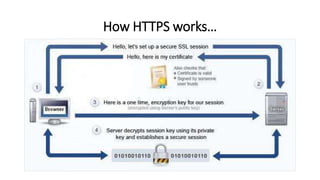
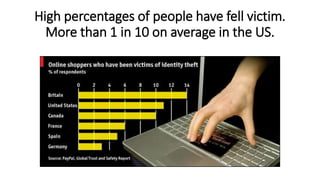
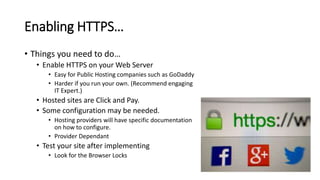
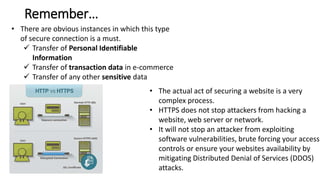
The document discusses HTTPS, explaining its importance for secure communication between web servers and browsers, as well as its limitations. It emphasizes the necessity of SSL certificates for protecting sensitive user information and outlines best practices for implementing HTTPS. Furthermore, it highlights the ongoing risks of data theft and the importance of user education in maintaining online security.




![Founded
• Netscape Communications created HTTPS in 1994 for its Netscape
Navigator web browser.[40] Originally, HTTPS was used with the SSL
protocol. As SSL evolved into Transport Layer Security (TLS), the
current version of HTTPS was formally specified by RFC 2818 in May
2000.](https://image.slidesharecdn.com/httpspresentation927-160520201646/85/HTTPS-6-320.jpg)