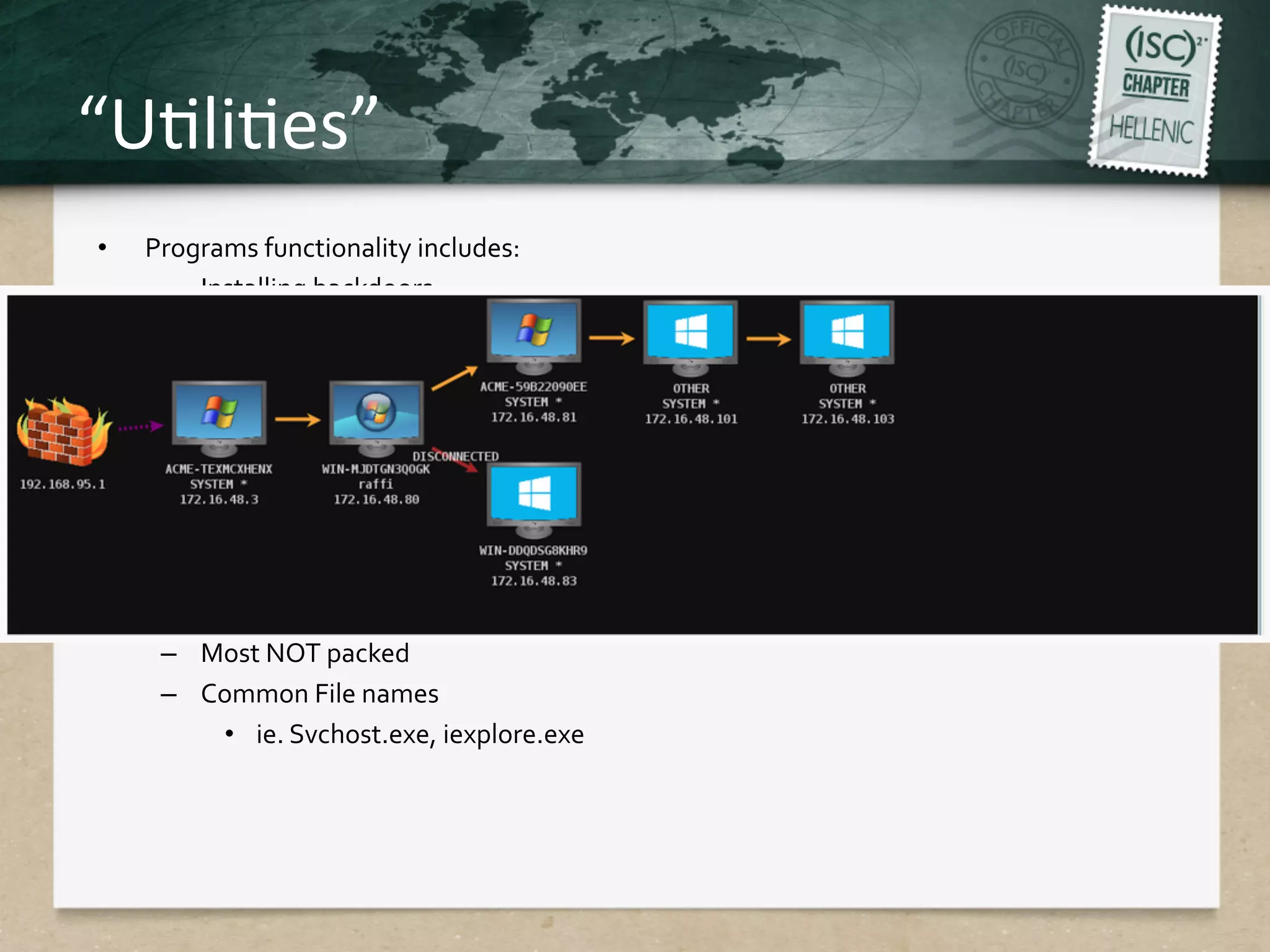
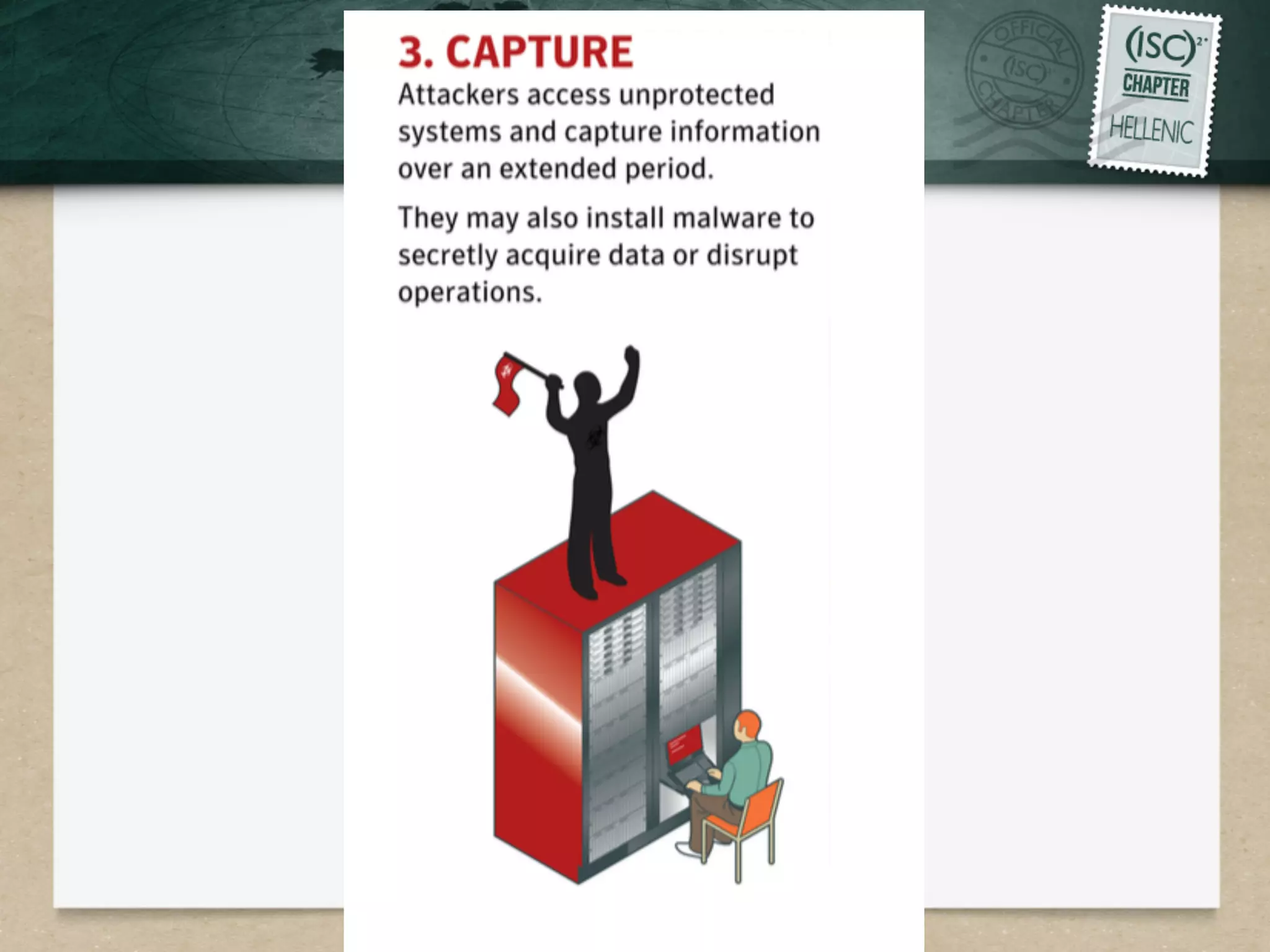
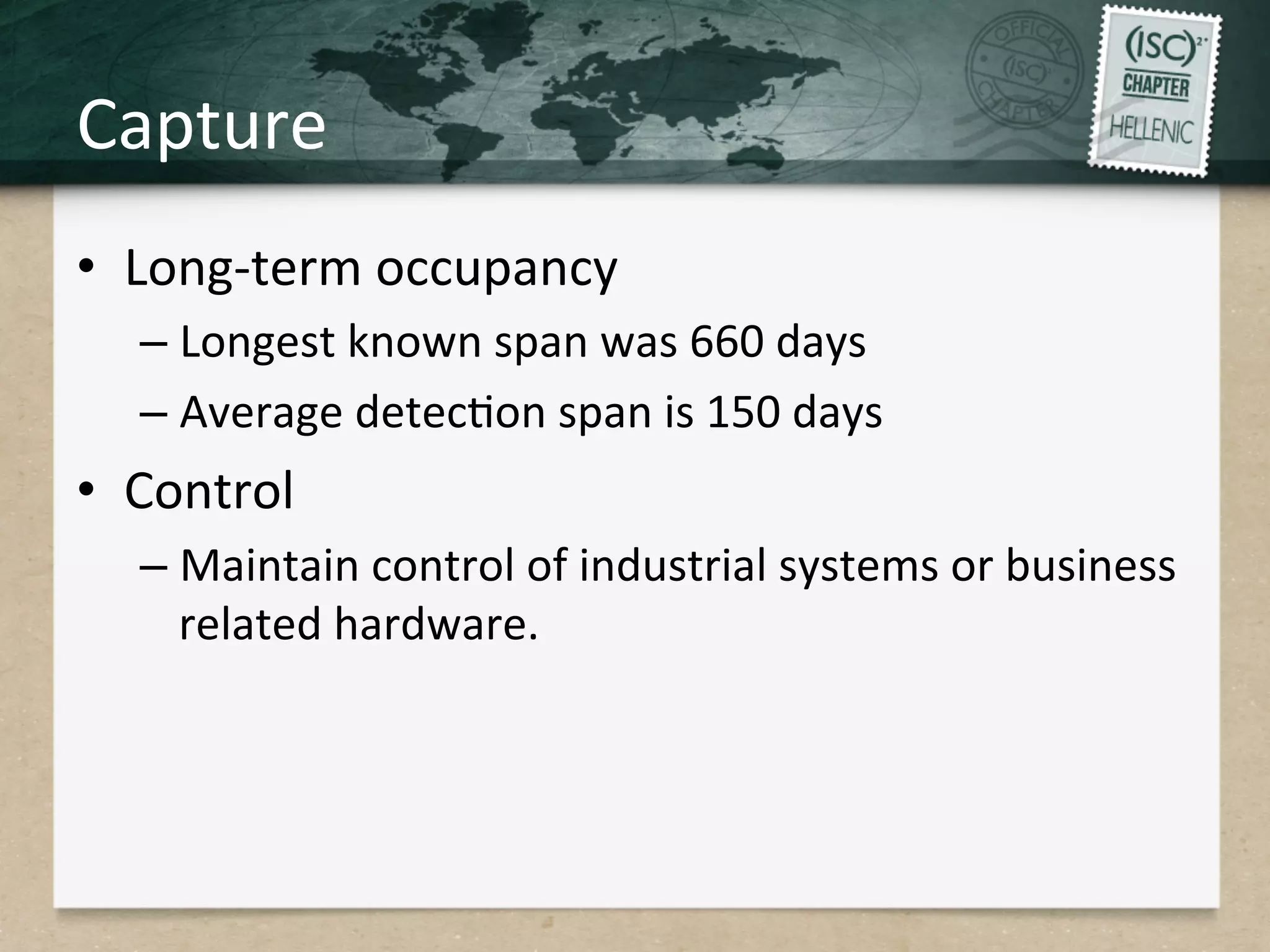
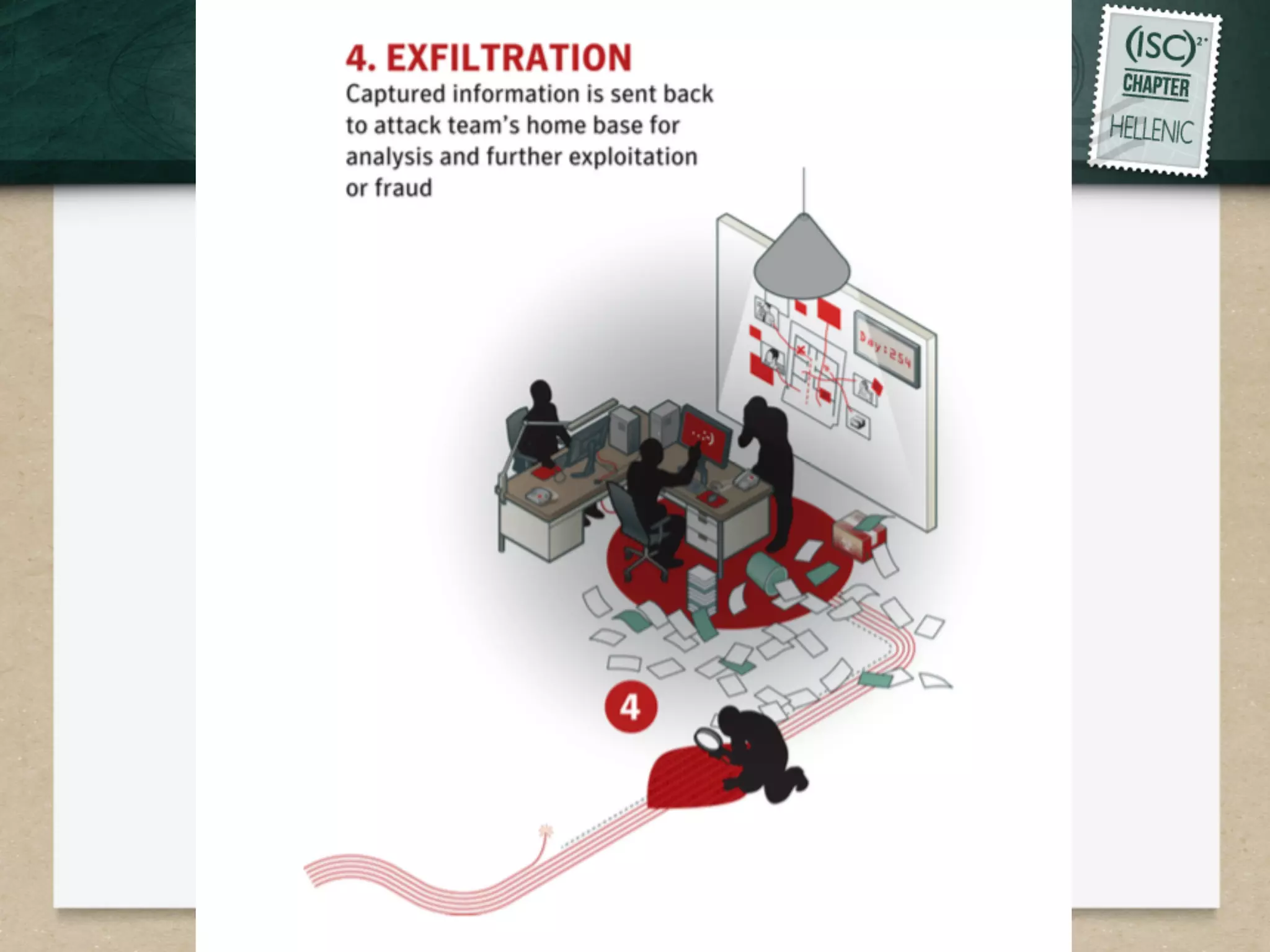
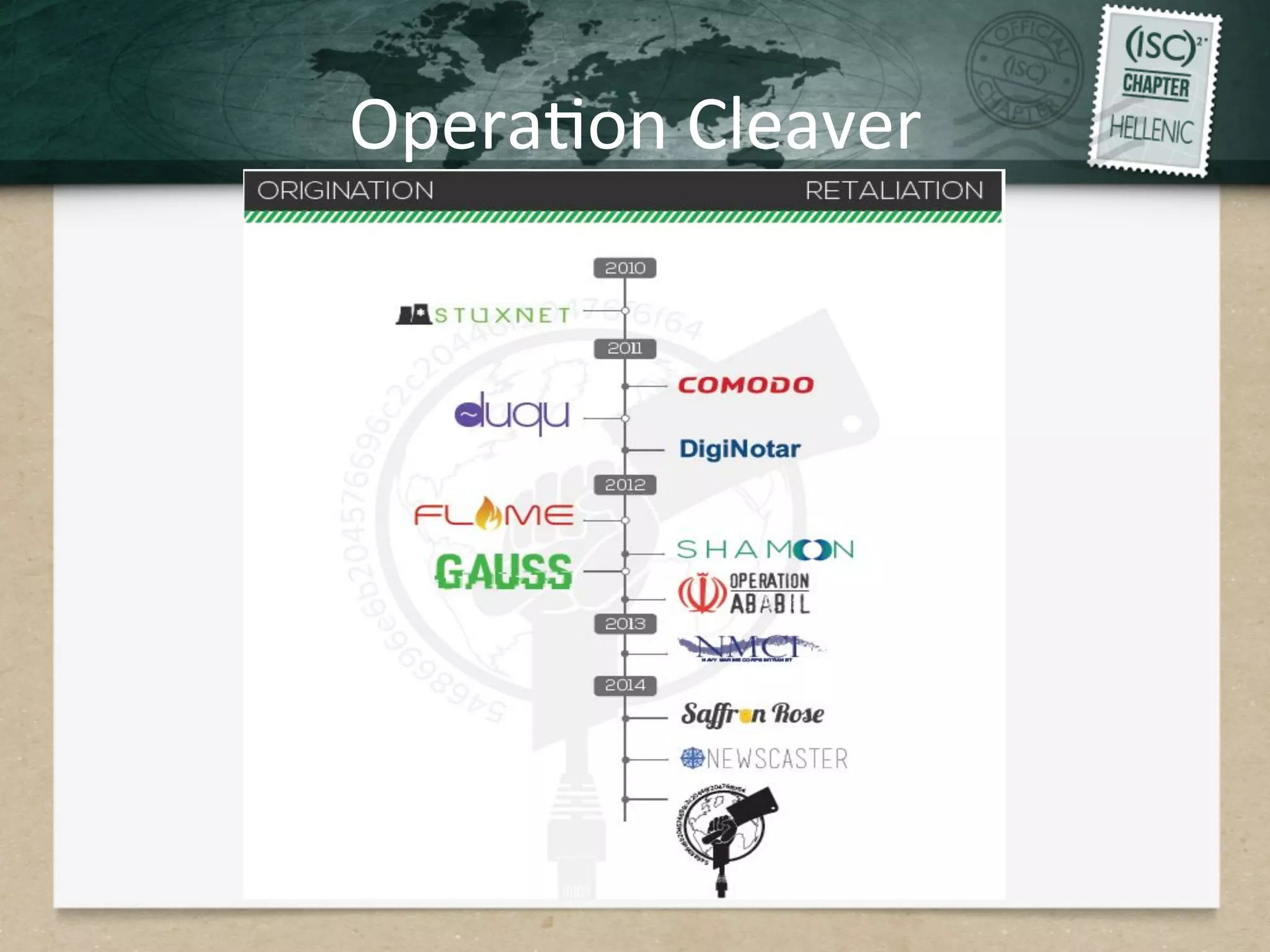
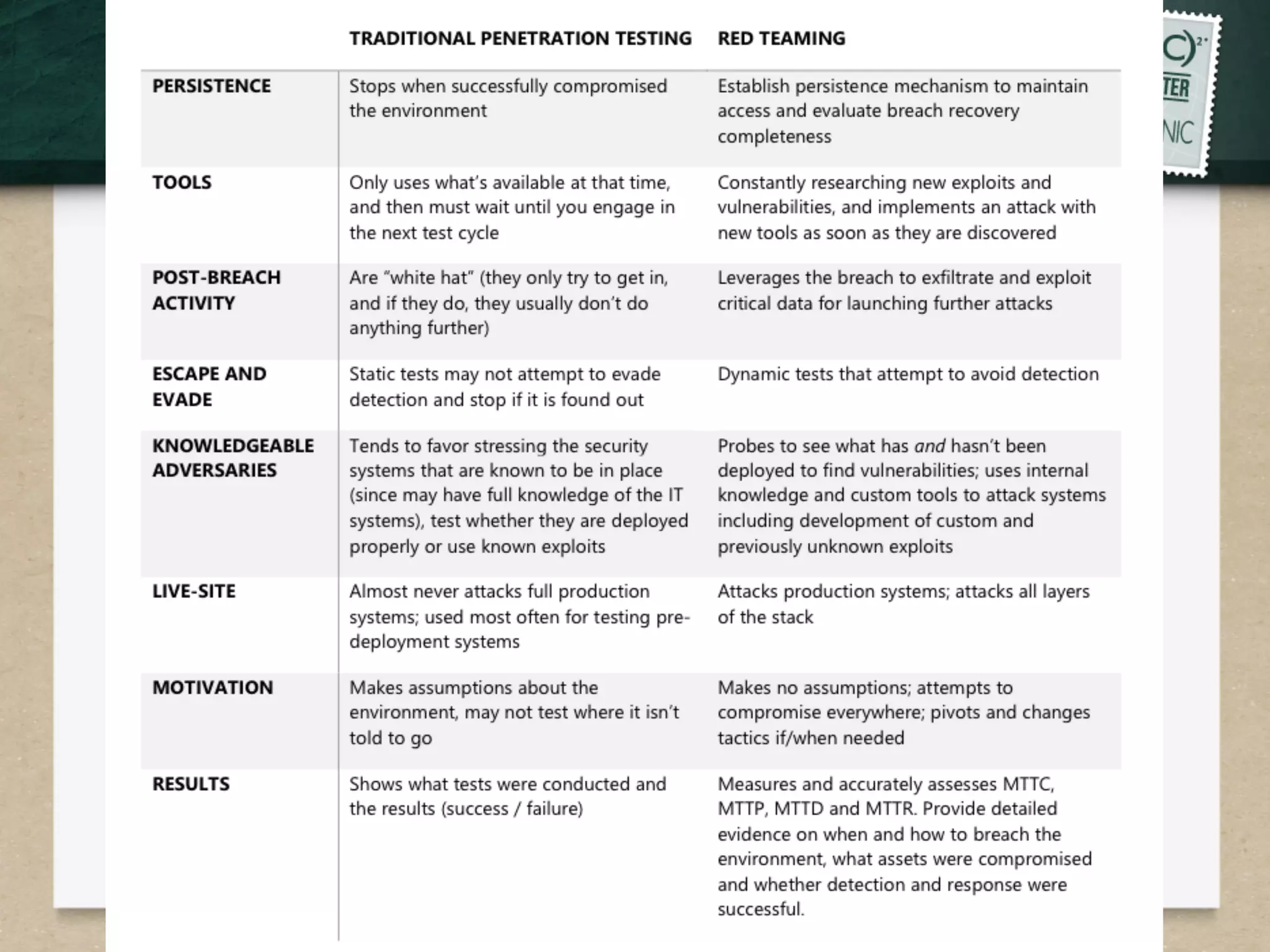
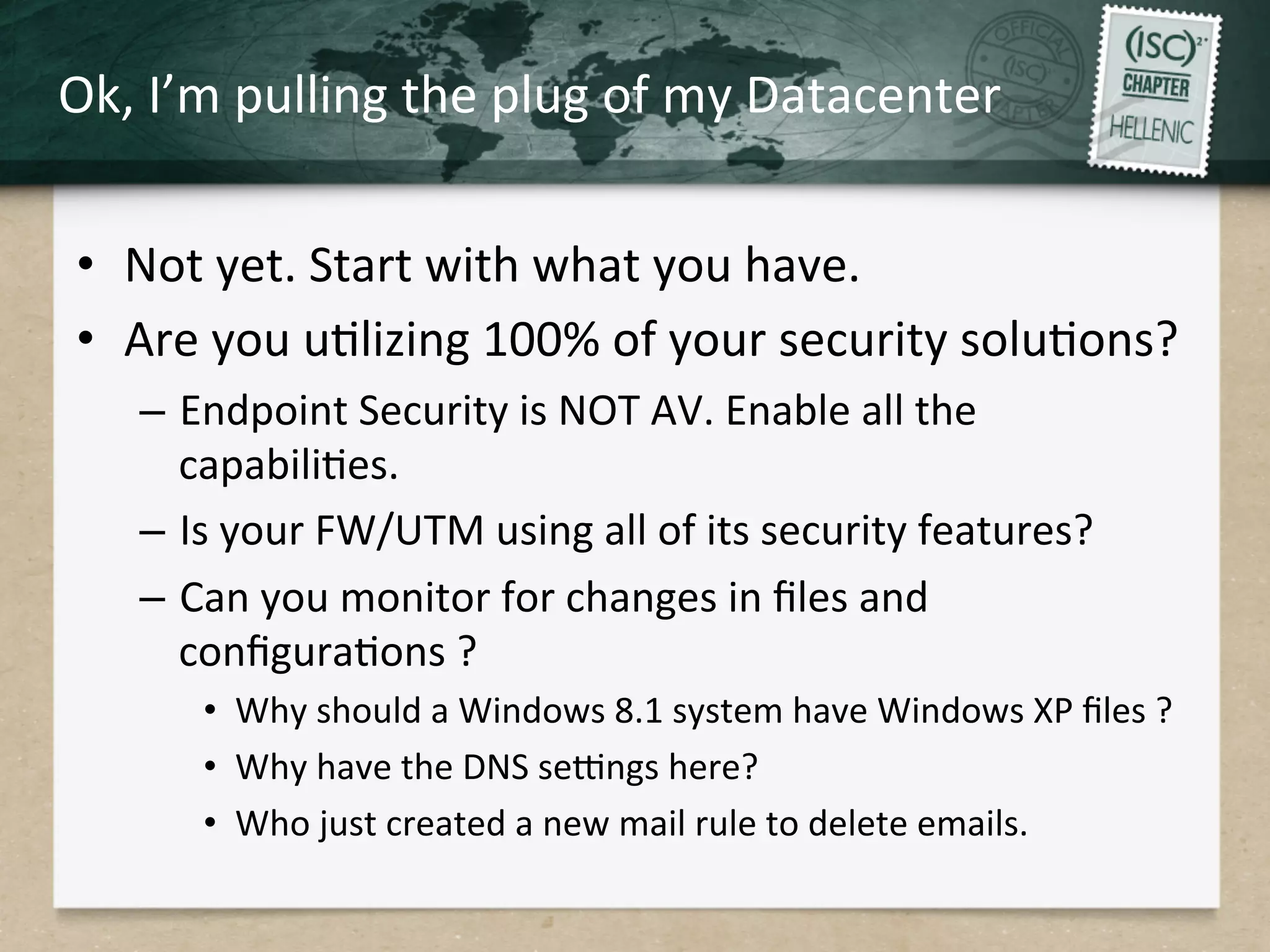
This document discusses advanced persistent threats (APTs) and strategies for cyber defense. It describes APTs as advanced, persistent, and threatening adversaries that are formally tasked to accomplish missions. The document outlines the lifecycle of APT attacks, including establishing backdoors in networks, maintaining long-term control, and exfiltrating data using encryption. It provides examples of APT groups and tools they use, such as exploiting vulnerabilities to escalate privileges and dump cached credentials from Windows networks. The overall summary is that APTs are dangerous, organized adversaries requiring persistent cyber defense strategies.













![IdenQty
Protect
Detect
Respond
Recover
NIST
Categories
FuncQon
What
are
my
assets,
risks
and
business
goals?
Asset
Mgmt
Business
Environment
Governance
Risk
Assessment
Risk
Mgmt
Strategy
What
are
my
safeguards
to
block
aackers?
Access
Control
Training
Data
Security
Processes
Maintenance
ProtecQve
Technology
How
do
I
know
when
a
security
event
has
happened?
Anomalies
and
Events
ConQnuous
Monitoring
DetecQon
Processes
How
do
I
respond
to
a
cyber
security
event?
Response
Planning
CommunicaQons
Analysis
MiQgaQon
Improvement
How
do
I
restore
services
a]er
an
event?
Recovery
Planning
Improvements
CommunicaQons
NIST
Cybersecurity
Framework
Summary
The
framework
provides
a
consensus
descripQon
of
what's
needed
for
a
comprehensive
cybersecurity
program,
and
allows
organizaQons—regardless
of
size,
degree
of
cyber
risk
or
cybersecurity
sophisQcaQon—to
apply
the
principles
and
best
pracQces
of
risk
management
to
improve
the
security
and
resilience
of
criQcal
infrastructure](https://image.slidesharecdn.com/3-141221191249-conversion-gate01/75/3-APTs-Presentation-27-2048.jpg)