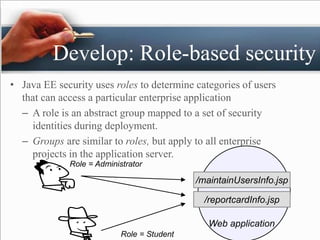
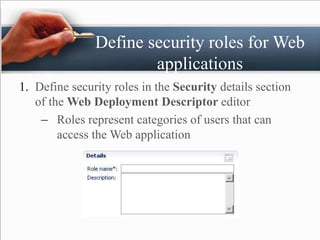
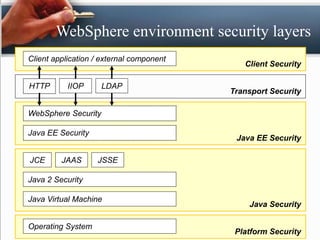
The presentation by Padam Banthia on web security discusses the critical need for protecting information online as various sectors increasingly rely on digital systems. It outlines several key web security issues such as malicious websites, spam, phishing, DDoS attacks, and the importance of role-based security in web applications. Additionally, it highlights various authentication methods and emphasizes integrating security into applications during development rather than as an afterthought.

















![Protect
• [SWAT] Checklist
• Firewalls
• IDS and IDPs
• Audits
• Penetration Tests
• Code Reviews with Static
• Analysis Tools](https://image.slidesharecdn.com/web-security-170321174417/85/Web-security-21-320.jpg)


