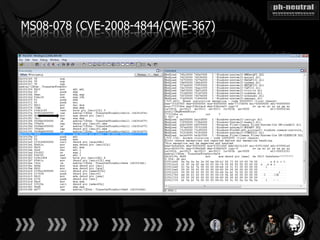
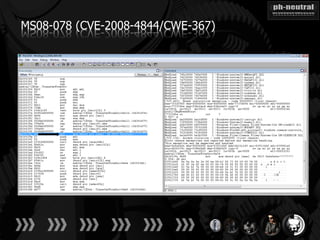
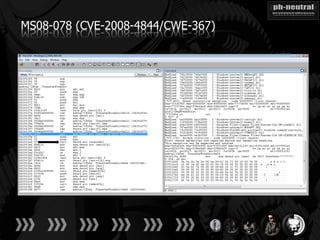
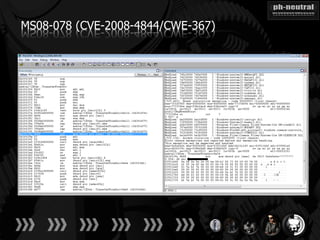
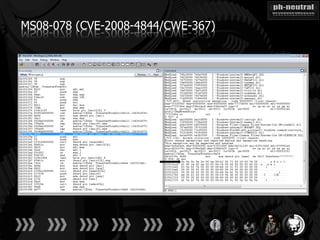
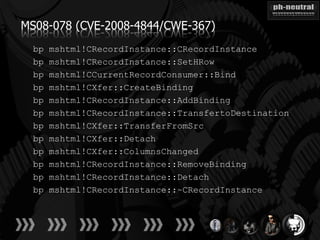
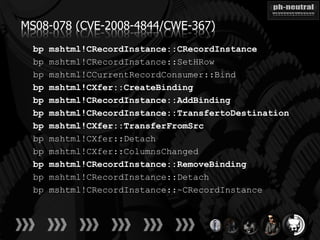
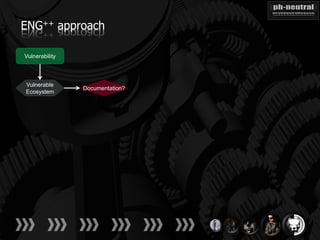
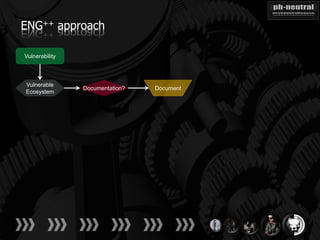
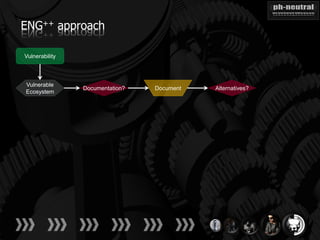
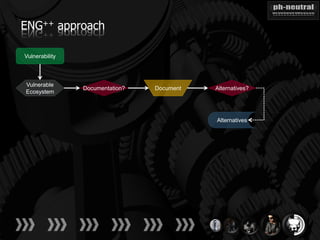
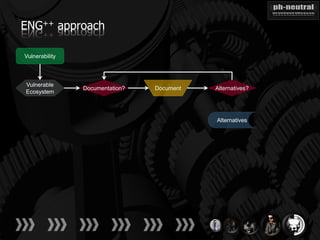
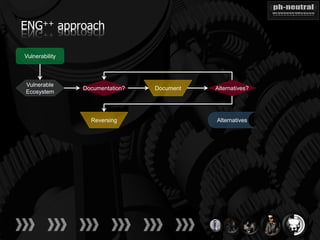
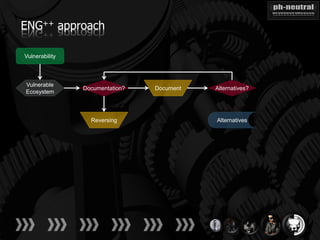
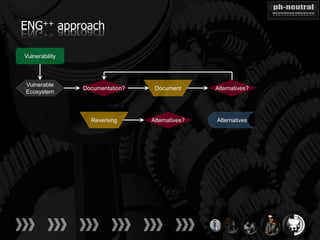
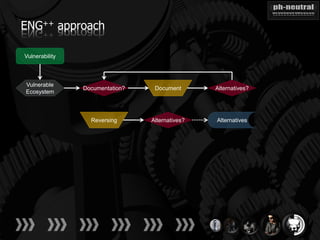
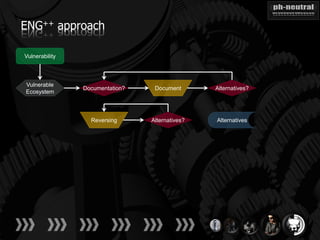
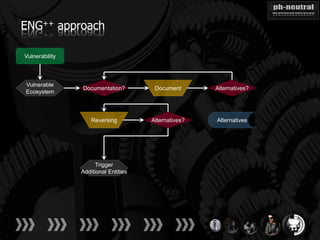
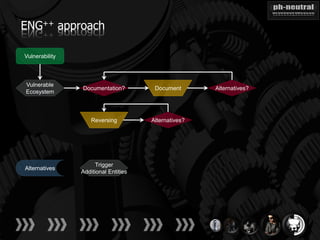
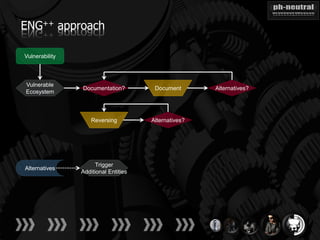
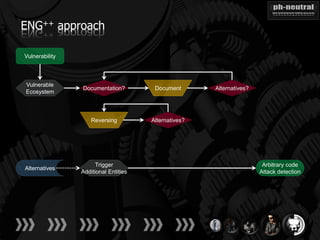
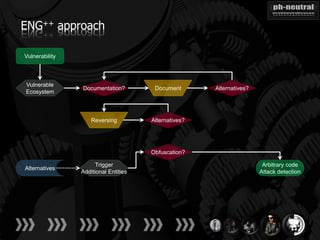
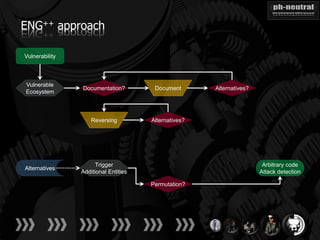
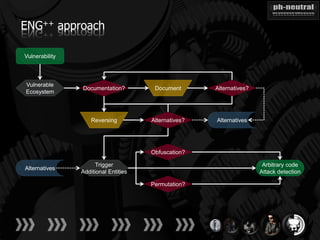
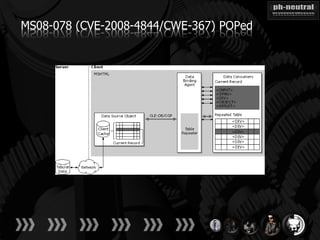
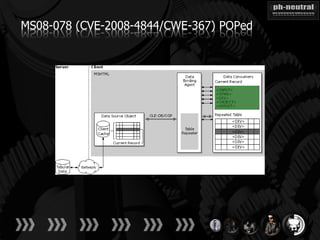
The document discusses the challenges and methodologies related to exploiting 0-day vulnerabilities, focusing on the eng++ approach which utilizes permutation-oriented programming to overcome traditional pattern-matching detection. It highlights various evasion techniques, tools, and examples of server and client-side vulnerabilities such as ms02-039 and ms08-078. The overall aim is to improve exploitation reliability by manipulating vulnerable ecosystems and enhancing the understanding of existing vulnerabilities.






![Current evasion techniques (a.k.a. TT)
Techniques Tools
• Packet fragmentation – Overlapping fragments • Fragroute / Fragrouter
• Stream segmentation – Overlapping segments • ADMutate / ALPHA[2-3] / BETA3 / Others
• Byte and traffic insertion
• Whisker / Nikto / Sandcat
• Polymorphic shellcode
• Snot / Stick / IDS-wakeup / Others
• Denial of Service
• Sidestep / “rpc-evade-poc.pl” / Others
• URL obfuscation (+ SSL encryption)
• “predator”
• RPC fragmentation
• Etc…
• HTML and JavaScript obfuscation
• Etc…](https://image.slidesharecdn.com/ph-neutralnbrito-exploitnextgeneration-110612150913-phpapp01/85/PH-Neutral-0x7db-Exploit-Next-Generation-16-320.jpg)













![[PH-Neutral 0x7db] Exploit Next Generation®](https://image.slidesharecdn.com/ph-neutralnbrito-exploitnextgeneration-110612150913-phpapp01/85/PH-Neutral-0x7db-Exploit-Next-Generation-105-320.jpg)