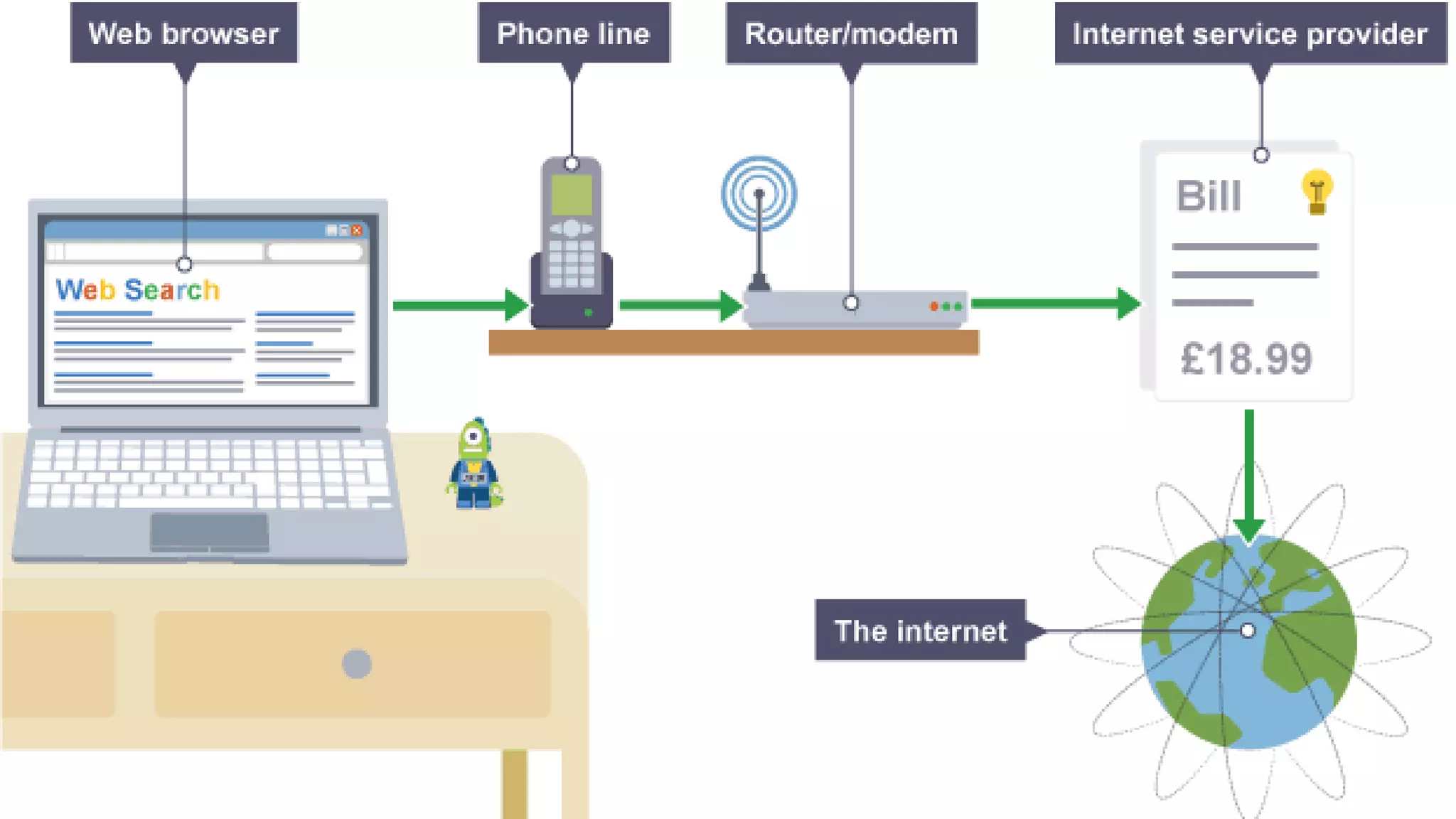
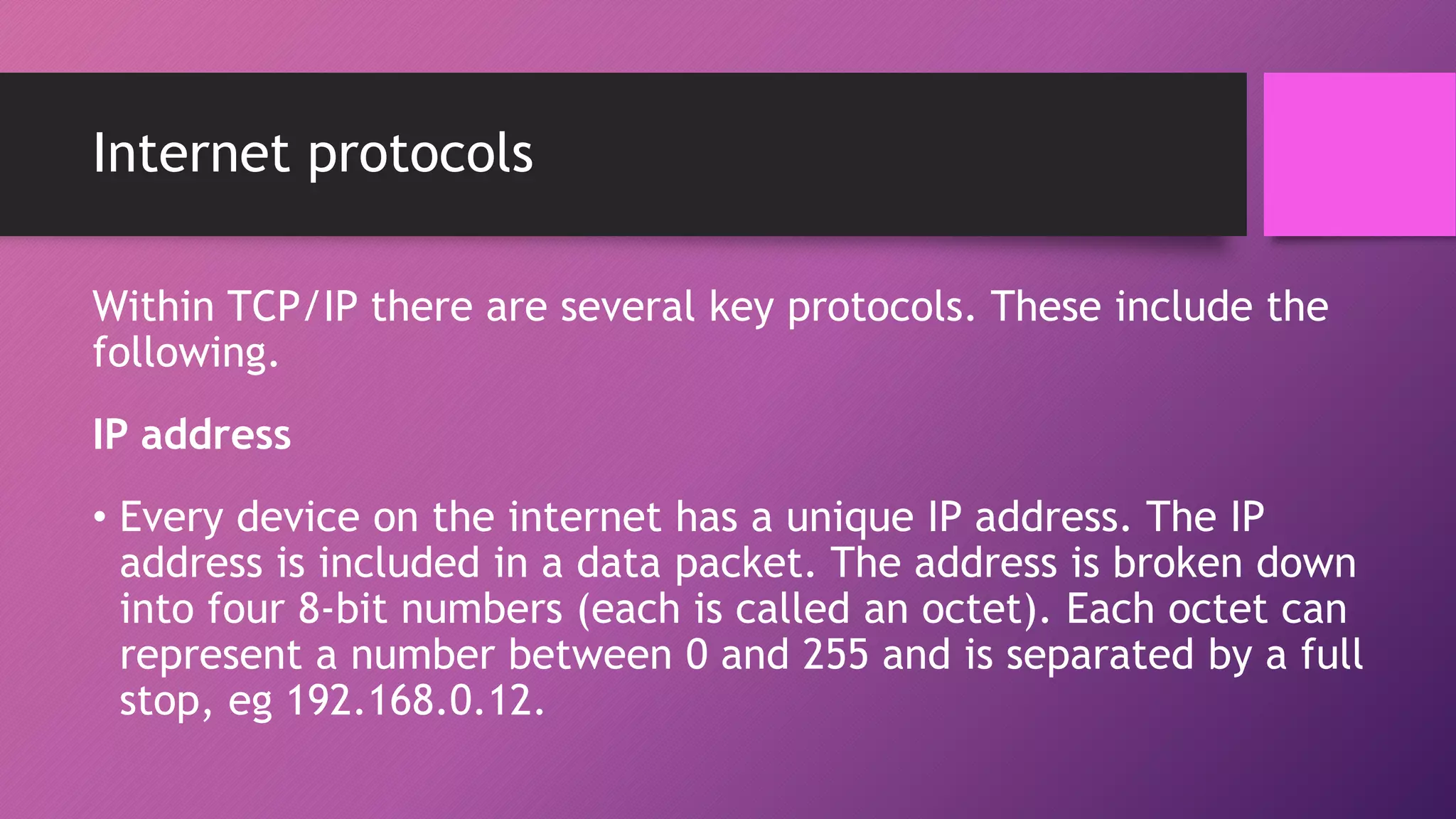
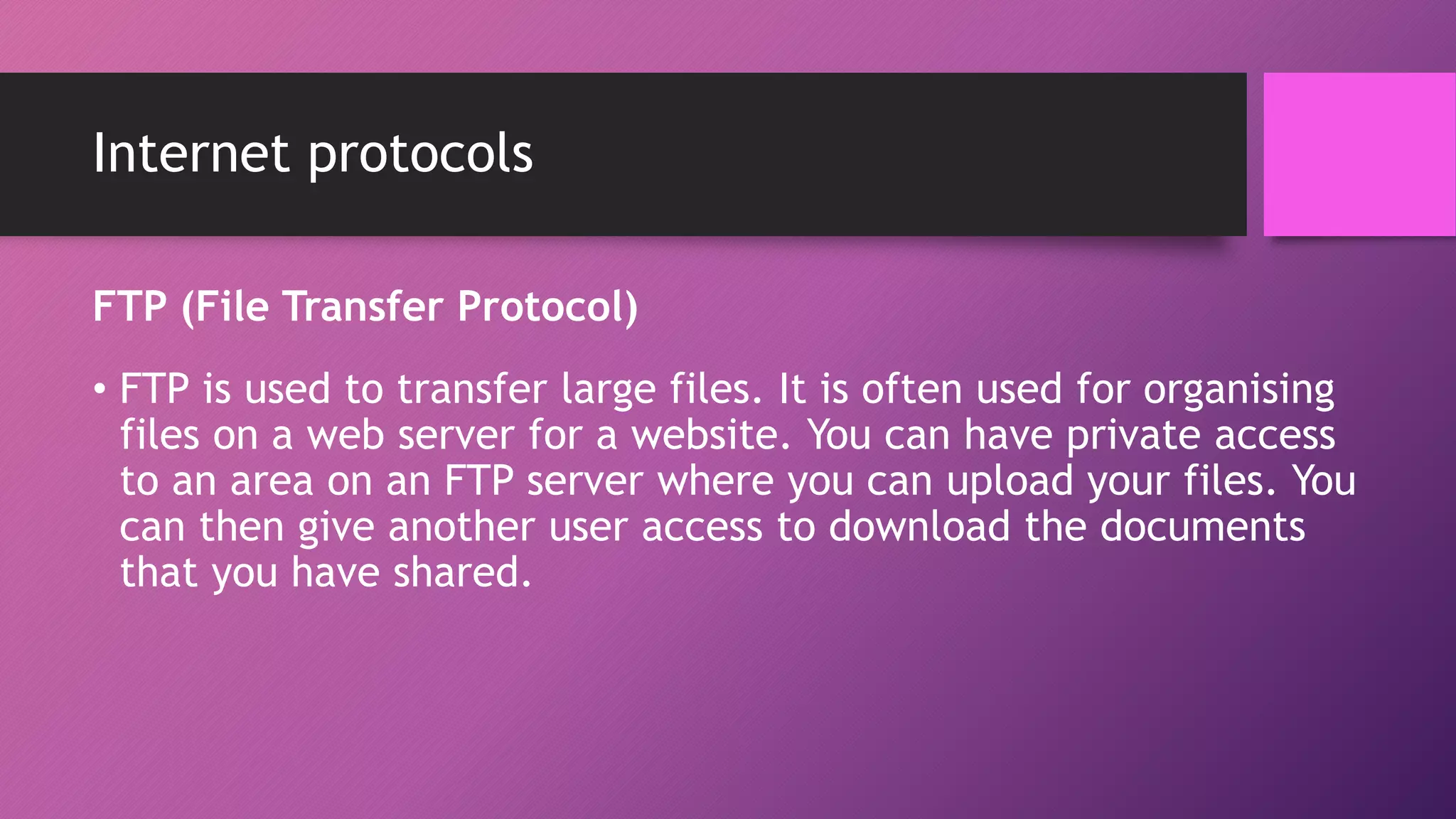
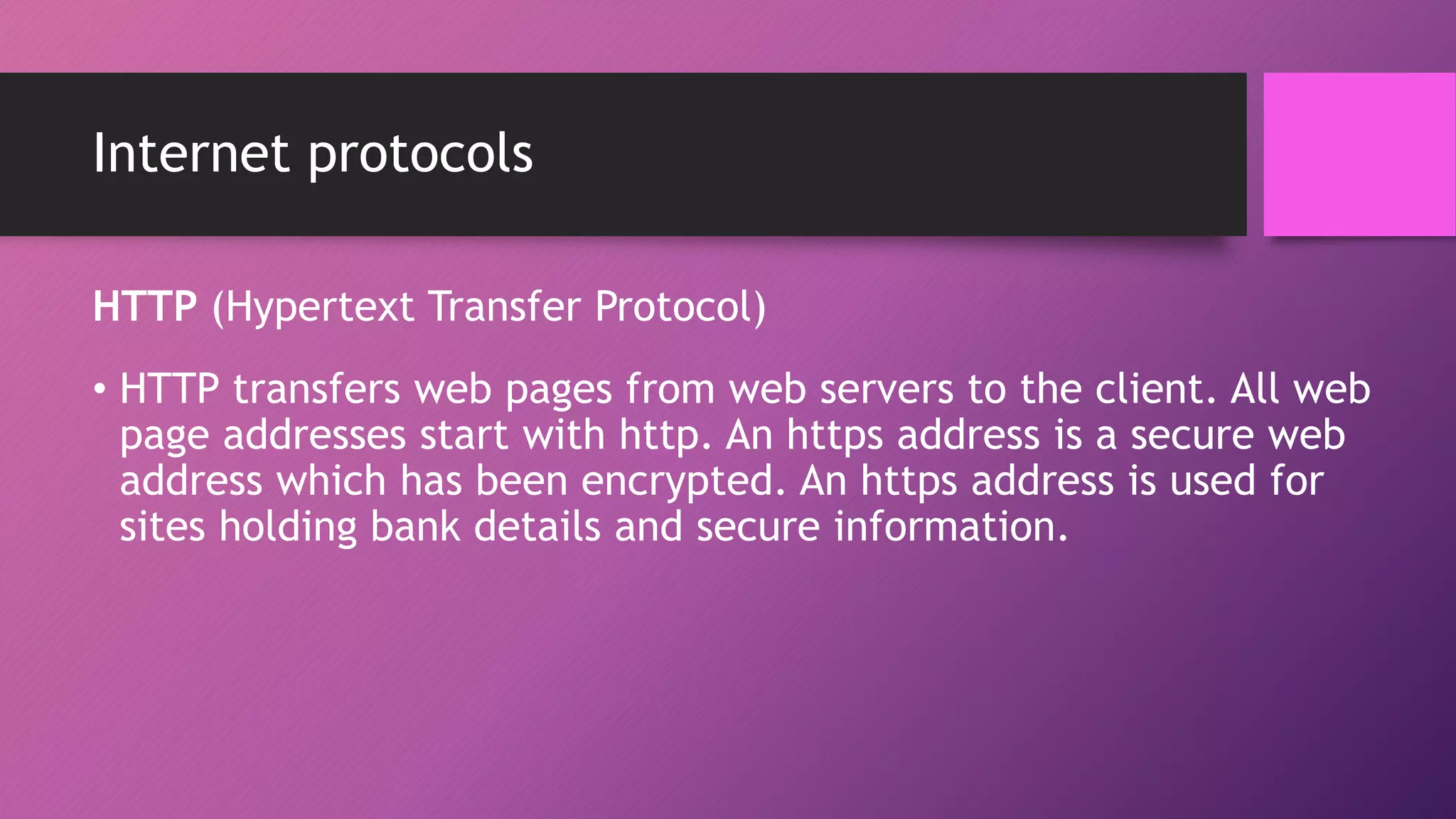
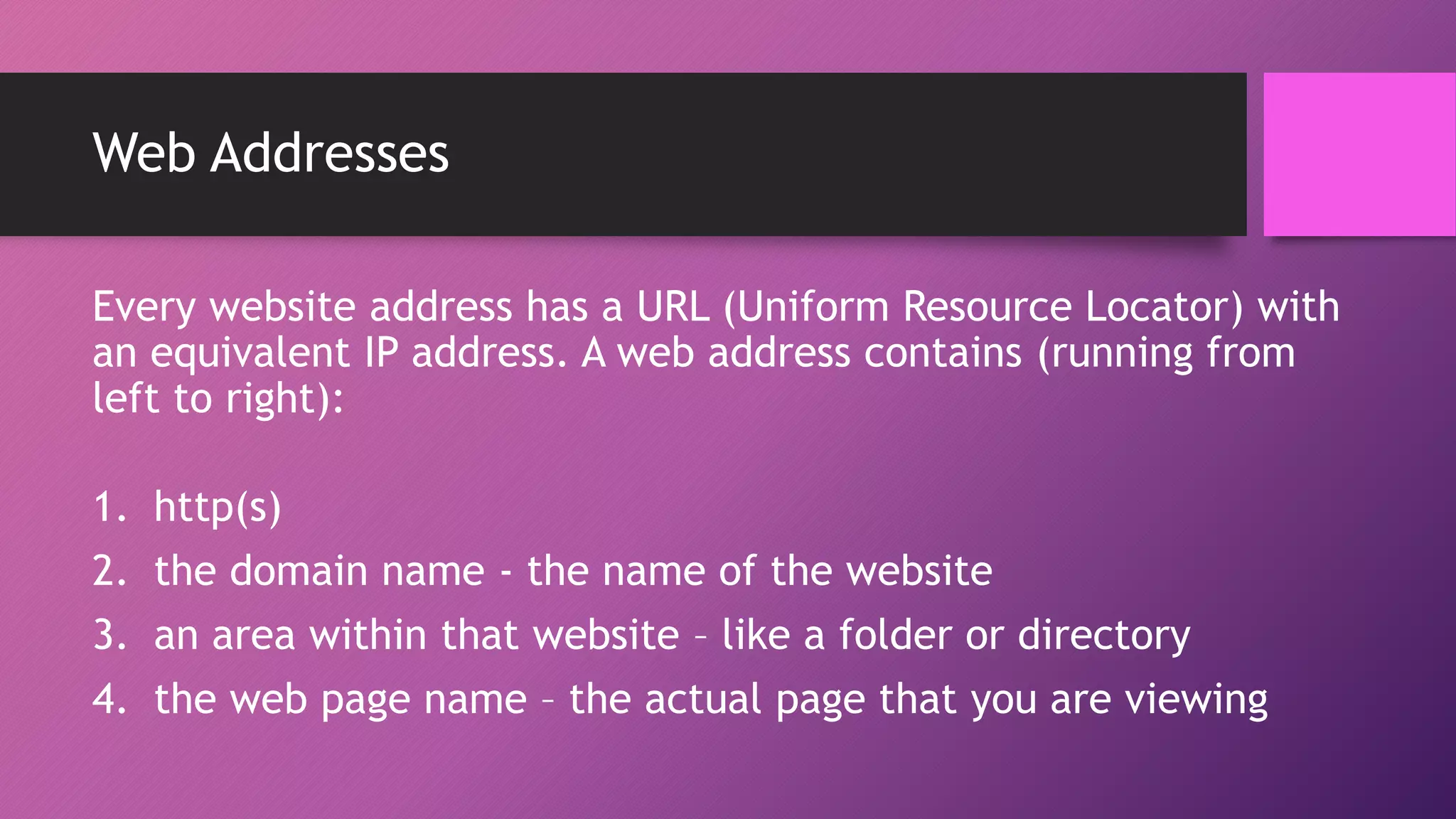
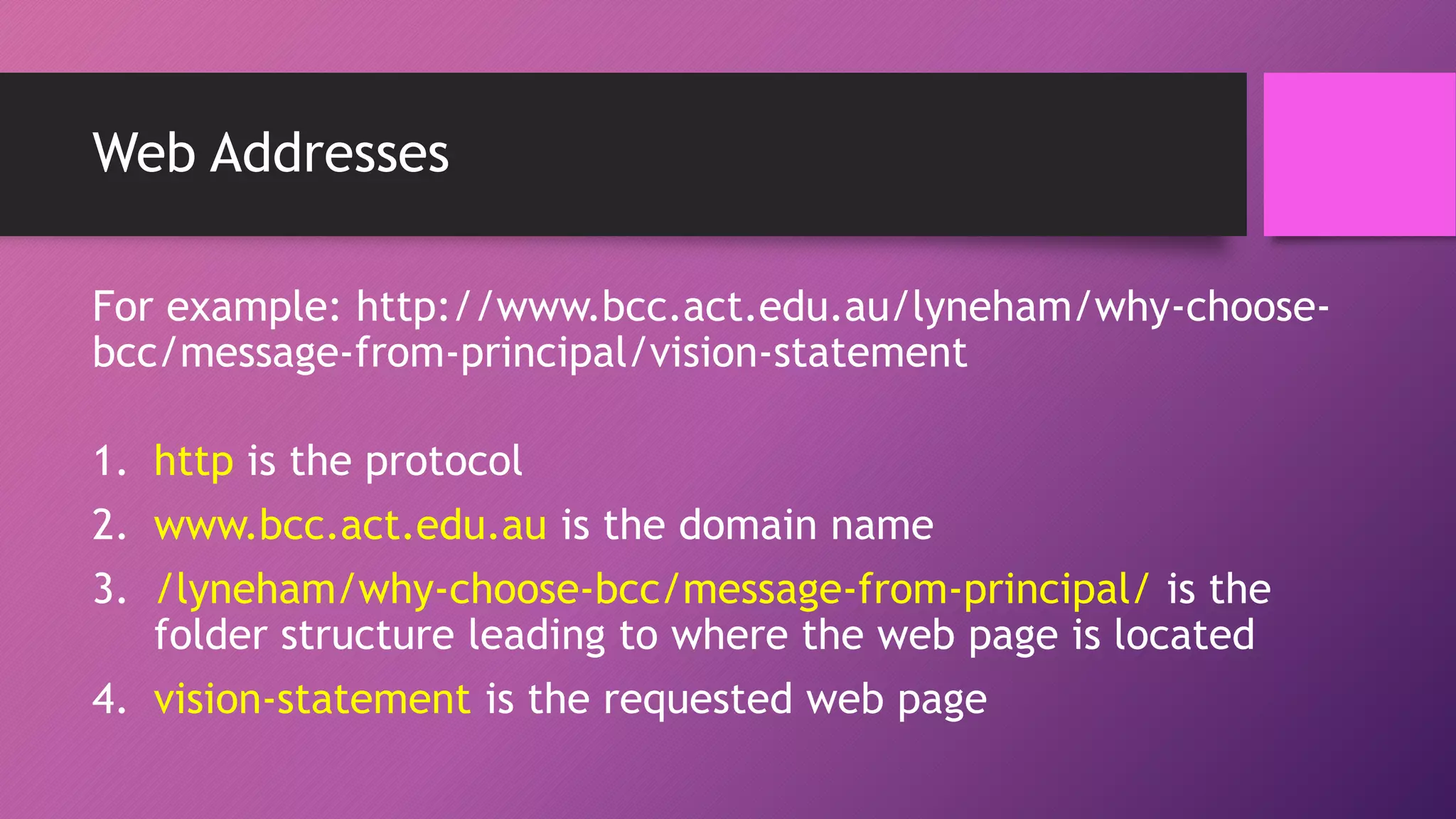
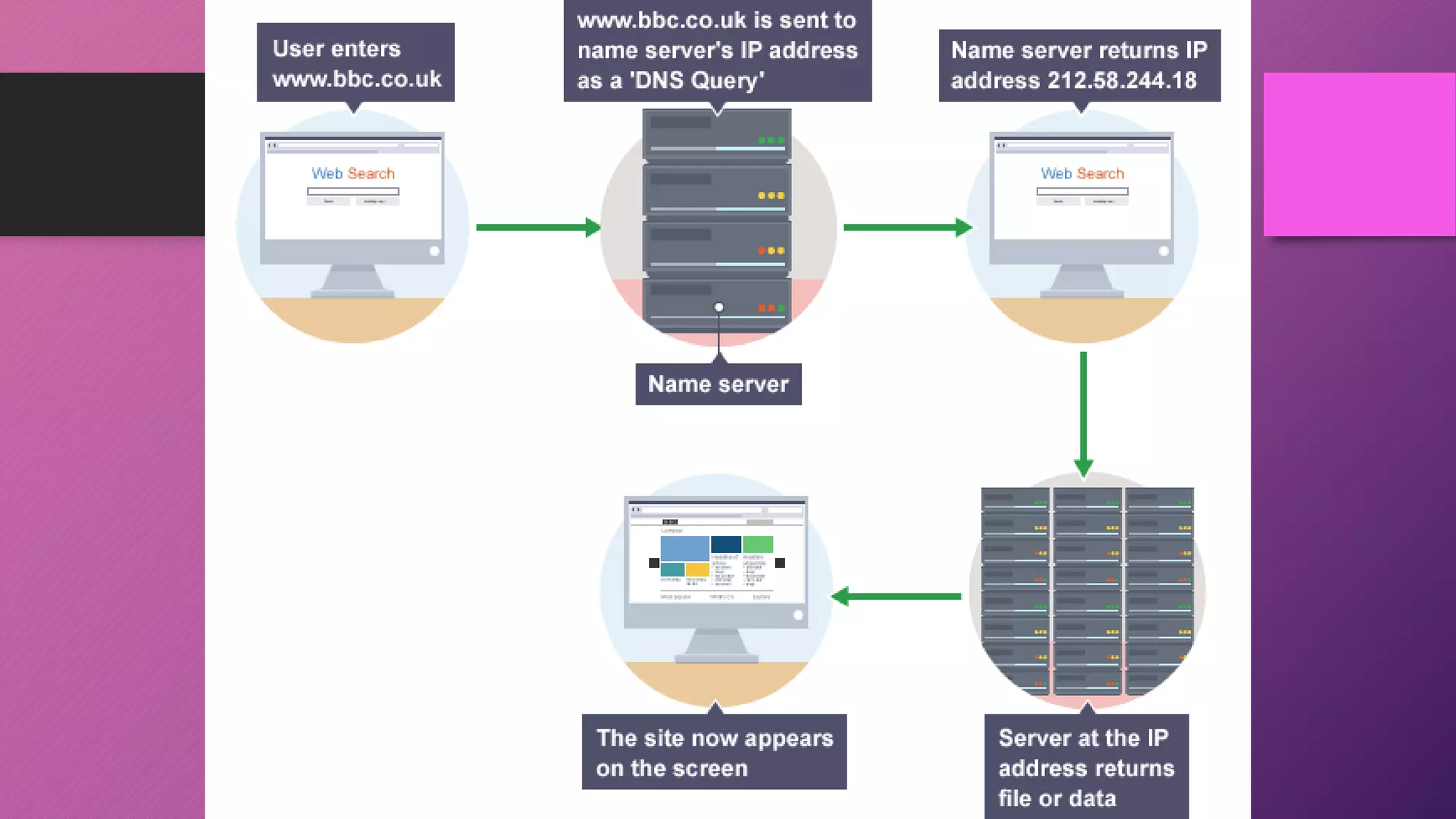
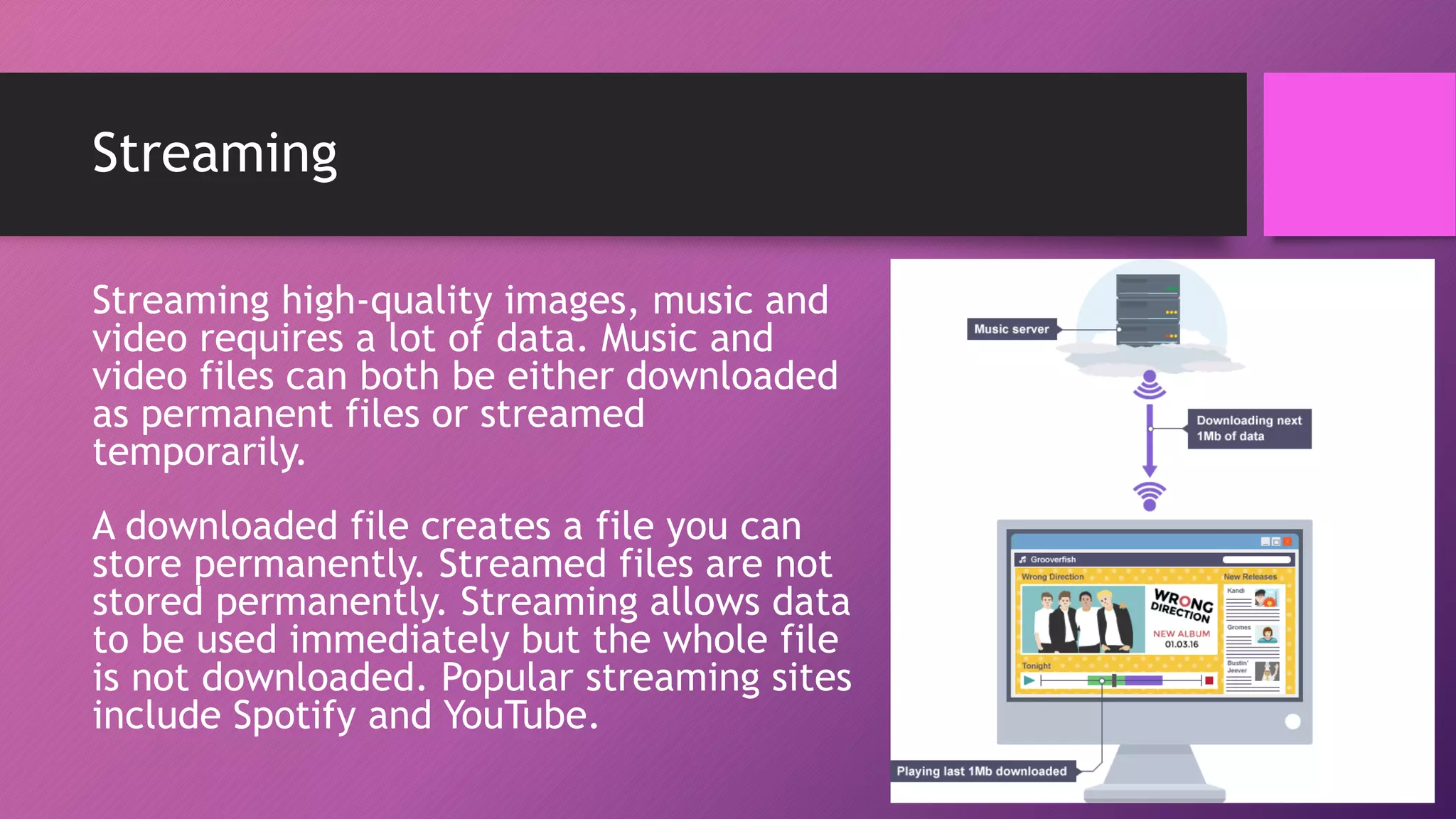
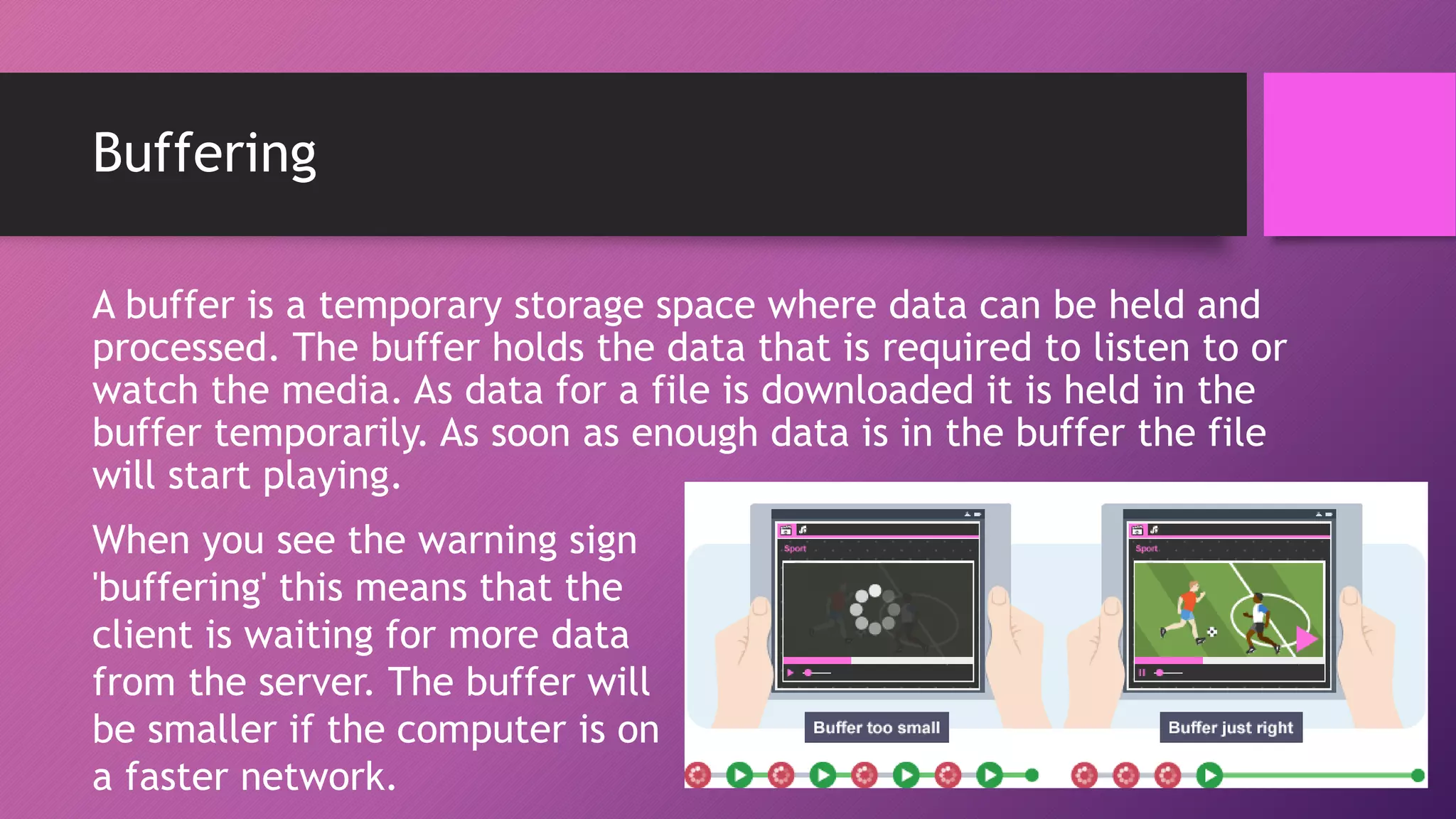
The document discusses network protocols and how the internet works. It explains that the internet is a global network of connected computers that use protocols like TCP/IP to manage how data is sent and received using packets. Key internet protocols include IP addresses, HTTP, FTP, SMTP/POP3 and VOIP. Websites have URLs with a domain name and IP address, and DNS servers match names to addresses. The document also covers streaming media, buffering, and wired/wireless connections using copper cables or fiber optics.