The document discusses cybersecurity issues including:
- The original open design of the internet lacked security concerns
- Cybersecurity issues can be classified by the type of action, perpetrator, and targets
- National and international initiatives have been established to address cybersecurity including organizations like DHS, ITU, UN, and policies on standards, legal measures, and capacity building
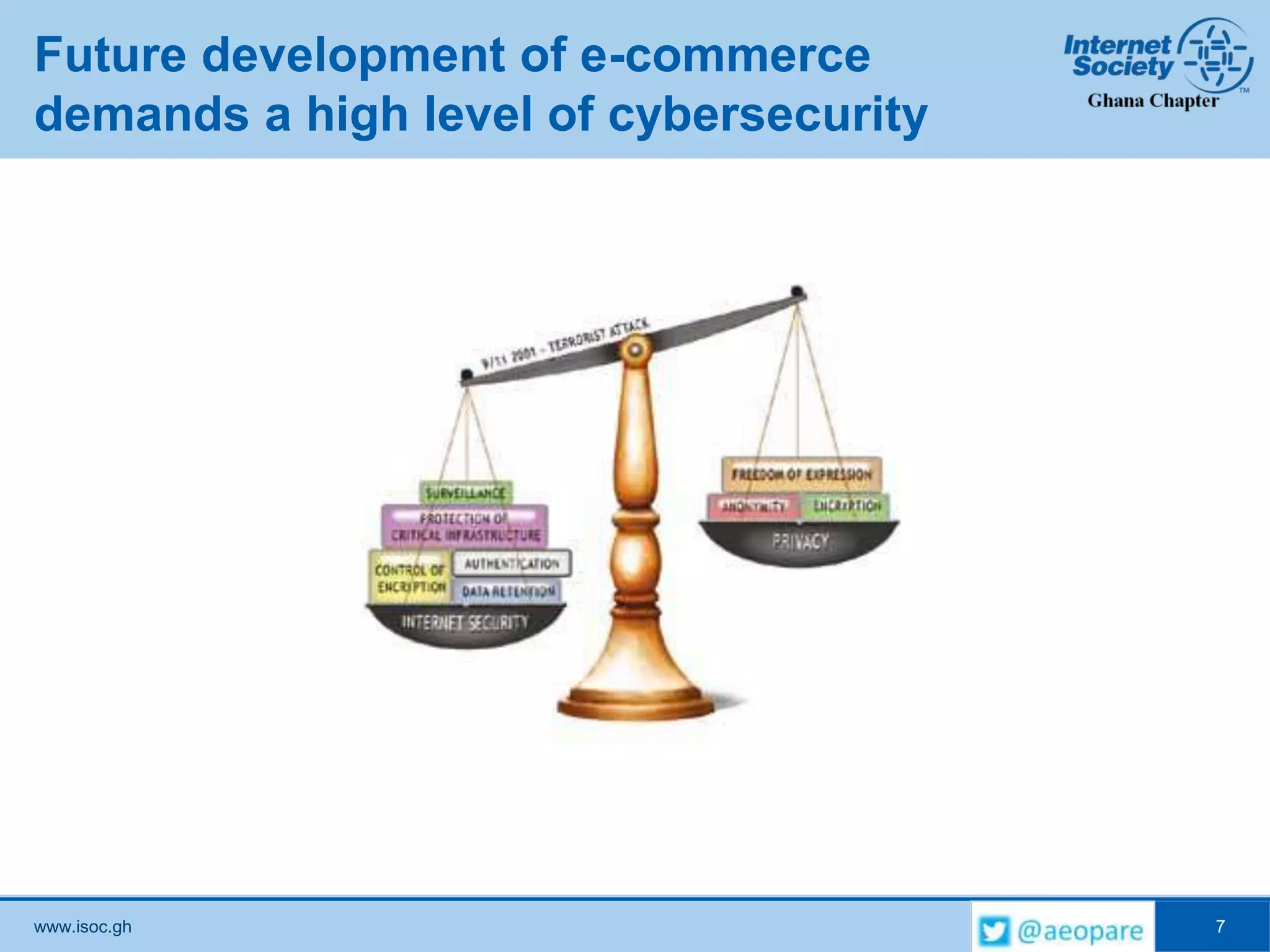
- Future e-commerce requires high cybersecurity but additional measures may impact privacy, such as regulations on encryption software.