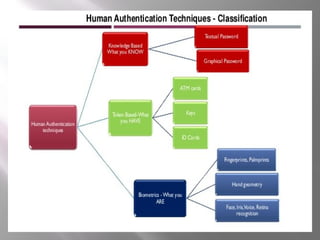
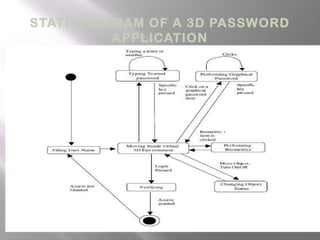
The document discusses 3-D passwords, which combine multiple authentication factors like passwords, biometrics, and tokens into a single virtual 3D environment. A 3-D password requires a user to navigate a virtual world and interact with various objects in a specific sequence. This makes 3-D passwords very difficult to guess compared to standard text passwords. The document outlines how a 3-D password works, provides examples of virtual objects, and discusses potential applications and advantages like improved security and ease of memory, while also noting challenges like vulnerability to recording attacks.