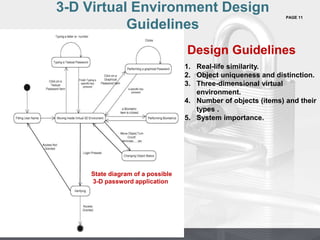
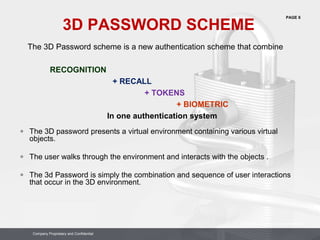
This document proposes a 3D password authentication scheme that combines recognition, recall, tokens, and biometrics. The scheme uses a 3D virtual environment containing various interactive objects. A user's 3D password is the combination and sequence of interactions they perform with objects in the environment, such as opening a door, typing on a keyboard, drawing on a whiteboard. The scheme aims to provide stronger authentication through multi-factor authentication in a 3D space while being easier for users to remember. Some advantages include flexibility, strength from many possible passwords, and ease of memory through forming a story. Disadvantages include difficulty for blind users and needing sophisticated technology.




![PAGE 9
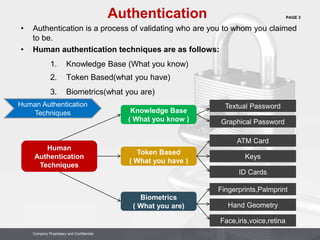
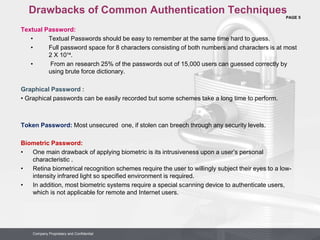
Company Proprietary and Confidential
Company Proprietary and Confidential
For Example :
Let us assume the user enters a virtual office then performs the following action:
(10,24,91) Action=Open office door
(10,24,91) Action=Close office door
(4,34,18) Action=Typing,”C”
(4,34,18) Action=Typing,”O”
(4,34,18)Action=Typing,”N”
(10,24,80)Action=Pick up the pen
(1,18,80)Action=Draw point=(330,130)
3D Password selection and Inputs
( Formal View )
Let us consider a 3-D virtual environment space of size G x G x G.
The 3-D environment space is represented by the coordinates (x, y, z) Є [1, . . . ,
G] x [1, . . . , G] x [1, . . . , G].
The objects are distributed in the 3-D virtual environment with unique (x, y, z)
coordinates.
We assume that the user can navigate into the 3-D virtual environment and interact
with the objects using any input device such as a mouse, keyboard, fingerprint
scanner, iris scanner, stylus, card reader, and microphone.](https://image.slidesharecdn.com/3dpassword23mar14-140630051345-phpapp02/85/3d-password-23-mar-14-9-320.jpg)