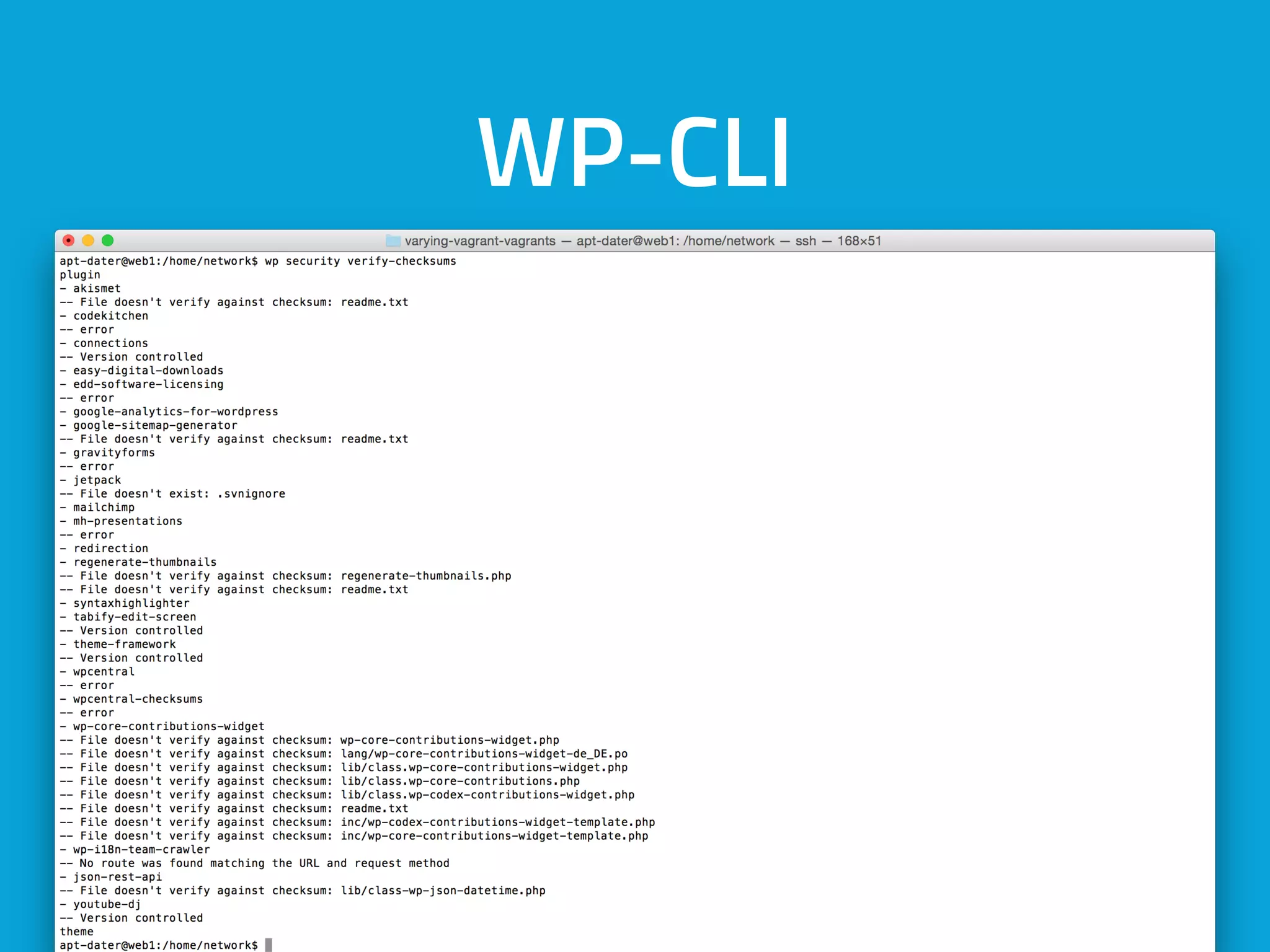
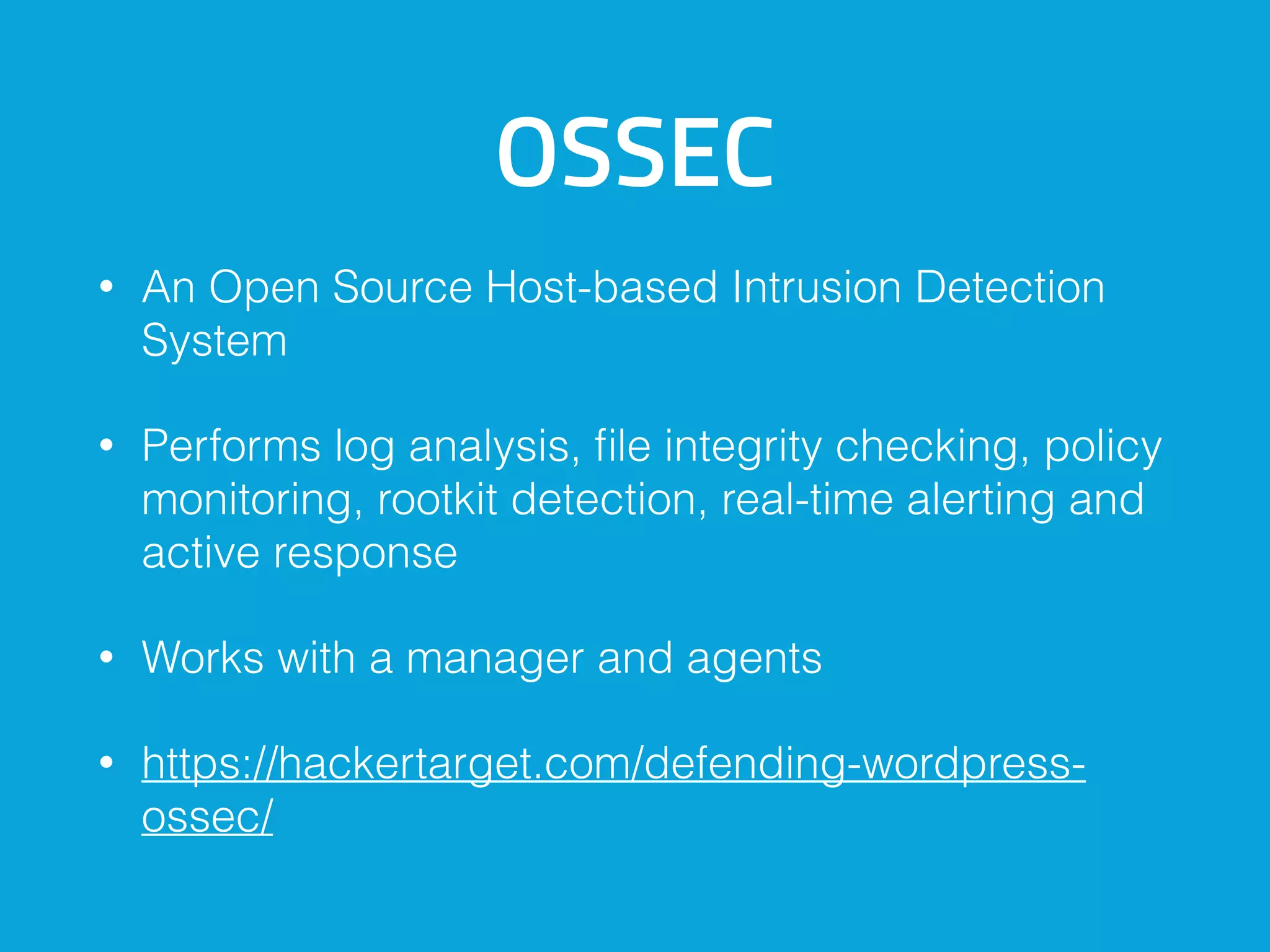
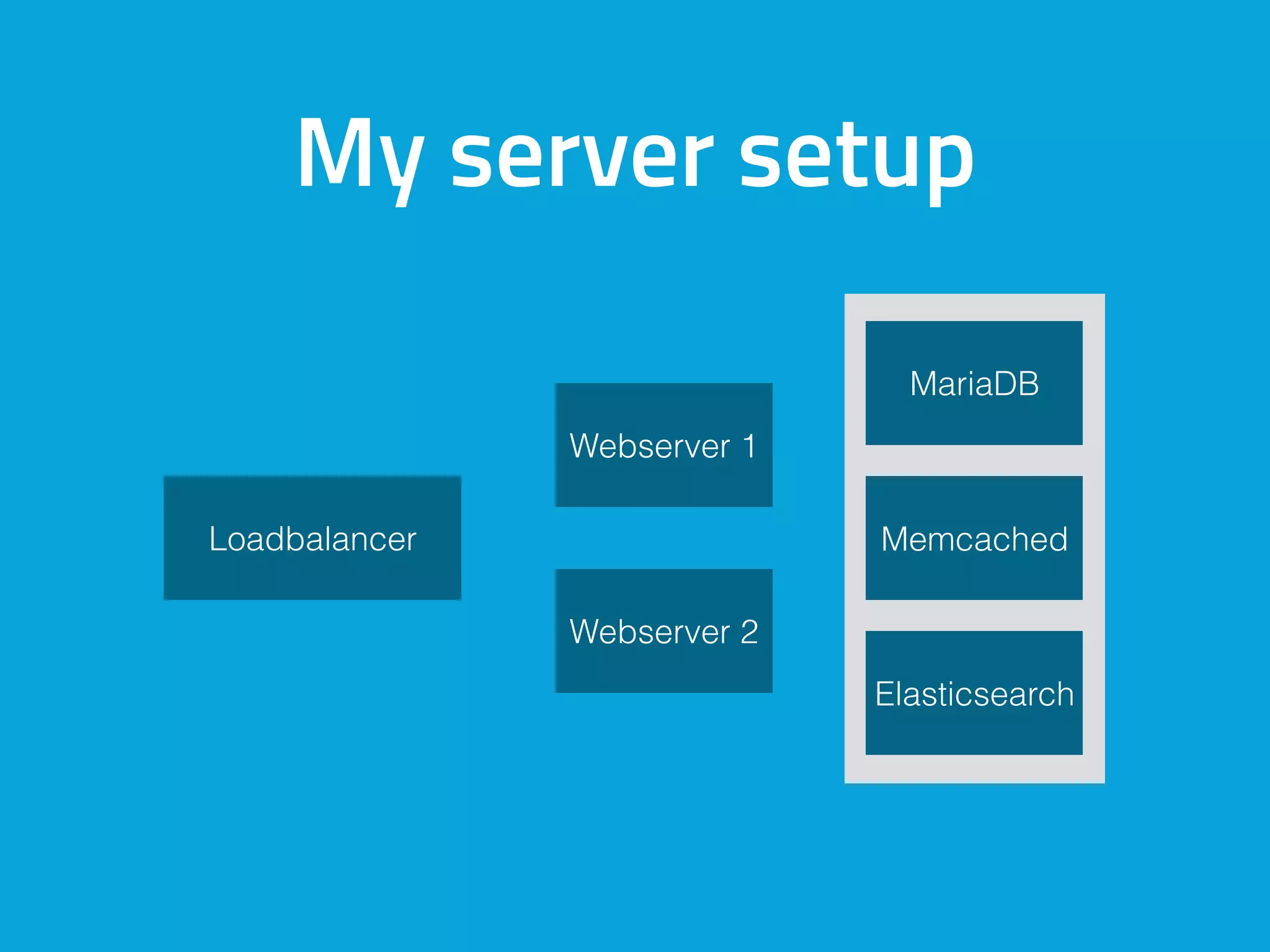
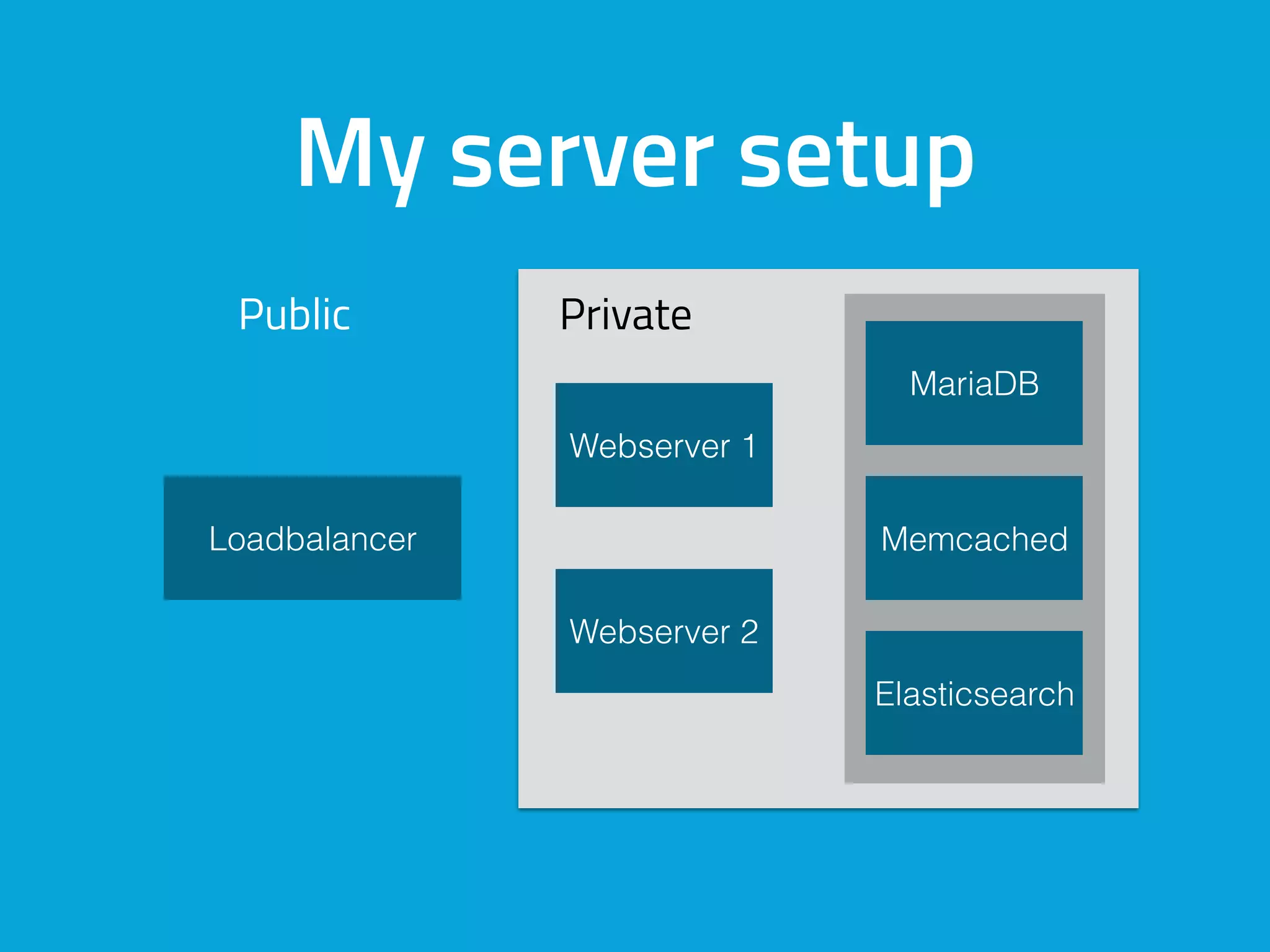
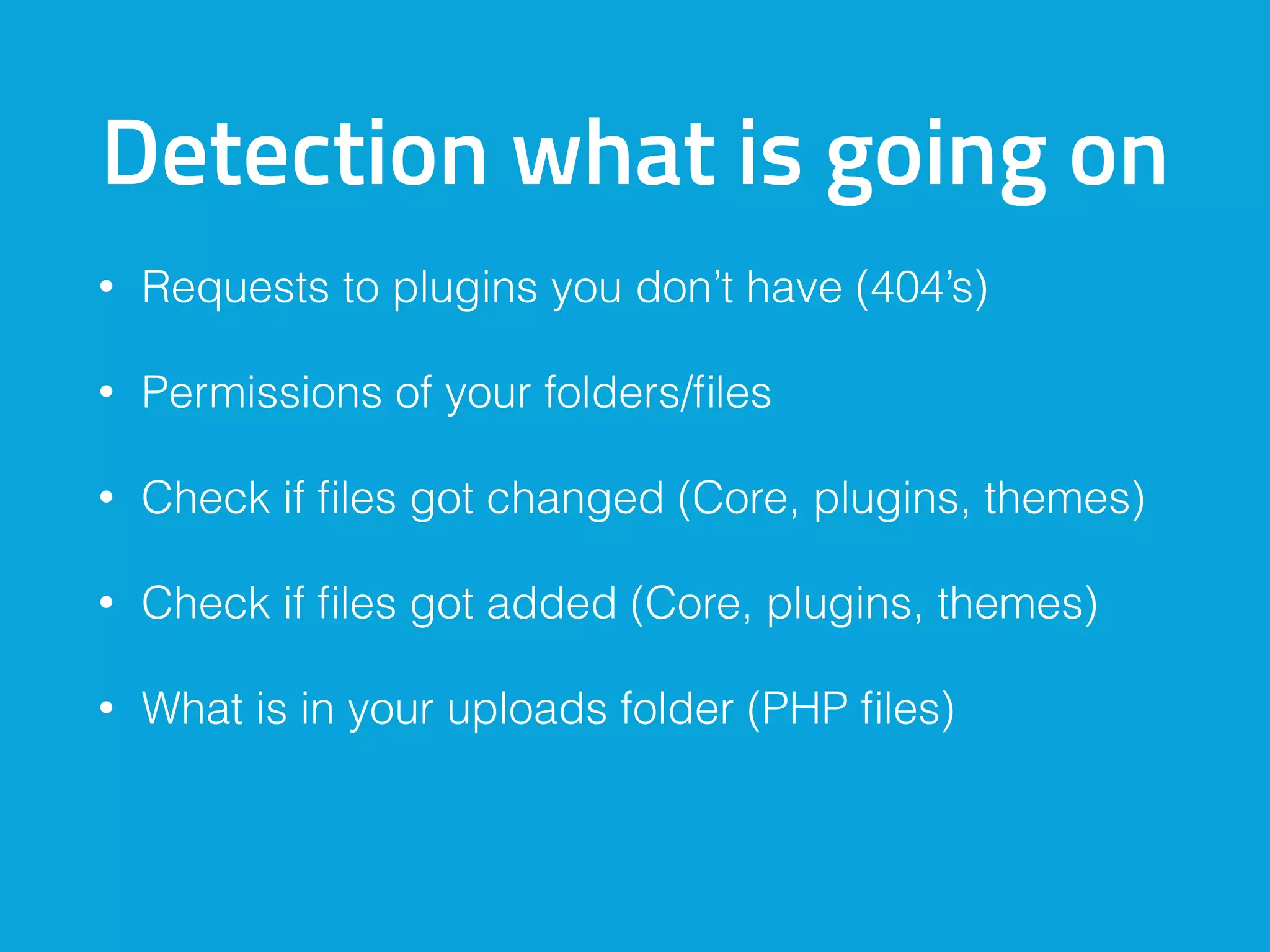
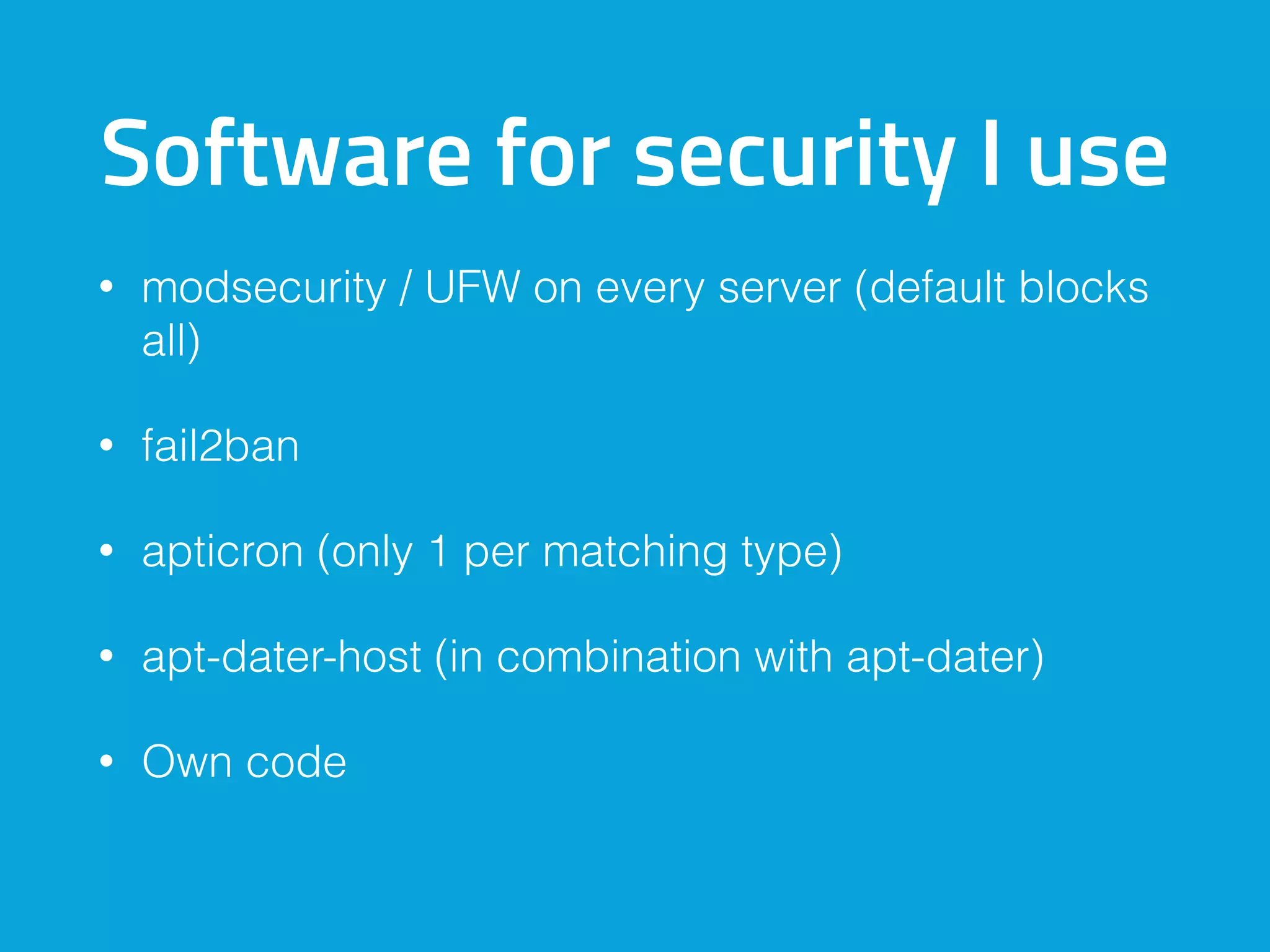
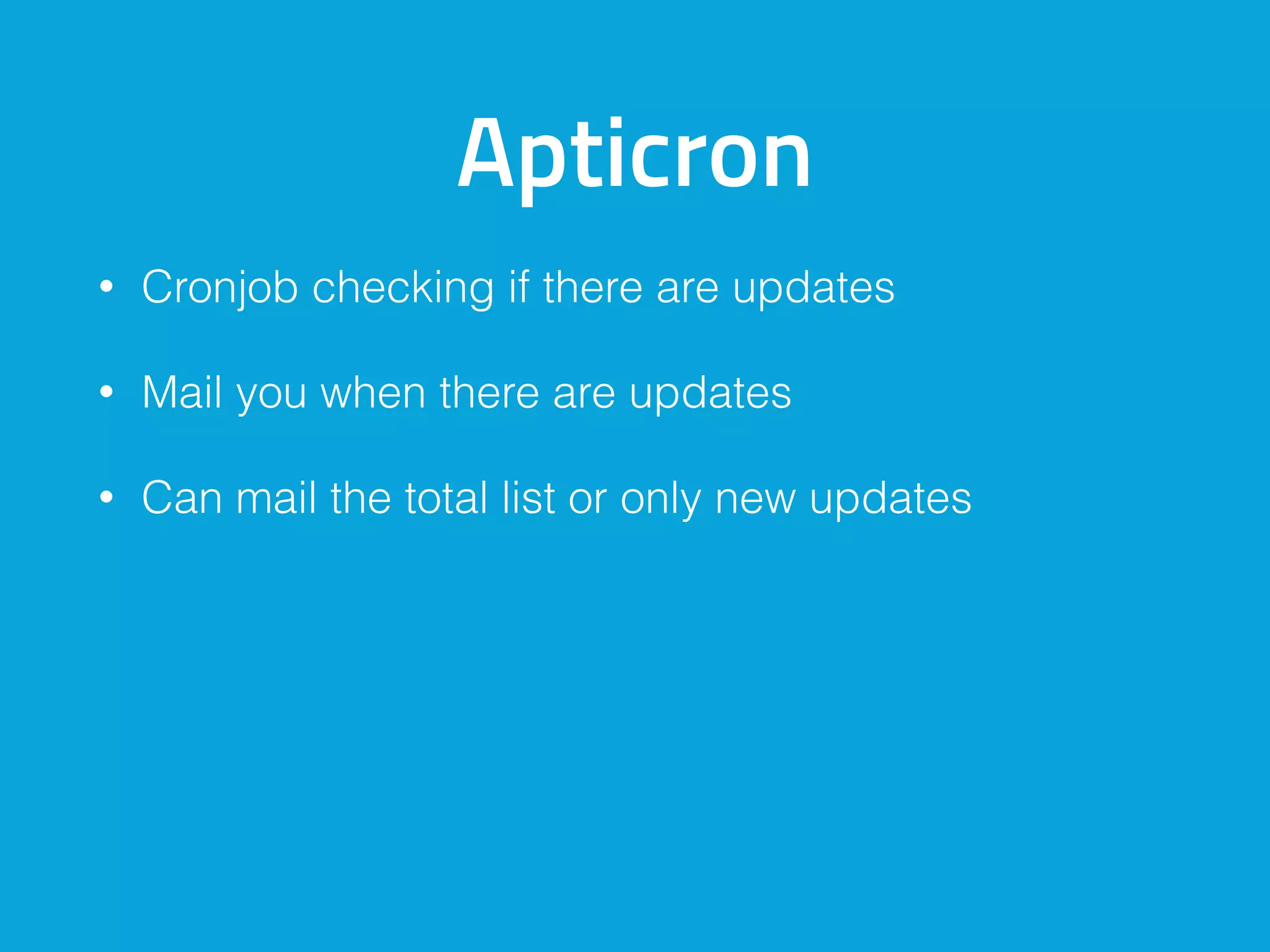
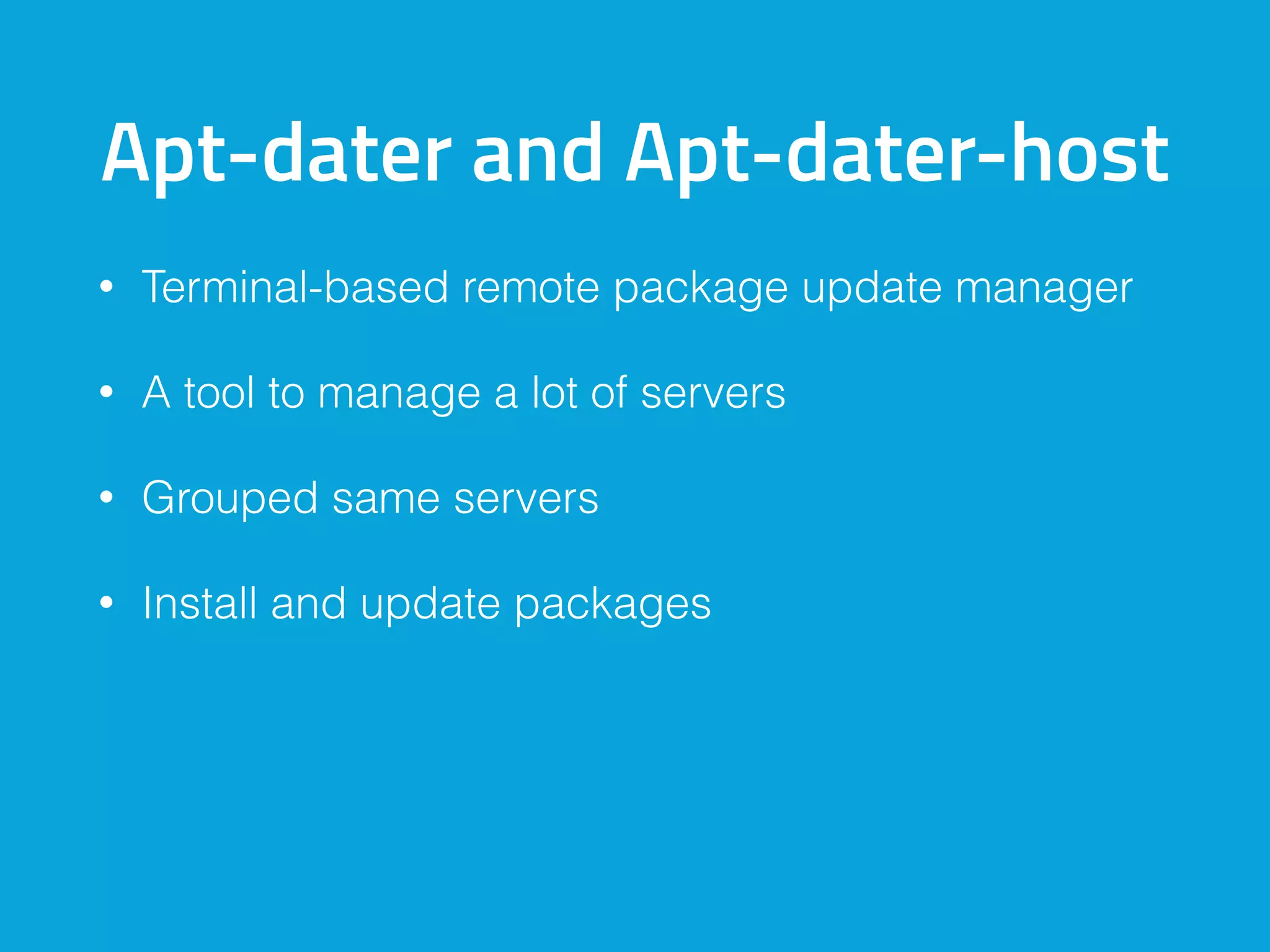
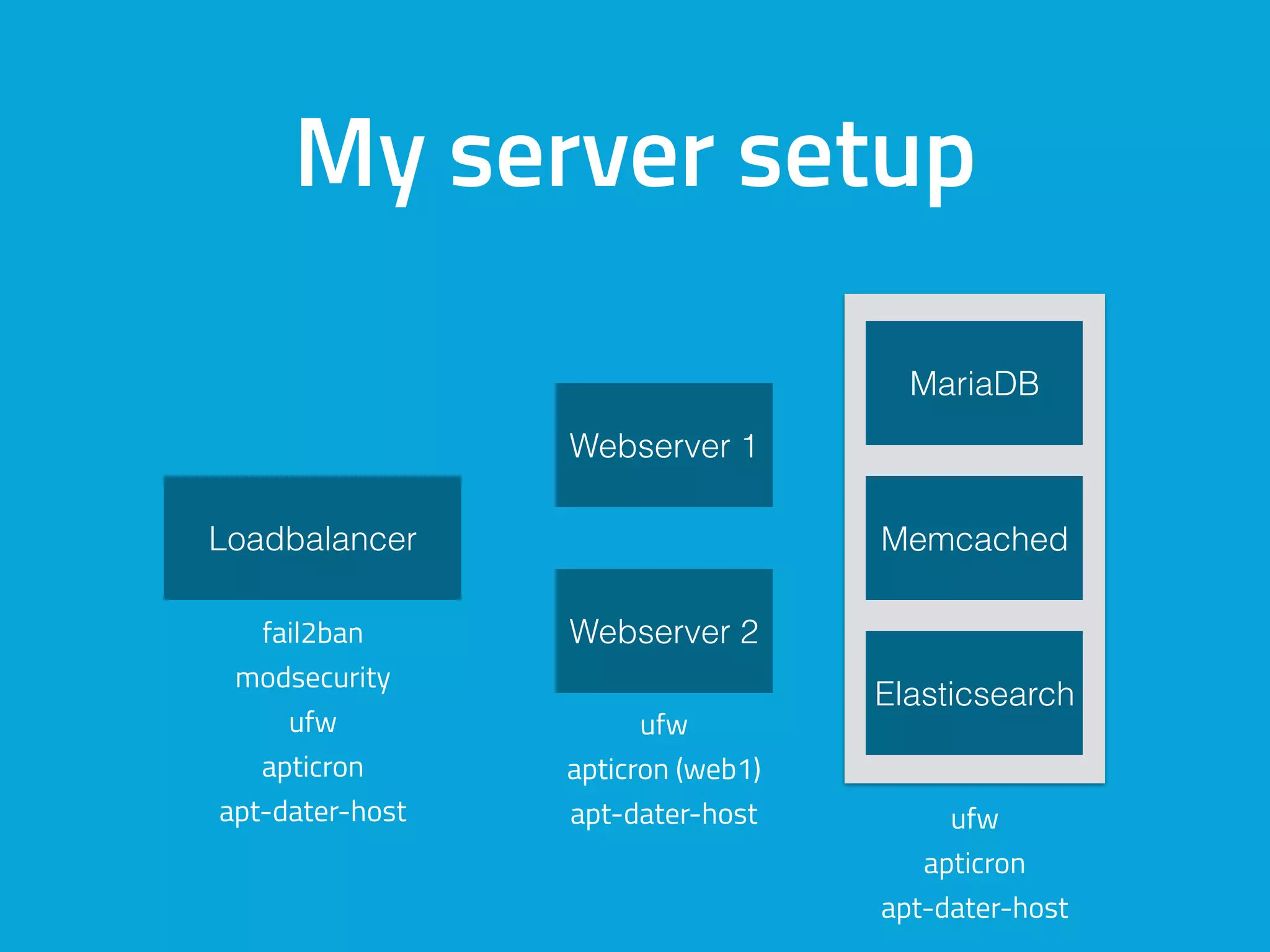
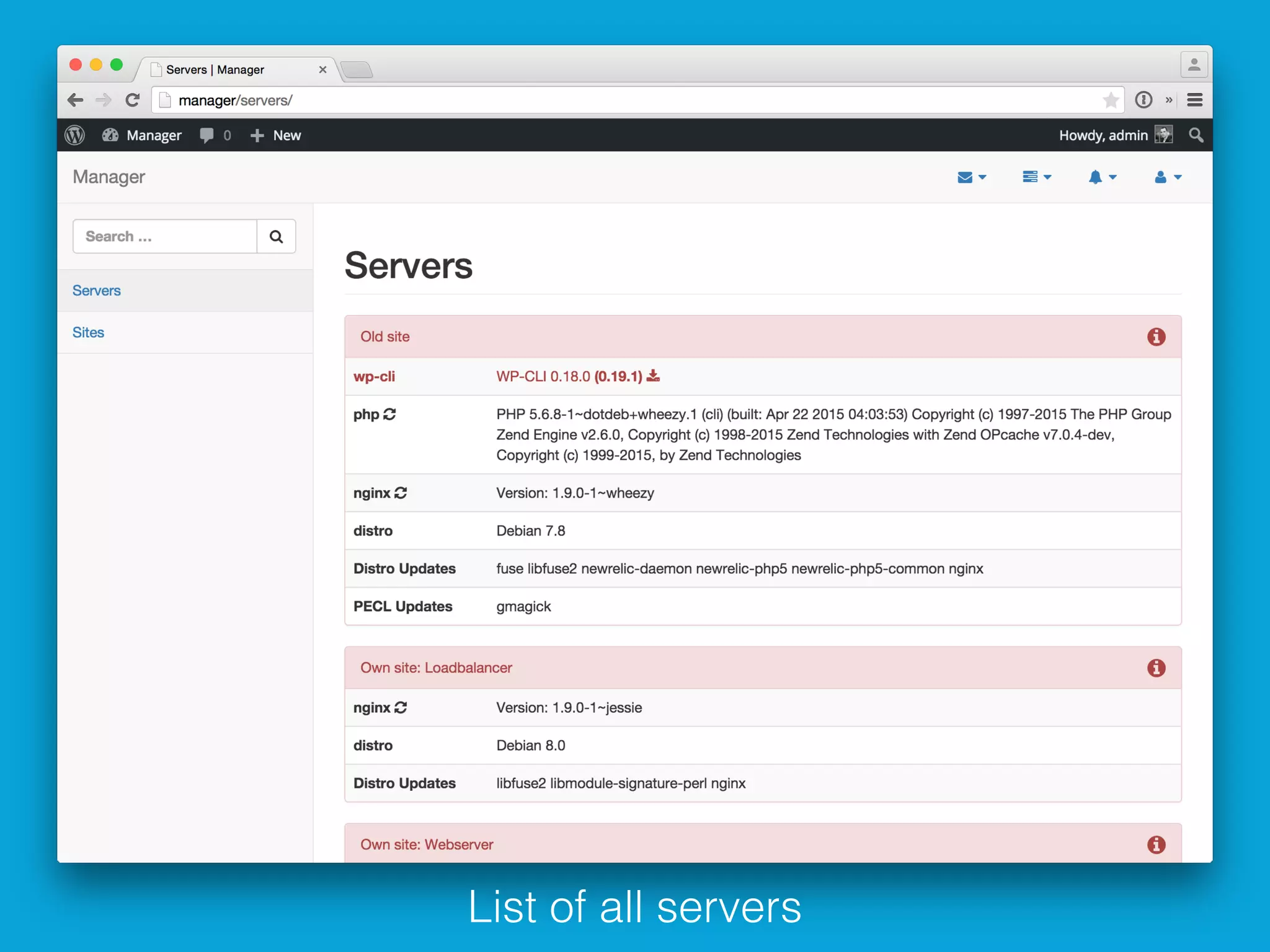
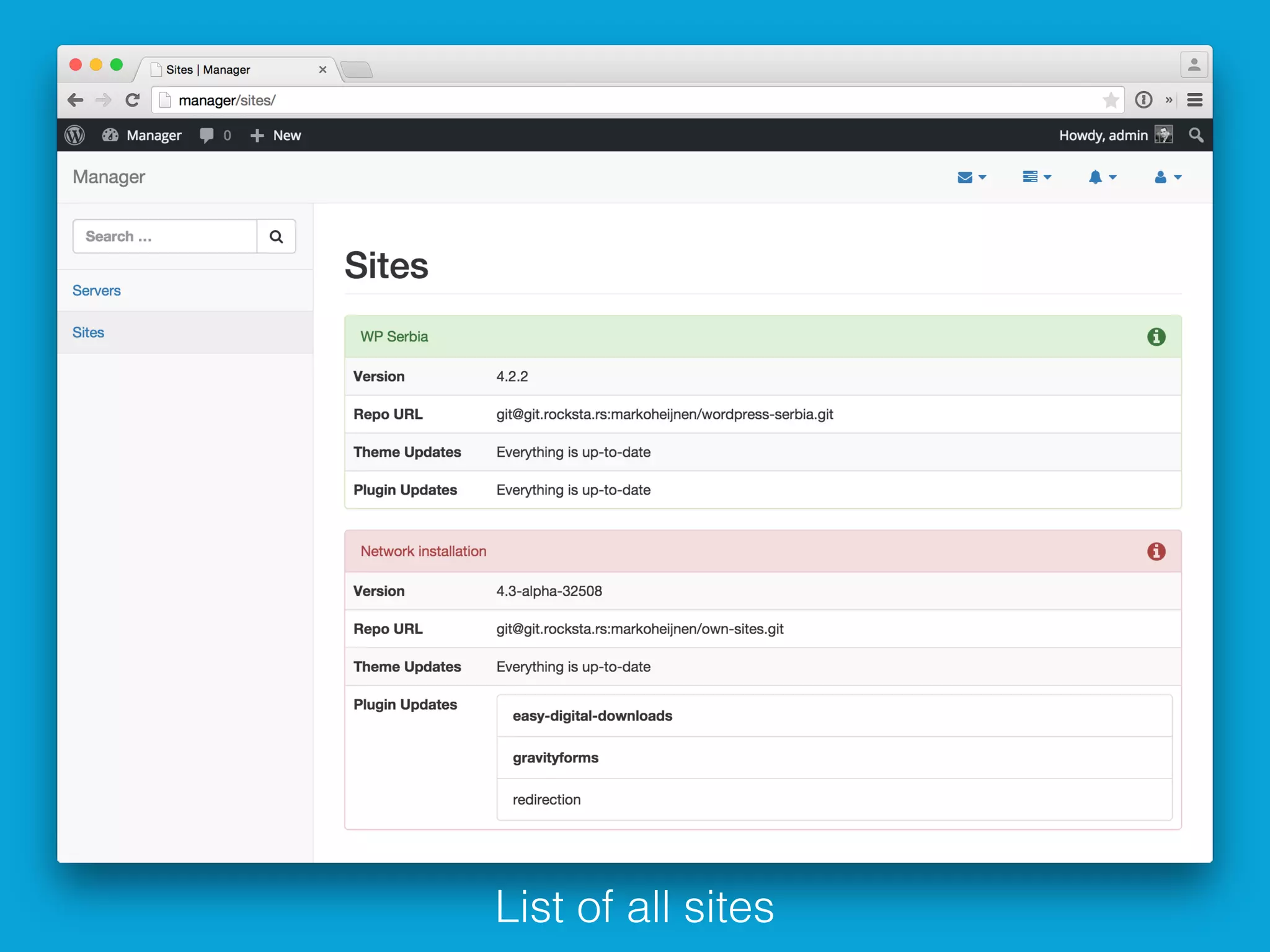
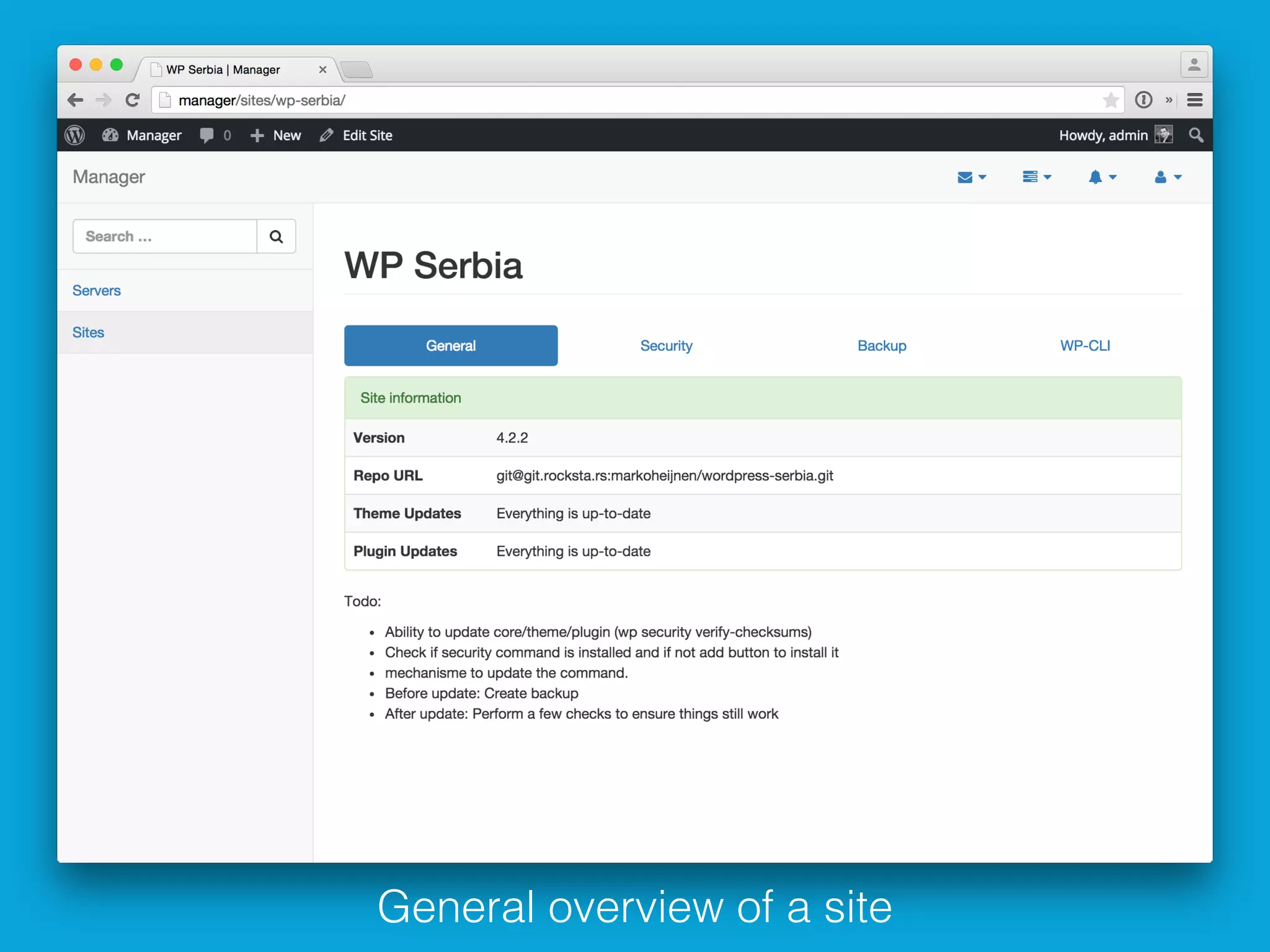
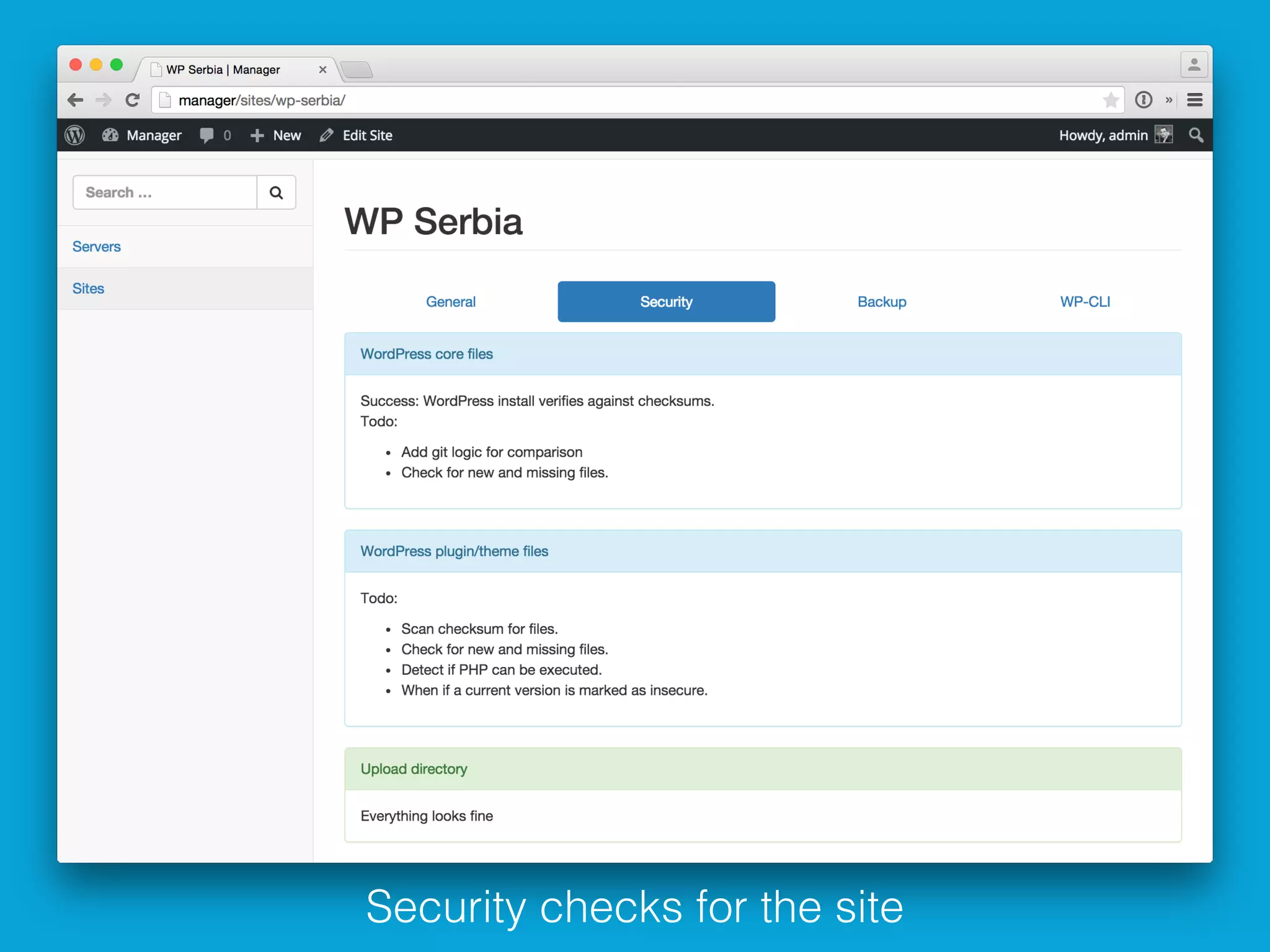
This document discusses ways to detect security issues on a WordPress site and server. It recommends using tools like ModSecurity, fail2ban, Apticron, and Apt-dater to monitor for updates, failed login attempts, and other security events. It also proposes building a WordPress plugin called WP Central that would aggregate security data from all sites and servers and provide a central dashboard. The plugin would monitor files, permissions, login attempts, and perform checksum scans to detect any changes or additions.

















![WP Central API
• http://wpcentral.io/api/checksums/theme/
twentyfifteen/1.2
• [{"code":"wpcentral_server_error","message":"Gener
ating checksums”}]
• [{"file":"header.php","checksum":"c0919b5f4b6e4f3a
58b858b2305e9146"},{},{},{},{},{},{},{},{},{},{},{},{},{}]](https://image.slidesharecdn.com/protectingyoursitebydetection-150512220105-lva1-app6892/75/Protecting-your-site-by-detection-31-2048.jpg)