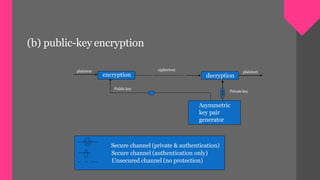
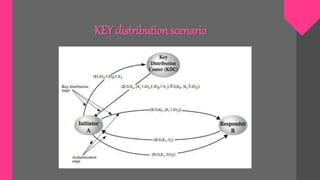
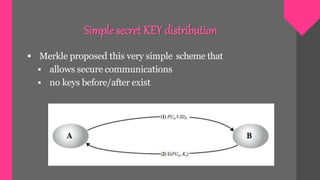
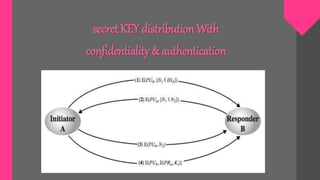
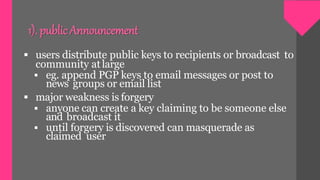
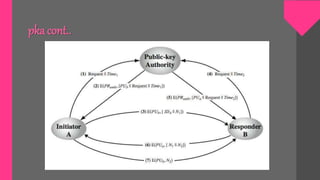
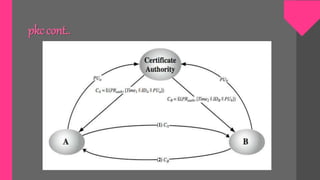
Key management involves techniques for establishing and maintaining secure cryptographic key relationships between parties. It includes procedures for key generation, distribution, installation, storage, backup and recovery, updating, revocation and destruction. The objective is to maintain keys in a way that counters threats like secret key compromise or unauthorized key use, while conforming to a security policy. Symmetric key encryption and public key techniques can be used. Key distribution methods include physical delivery, use of a third party, encryption with a previous key, or relaying via a secure third party communication channel. A key management lifecycle outlines registration, initialization, generation, installation, registration, normal use, backup, update, archival, de-registration and destruction, recovery and rev