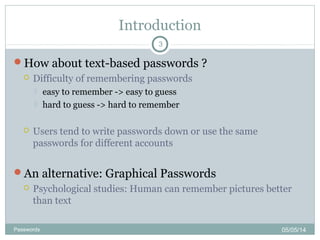
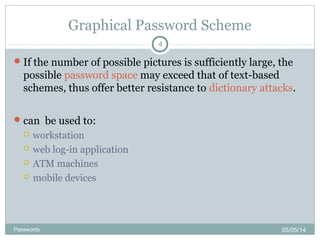
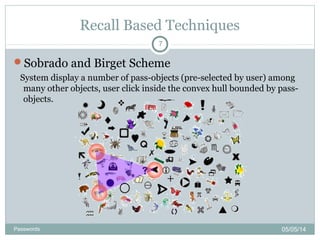
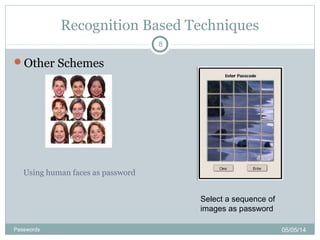
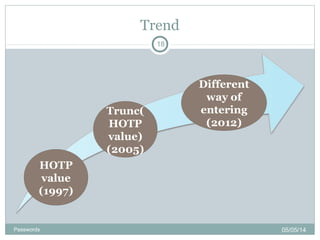
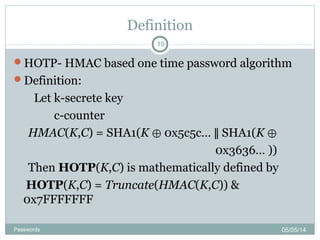
The document discusses various password authentication methods, highlighting the challenges of text-based passwords and the potential advantages of graphical passwords, which can enhance memorability and security. It outlines recognition and recall-based techniques and examines their usability and security compared to traditional text passwords. The conclusion suggests that while graphical passwords may offer better resistance to attacks, their current technological maturity is limited and they are not widely adopted.










![Contd..
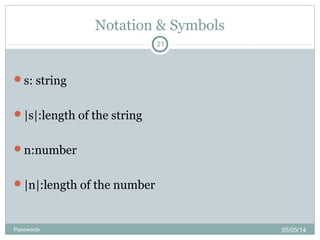
s[i]:string at ith
bit
stToNum: function that as i/p a string s returns the
number whose binary representation is s
Example:
stToNum(110)=6
05/05/14
22
Passwords](https://image.slidesharecdn.com/gpa-140505121603-phpapp02/85/Graphical-Password-authentication-using-Hmac-22-320.jpg)
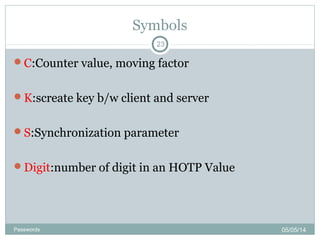
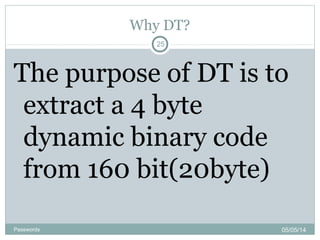
![Generation of HOTP Value
Step-1
Generate HMAC Value(HMAC-SHA-1)
Let HS=HMAC-SHA-1(k,c) [ HS=20 bytes (say)]
Step-2
Generate 4byte string(DT)
sbits=DT(HS) [returns 32-bit string]
Step-3
Compute HOTP Value
Let Snum=stToNum(sbits)
return D=Snum mod 10^Digit
05/05/14
24
Passwords](https://image.slidesharecdn.com/gpa-140505121603-phpapp02/85/Graphical-Password-authentication-using-Hmac-24-320.jpg)

![Implementation
function hmac (key, message)
{
if (length(key) > blocksize)
then key = hash(key)
end if
if (length(key) < blocksize)
then key = key [0x00 * (blocksize - length(key))∥
end if
o_key_pad = [0x5c * blocksize] key⊕
i_key_pad = [0x36 * blocksize] key⊕
return hash(o_key_pad hash(i_key_pad message))∥ ∥
End of function
05/05/14
28
Passwords](https://image.slidesharecdn.com/gpa-140505121603-phpapp02/85/Graphical-Password-authentication-using-Hmac-28-320.jpg)
