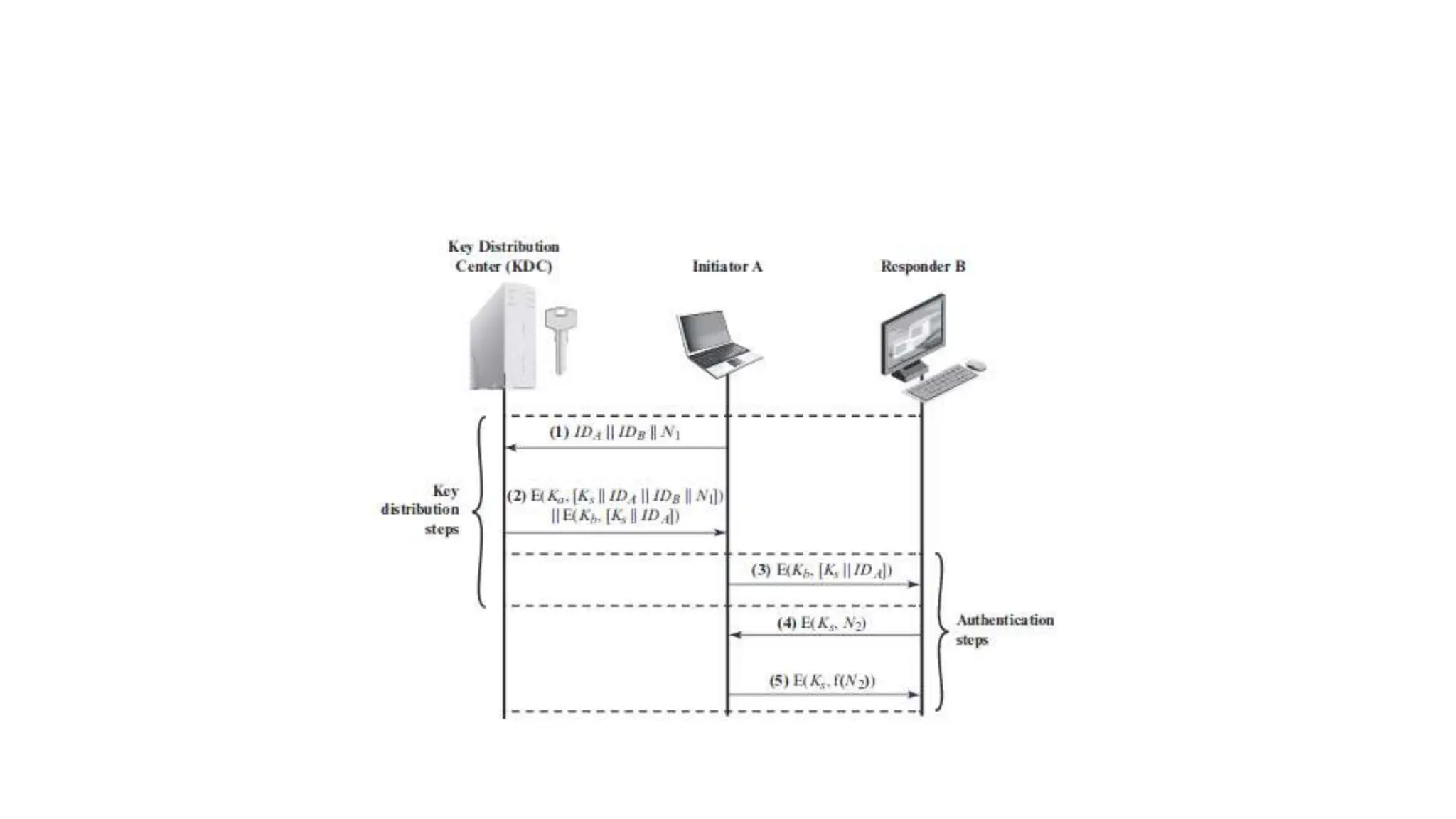
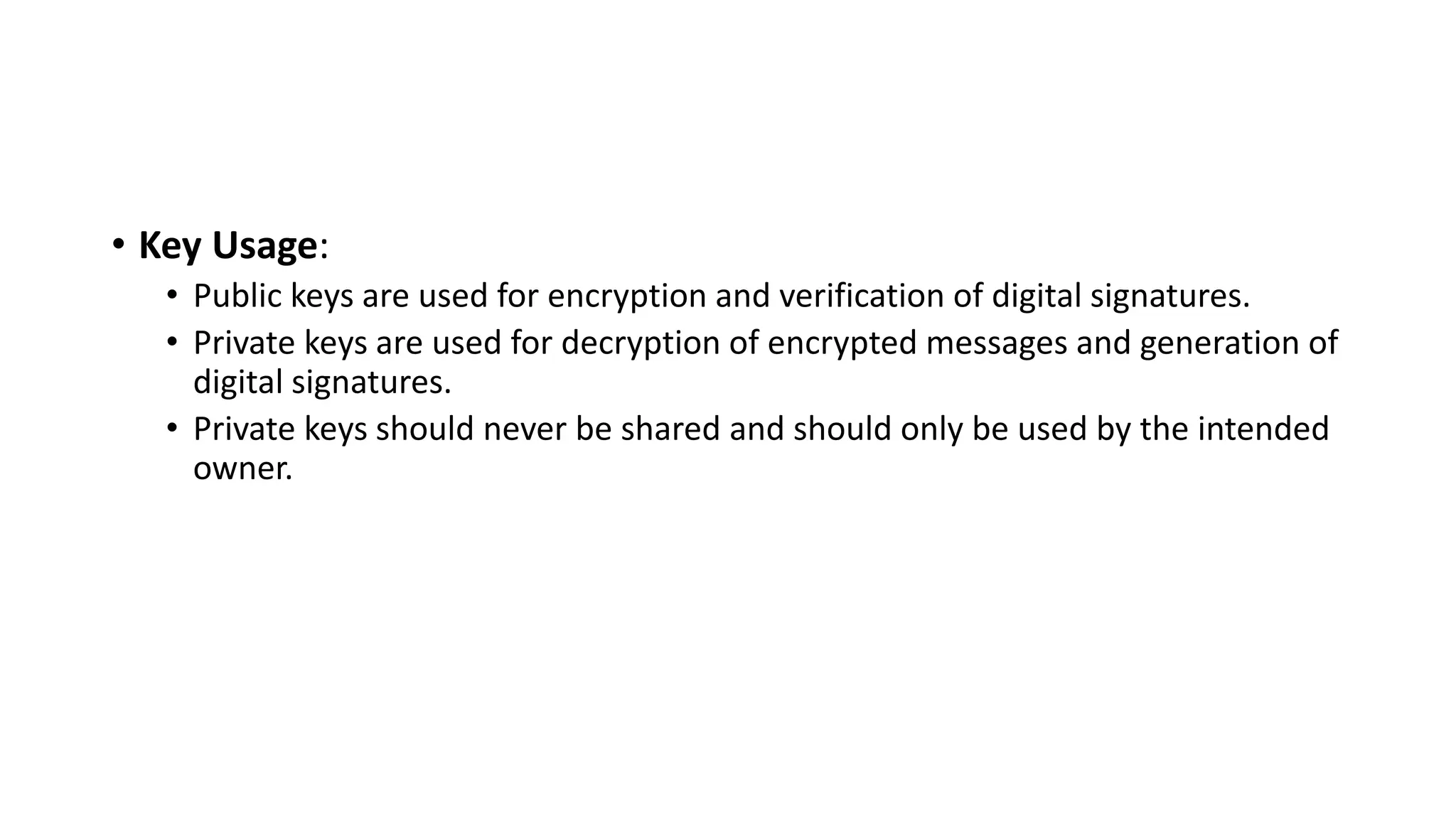
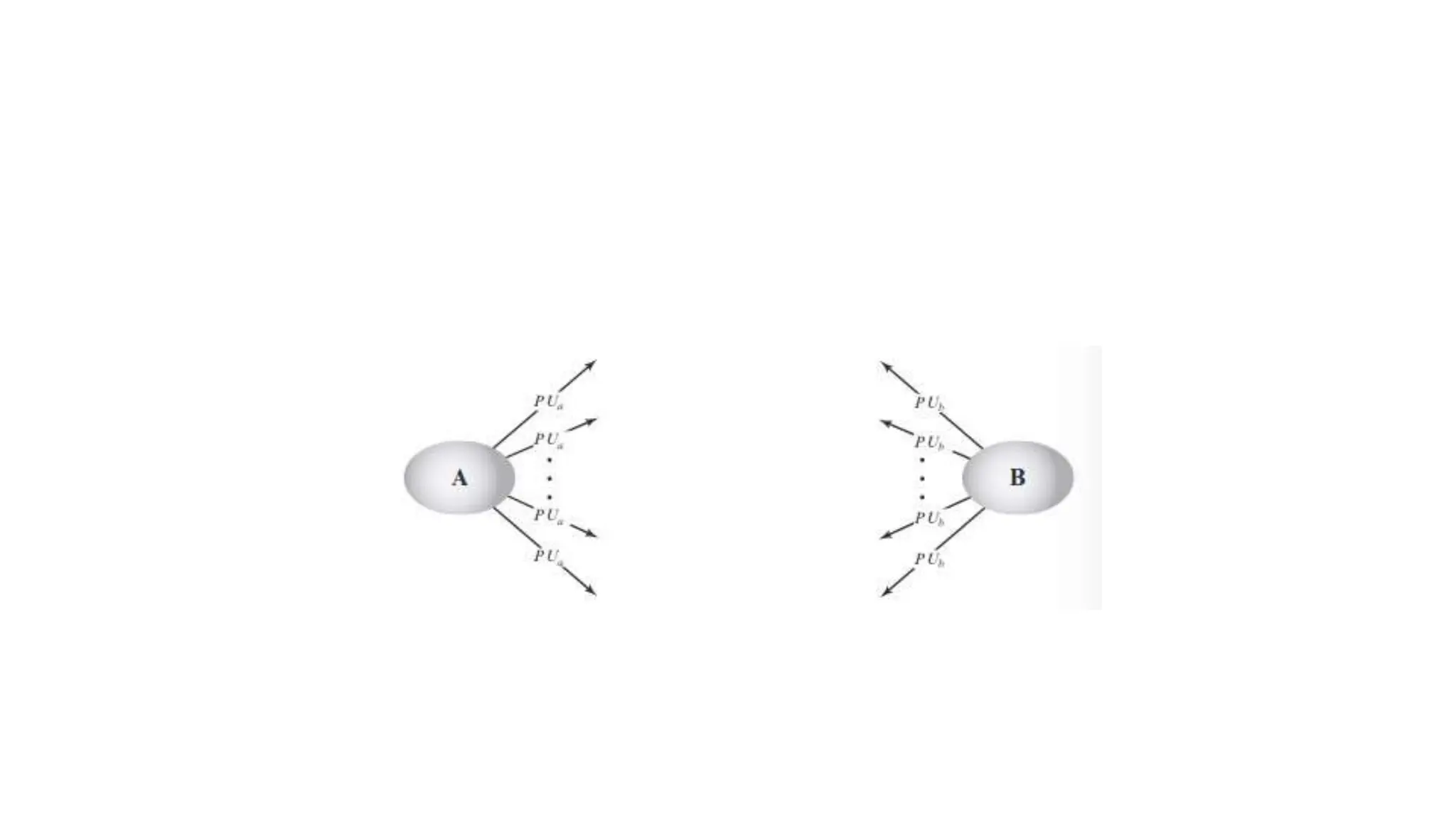
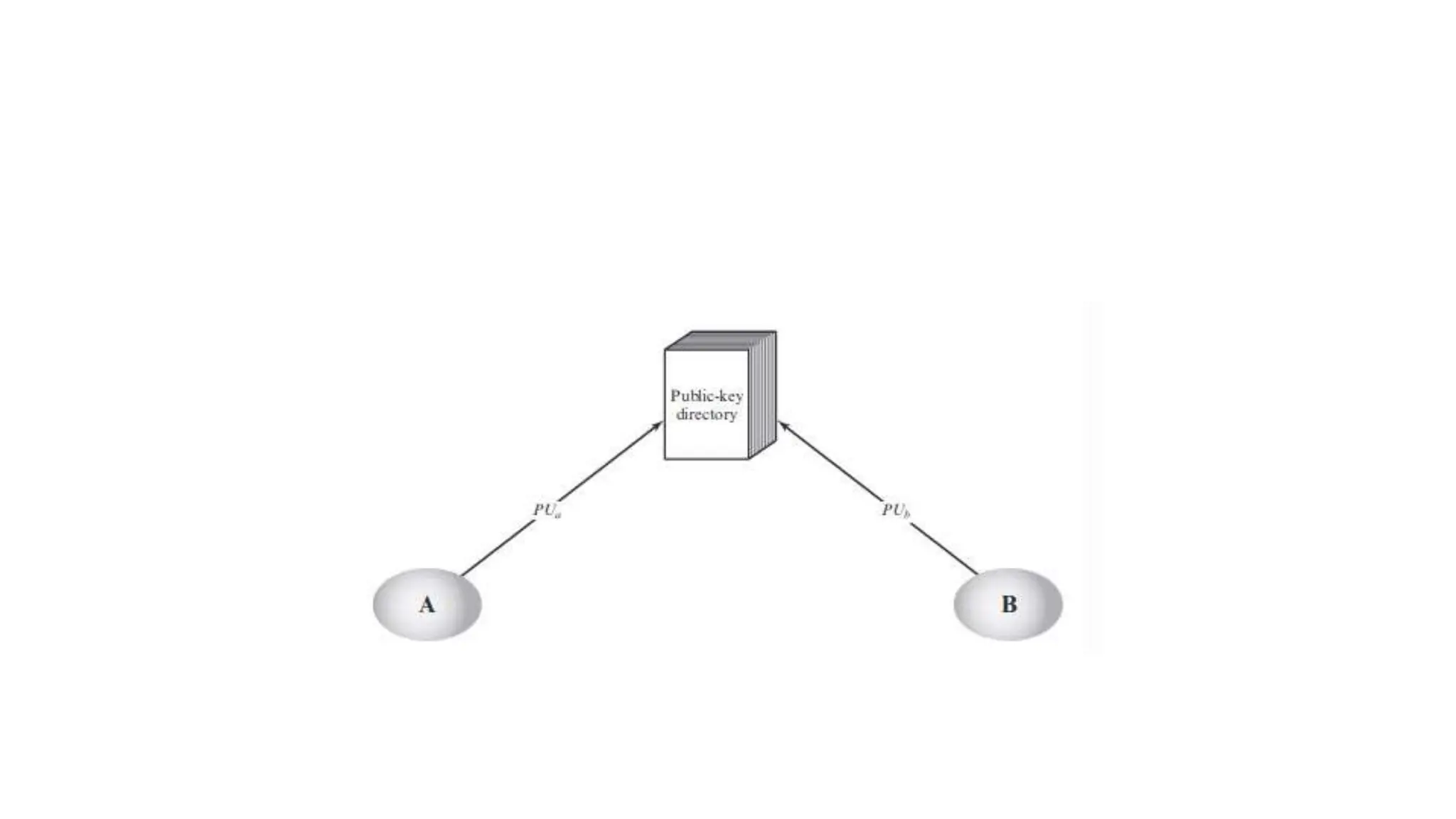
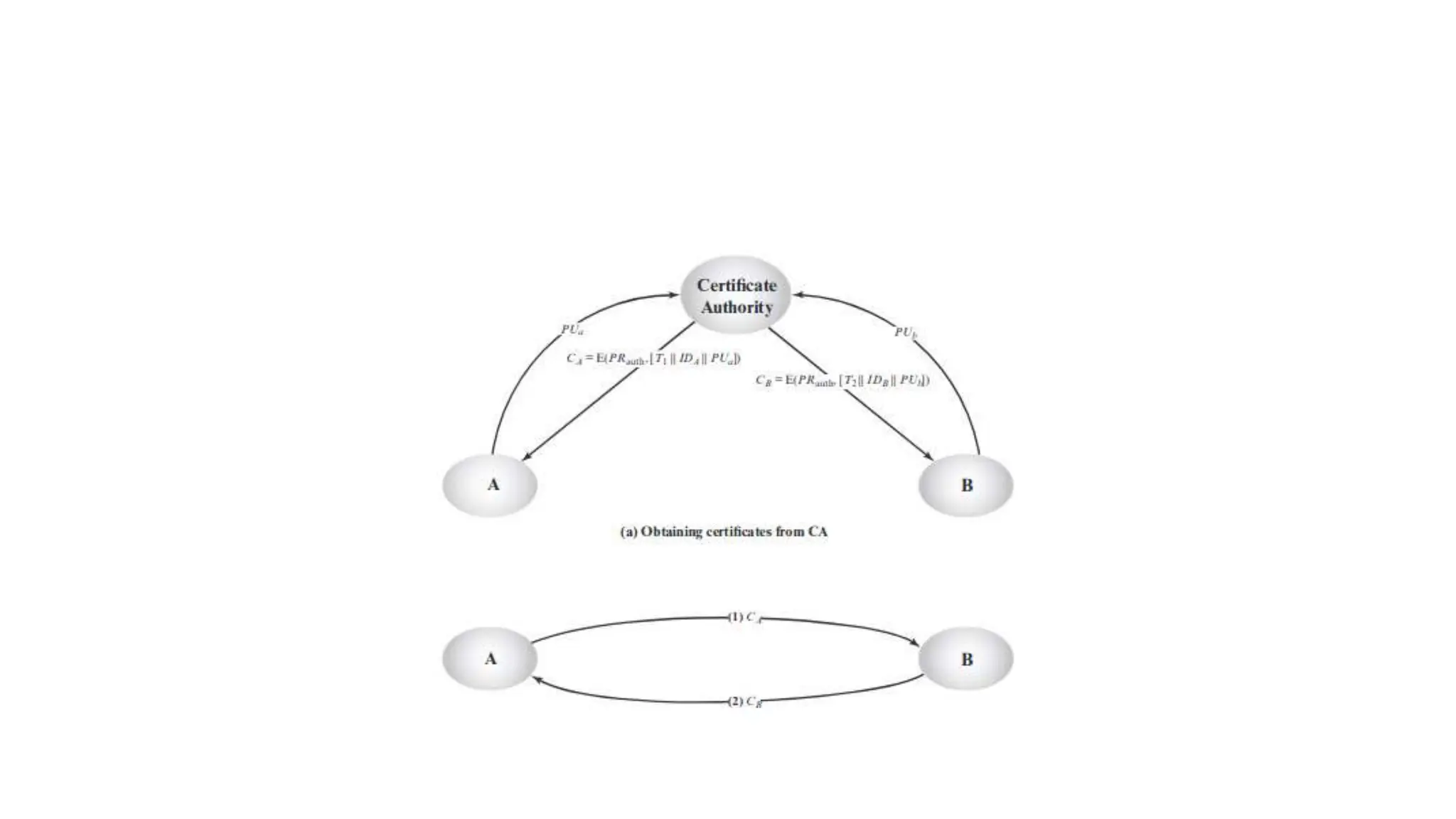
The document discusses the principles of public key cryptography including public and private keys, encryption, decryption, digital signatures, key exchange, security, trust, and revocation. It then provides details on the RSA algorithm including key generation, encryption, decryption, and security. It also discusses symmetric key distribution and key management principles like key generation, storage, distribution, rotation, expiration, revocation, and destruction. Finally, it discusses different techniques for distributing public keys such as public announcement, public directories, and using a public key authority.