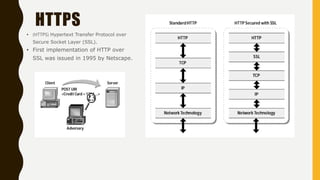
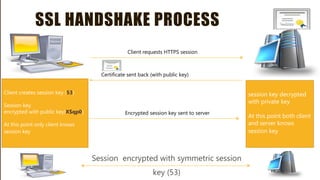
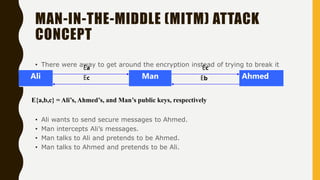
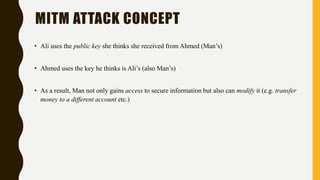
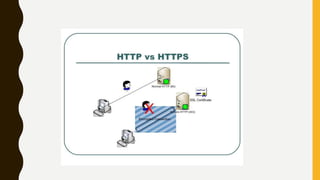
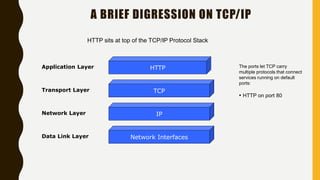
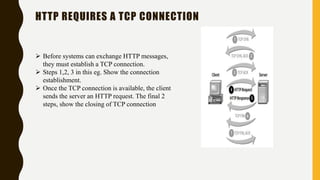
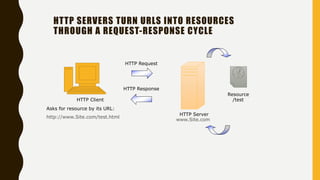
HTTP is an application-level protocol for distributed, collaborative hypermedia systems that has been used by the World Wide Web since 1990. The initial HTTP/0.9 version provided a simple protocol for raw data transfer, while HTTP/1.0 introduced MIME-like messages to include meta information and request/response modifiers. HTTP/1.0 did not sufficiently account for hierarchical proxies, caching, persistent connections or virtual hosts. HTTP sits at the top of the TCP/IP stack and uses ports to carry protocols between services, with HTTP typically using port 80. An HTTP message is delivered over a TCP/IP connection by chopping the message into chunks small enough to fit in TCP segments, which are then sent inside IP datagrams



![• URL (Uniform Resource Locators )
– Provides single short string to identify network-accessible resource
– <scheme>://<host>[:<port>]/<path>[?<query>]
– http://www.w3.org/Icons/w3c_home.gif
• URI (Uniform Resource Identifier)
– Identifies a resource either by location or name.
– The selection of the representation can be determined by the web server through
HTTP content negotiation.
– A superset of URLs
– http://www.w3.org/Icons/w3c_home.
– http request line contains a non-URL URI
URLS AND URIS](https://image.slidesharecdn.com/httpppt-180419164616/85/Http-protocol-6-320.jpg)

![RESPONSE
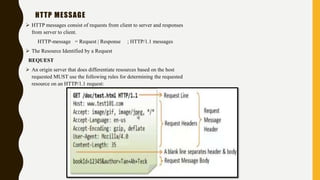
After receiving and interpreting a request message, a
server responds with an HTTP response message.
Response = Status-Line
*( general-header |
response-header |
entity-header )
CRLF [ message-body ]](https://image.slidesharecdn.com/httpppt-180419164616/85/Http-protocol-12-320.jpg)