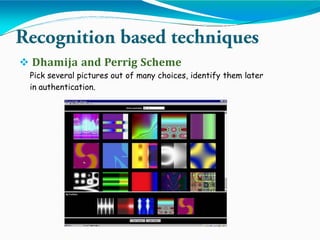
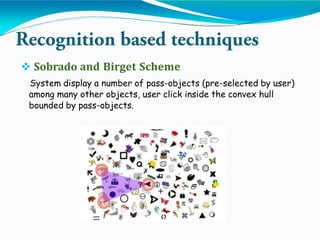
This document summarizes a project on graphical password authentication. The project was completed by three group members and guided by Prof. B. Jadhav. It provides an introduction to text passwords and their drawbacks. It then surveys existing recognition-based graphical password techniques, including schemes by Blonder, Dhamija and Perrig, and Passface. The document discusses the advantages of graphical passwords in being more secure and hard to crack via dictionary attacks, though they are slower and require more storage than text passwords. It also notes shoulder surfing as a disadvantage graphical passwords need to address to become more widely used.