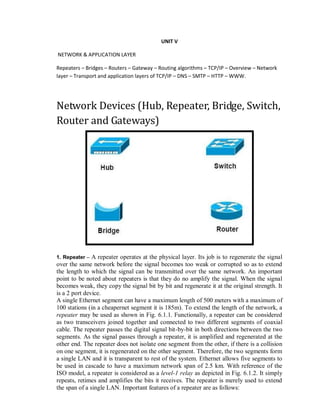
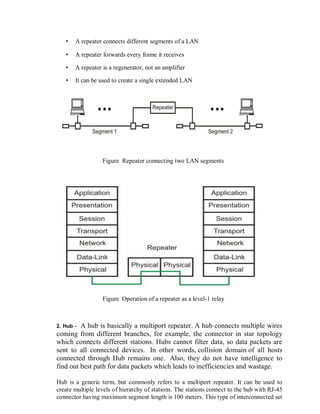
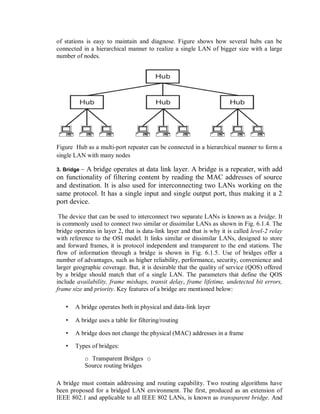
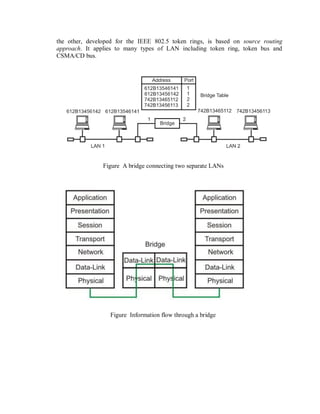
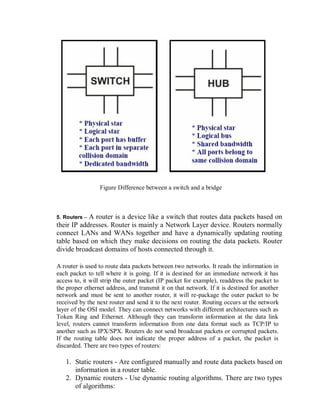
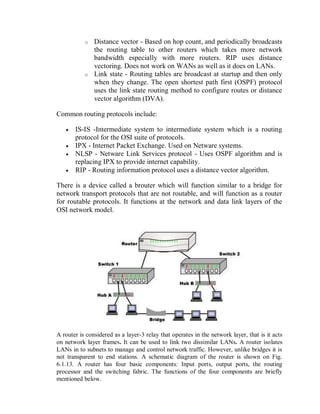
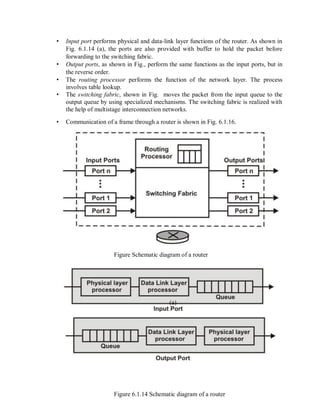
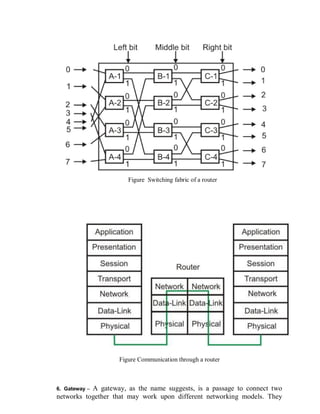
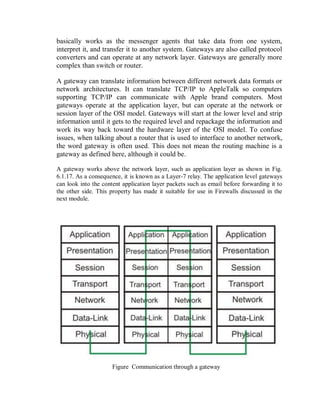
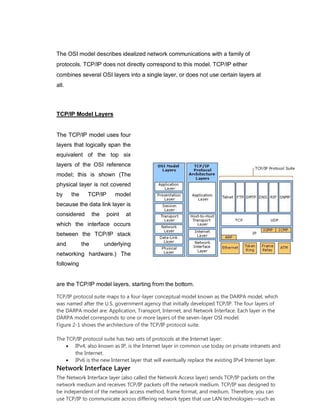
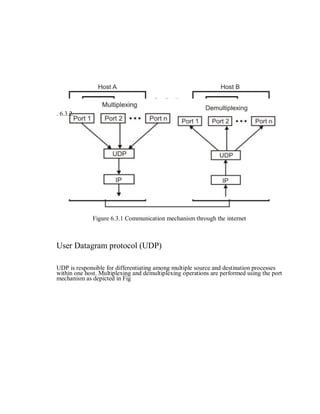
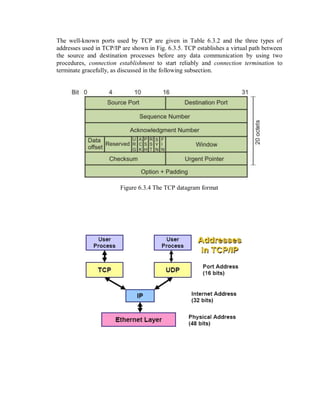
This document provides an overview of network devices and protocols including repeaters, bridges, routers, gateways, TCP/IP, and applications like DNS, SMTP, HTTP. It describes the functions of repeaters, hubs, bridges, switches, routers, and gateways. Repeaters extend network length while hubs connect multiple devices. Bridges and switches filter traffic between segments/ports. Routers route packets between networks and gateways translate between different protocols. It also summarizes the layers of the TCP/IP protocol suite including network interface, internet, transport, and application layers, and describes protocols like IPv4, IPv6, TCP, UDP, and applications like DNS, SMTP, HTTP.