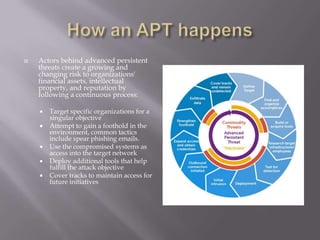
The document discusses advanced persistent threats (APTs) and signs that an organization may have been targeted by an APT. It defines APTs as sophisticated cyber threats, often foreign governments, that target specific entities over an extended period of time. The summary then lists five signs that an APT attack may be occurring: 1) an increase in elevated logins late at night, 2) widespread backdoor Trojans being installed, 3) unexpected information flows within the network, 4) discovery of unexpected large data bundles, and 5) detection of pass-the-hash hacking tools.