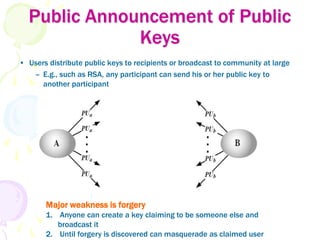
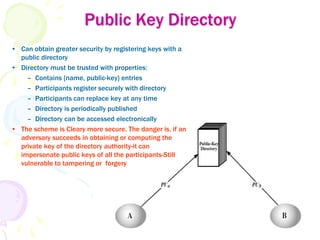
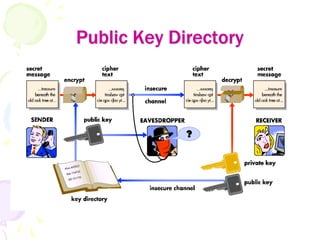
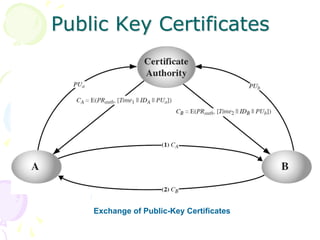
1) Key management involves the distribution and use of public keys through public announcement, public directories, public key authorities, and public key certificates.
2) Public key certificates bind a user's identity to their public key and can be verified by anyone, providing a secure mechanism for distributing public keys without direct contact.
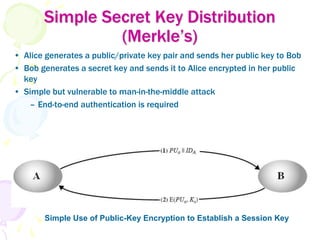
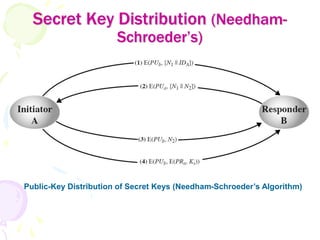
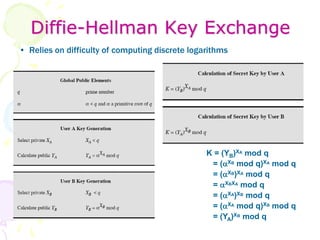
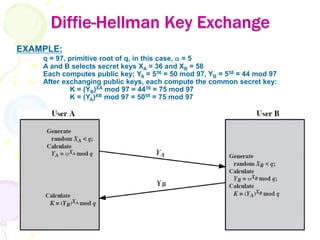
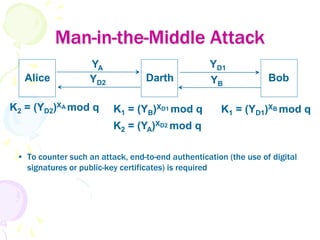
3) Secret keys can be distributed securely using public key encryption by having one party encrypt a secret key with the other's public key, or through protocols like Diffie-Hellman key exchange which allow two parties to jointly derive a shared secret key.