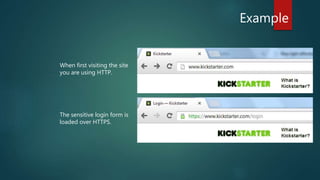
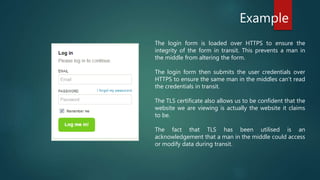
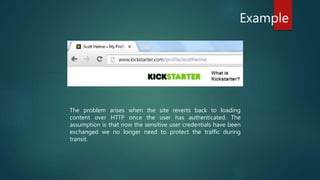
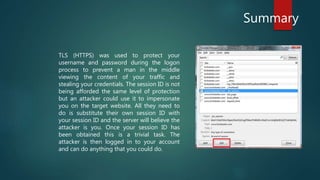
The document discusses the importance of Transport Layer Security (TLS) in protecting web communications from attacks such as session hijacking, where an attacker can impersonate a user by stealing their session ID. It emphasizes that TLS should be enforced across the entire site to ensure security, as reverting to HTTP after authentication exposes vulnerabilities. The conclusion stresses that while a stolen session ID doesn't reveal user credentials, it still allows attackers to access accounts, highlighting the need for constant HTTPS usage.