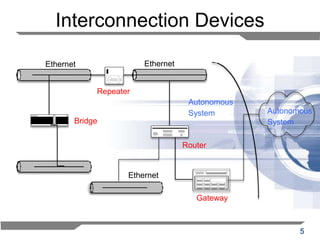
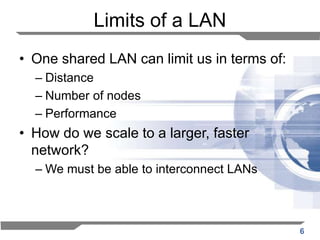
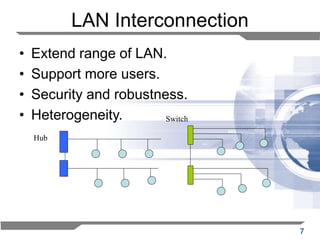
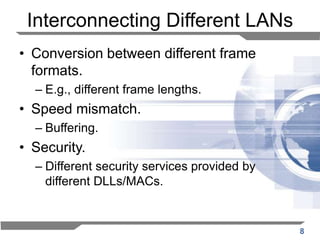
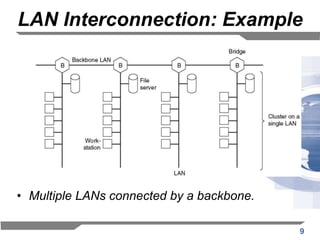
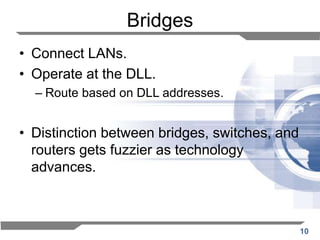
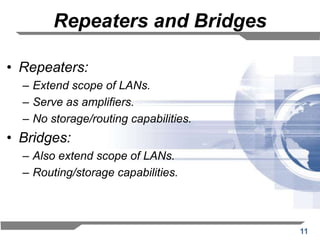
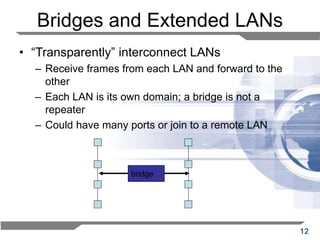
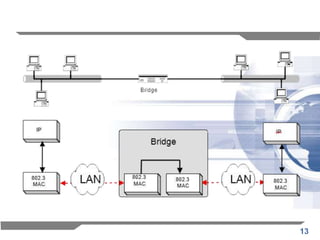
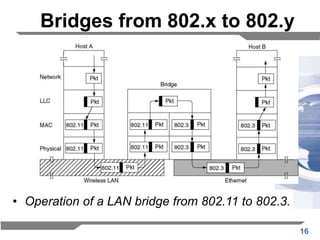
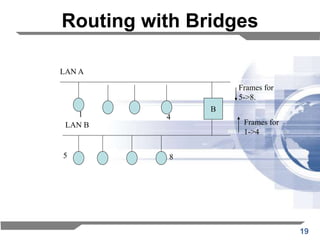
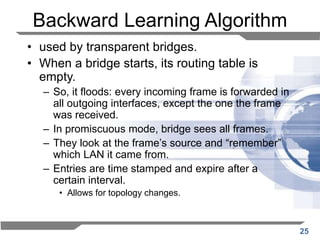
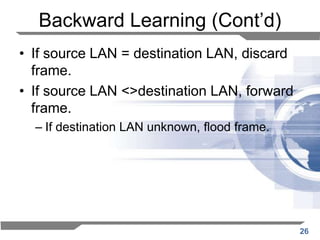
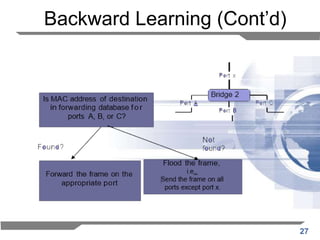
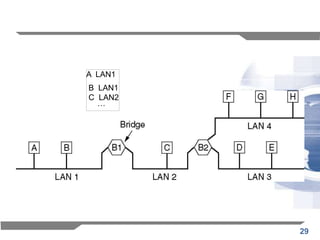
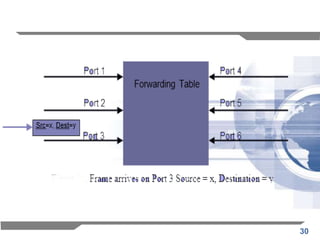
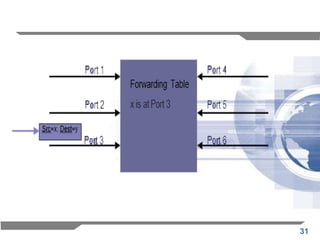
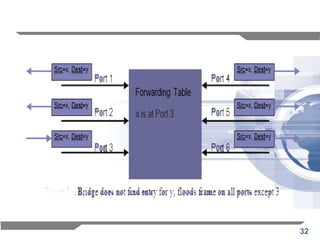
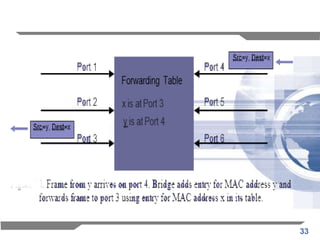
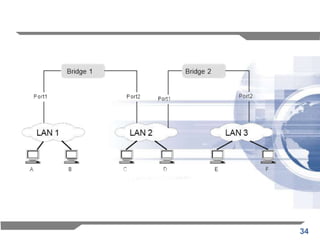
The document discusses the backward learning algorithm for creating bridges in network architectures, emphasizing the role of the data link layer and interconnection devices. It explains how bridges operate at the data link layer, managing traffic between LANs while learning the addresses from incoming packets to optimize forwarding. The backward learning algorithm enhances performance by updating routing tables based on source addresses and facilitating the connection of multiple LANs while adapting to network changes.