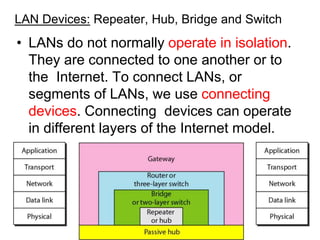
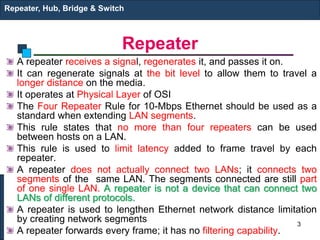
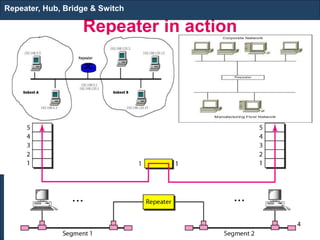
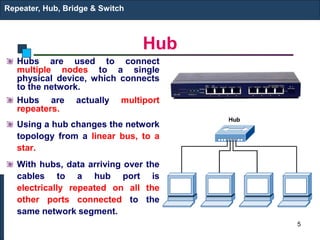
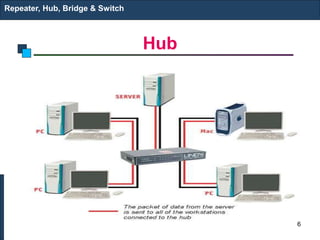
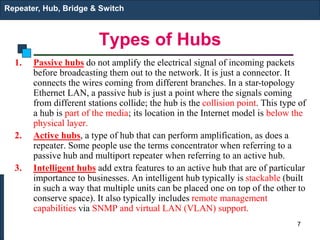
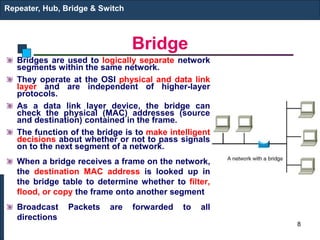
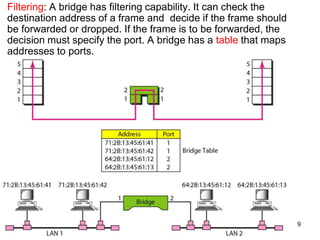
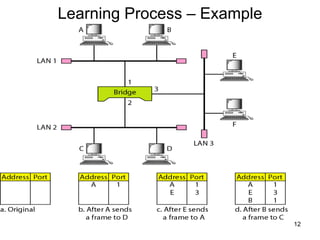
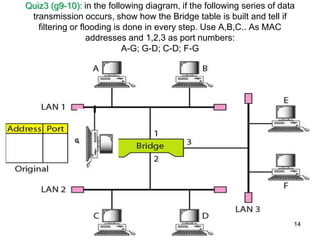
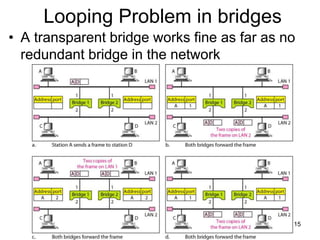
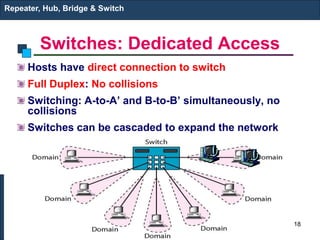
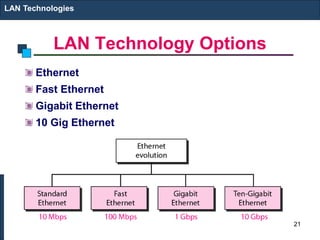
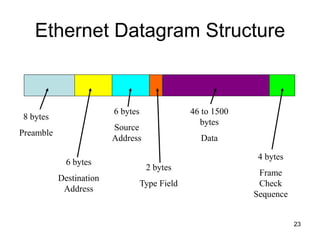
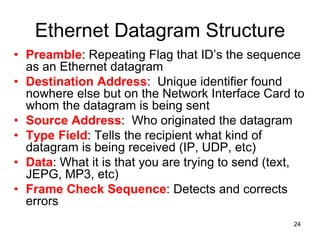
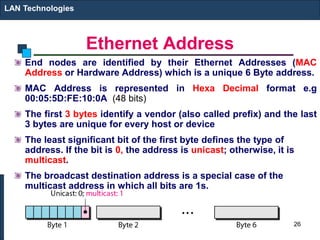
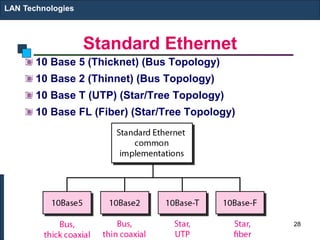
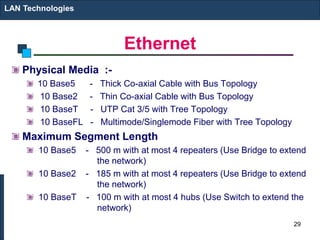
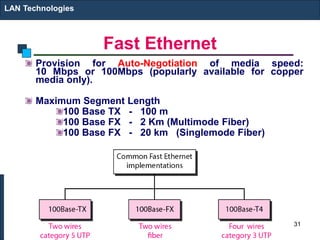
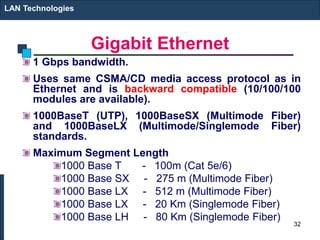
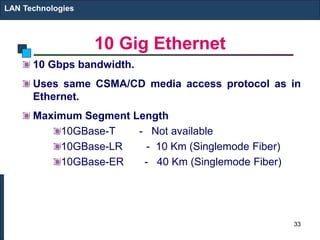
The document covers various LAN devices including repeaters, hubs, bridges, and switches, detailing their functions and roles in connecting network segments. It explains how these devices operate at different layers of the OSI model, highlighting communication practices such as filtering and flooding in bridges, as well as the advantages of switches over hubs. Additionally, it discusses Ethernet technologies and specifications, including various types of Ethernet standards and their physical media requirements.