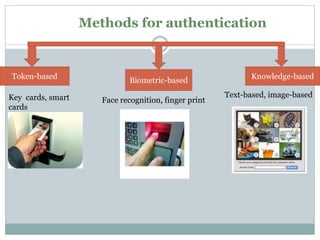
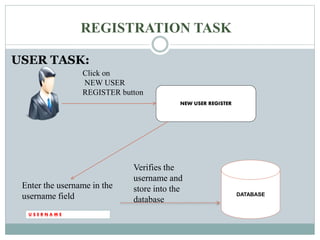
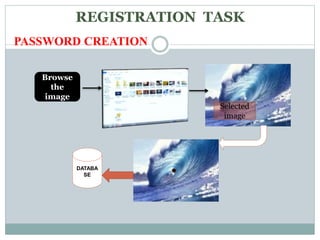
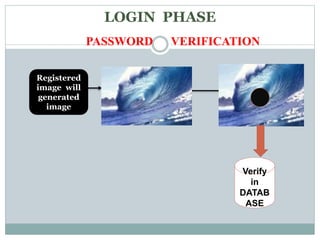
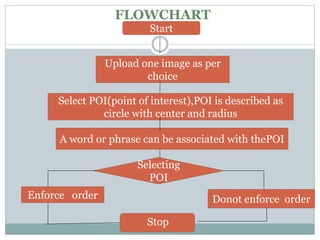
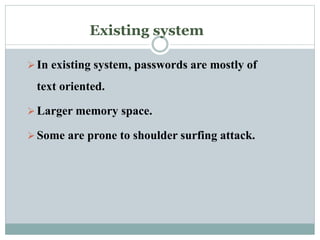
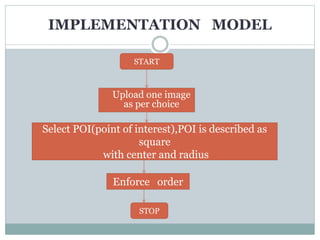
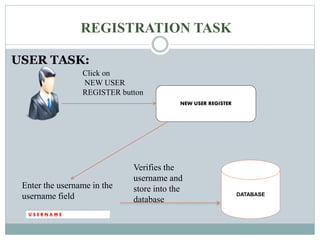
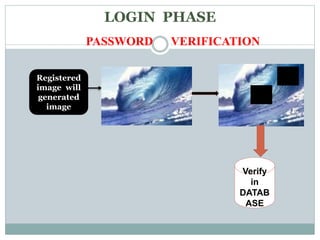
This document discusses graphical passwords as an alternative to text-based passwords. It outlines the drawbacks of text-based passwords, such as being difficult to remember and vulnerable to brute force and dictionary attacks. The document then proposes a graphical password system that uses images and points of interest on images instead of text for password authentication. This approach aims to make passwords more secure and easier for users to remember.