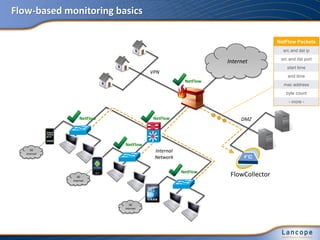
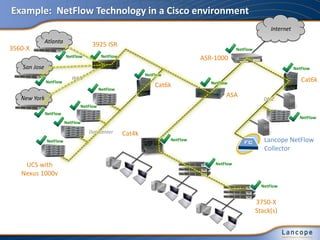
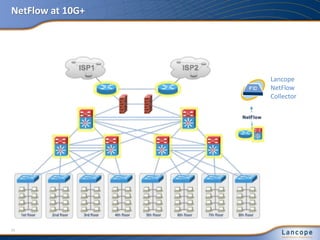
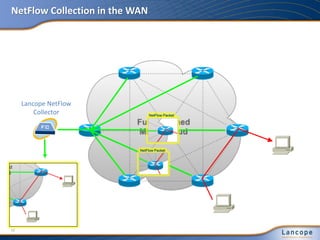
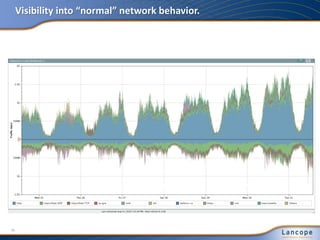
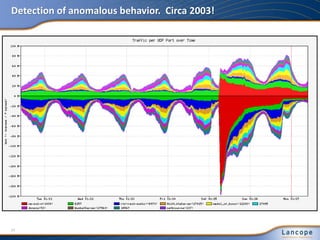
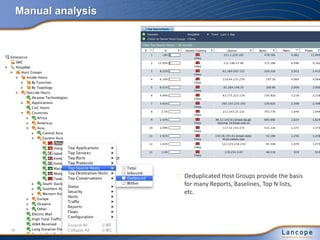
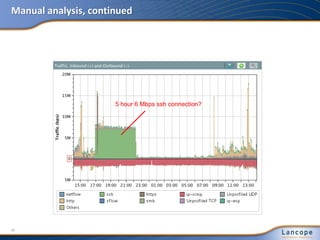
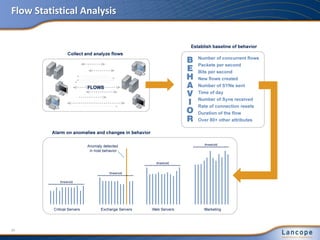
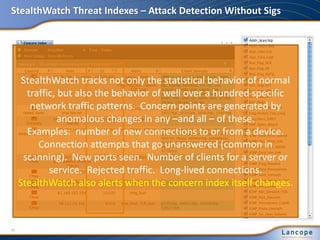
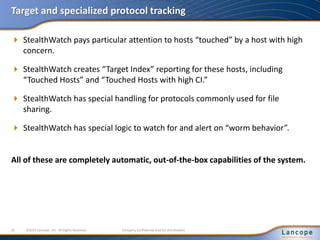
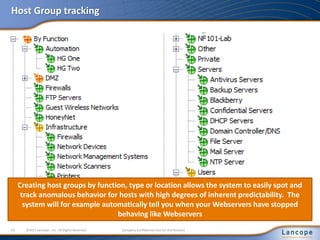
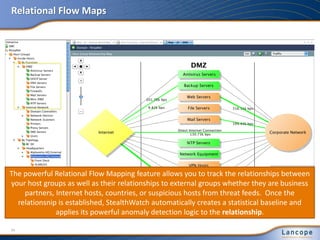
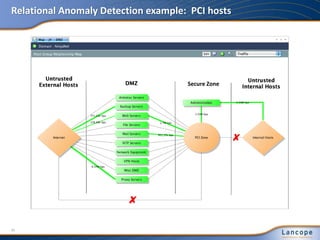
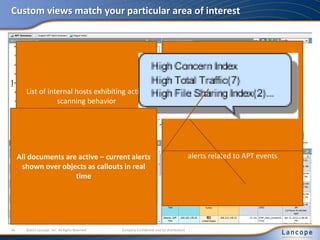
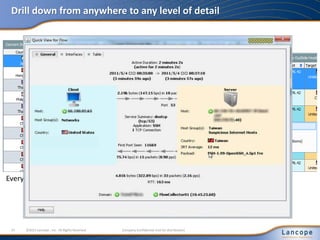
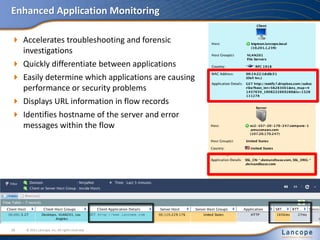
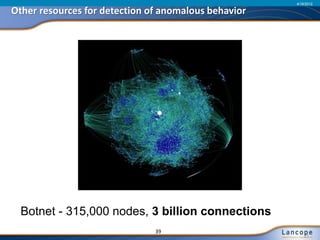
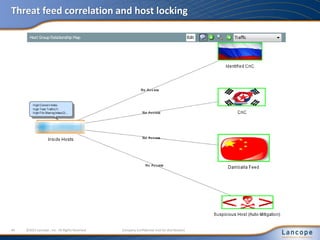
The document discusses advanced persistent threats (APTs), detailing their nature, methods, and impact on organizations, including notable attacks against companies like HBGary and RSA. It highlights the challenges in detecting APTs using traditional security measures and emphasizes the importance of flow-based security monitoring for effective detection and response. The presentation advocates for the adoption of network flow analysis to improve visibility and enhance the ability to identify and mitigate such threats.