Embed presentation
Download to read offline





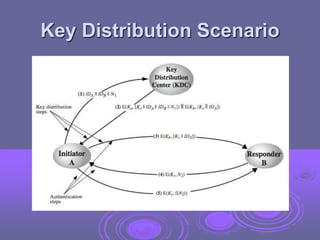


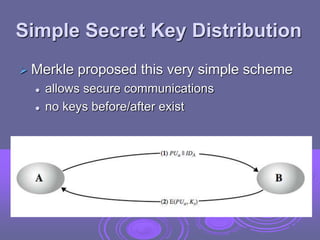

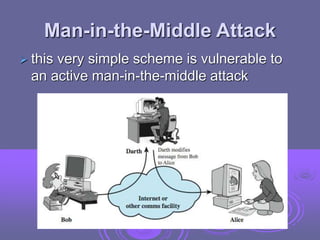
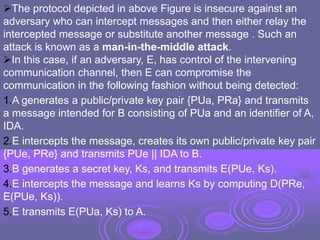
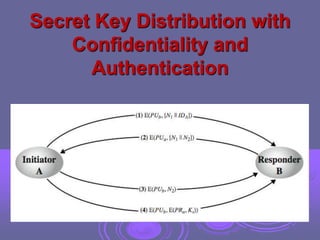






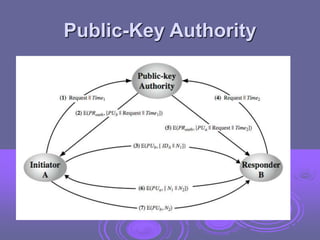

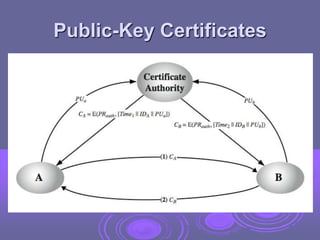

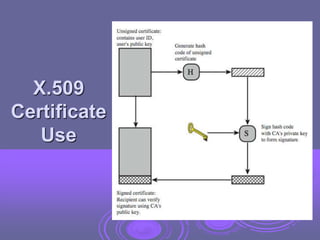

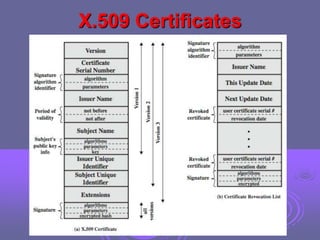


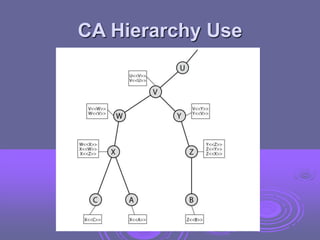



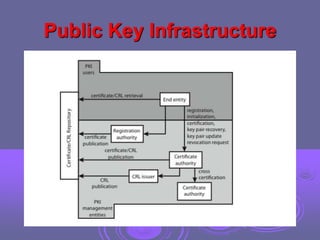





This document discusses key management and distribution. It covers several methods for distributing symmetric keys including physical delivery, using a third party, and encrypting new keys with previous keys. It also discusses distributing asymmetric keys through public announcement, directories, authorities, and certificates. X.509 certificates are described as binding a user's identity to their public key through a digital signature from a certification authority (CA). CA hierarchies are discussed to allow validation of certificates across different CAs.












































