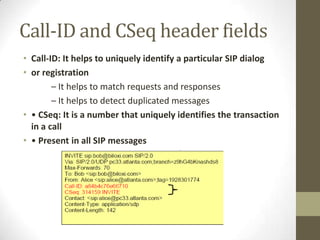
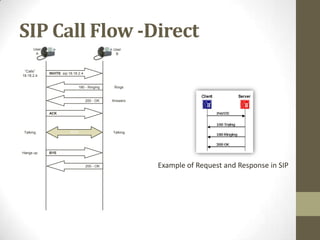
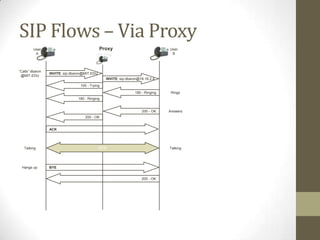
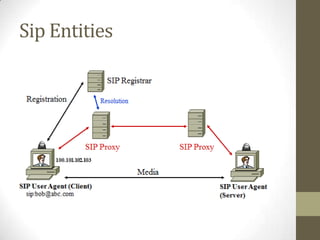
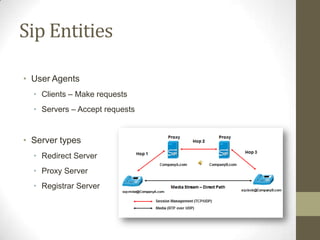
SIP is an application-layer protocol for establishing multimedia sessions over IP networks. It can be used to initiate voice, video, and instant messaging communications. SIP works by having user agents (clients and servers) exchange SIP request and response messages. These messages contain information about session setup, modification, and termination. Some key SIP components include user agents, proxy servers, registrar servers, and redirect servers. SIP messages use a request-response transaction model and contain start lines, headers, and optional message bodies. Common request methods are INVITE, ACK, BYE, and REGISTER. Typical response codes include 100-199 (informational), 200-299 (success), 300-399 (redirection), 400-499






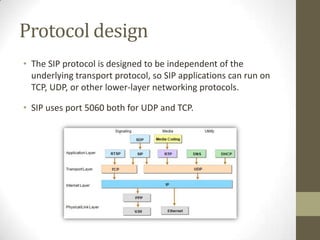

![Addressing
sip:user@host[parameters][headers]
• SIP-addresses are like URLs, with prefix sip:
which gives schema
– sip:joe.smith@hut.fi
– sip:joe.smith@hut.fi?subject=Protocol
– sip:sales@hotel.xy;geo.position:=48.54_-123.84_120
• Address must include host, other parameters are optional
(username, port, etc…)](https://image.slidesharecdn.com/presentation-sessioninitiationprotocol-copy-131005003534-phpapp01/85/session-initiation-protocol-SIP-13-320.jpg)