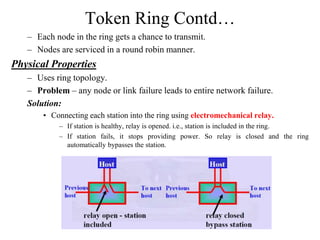
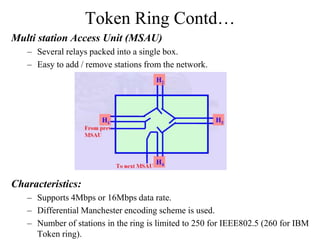
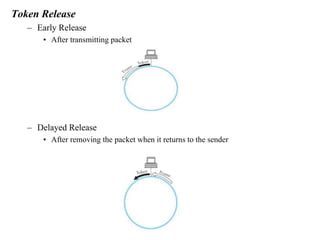
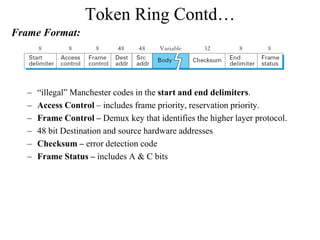
The document discusses the Token Ring network topology as defined by IEEE 802.5, where nodes are connected in a circular configuration, transmitting data in a specific direction using a token for access. It outlines the physical properties, media access control, and maintenance considerations, including how the token circulates and the roles of different nodes in managing the token and detecting failures. Additionally, it specifies data transmission characteristics, error checking, and the priorities assigned to packets.