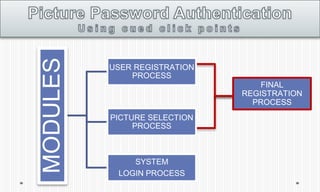
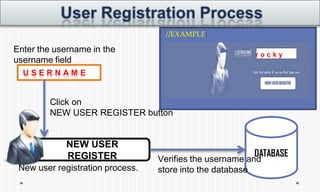
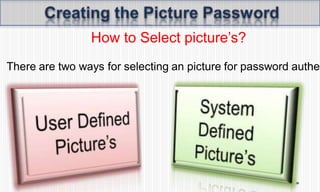
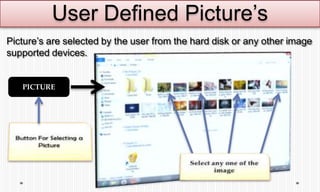
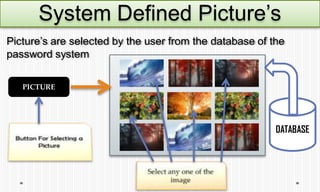
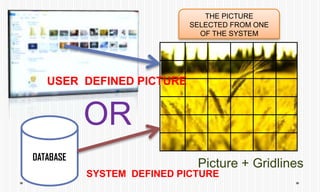
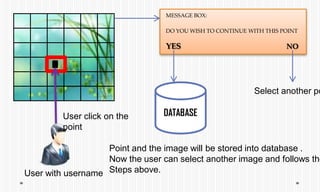
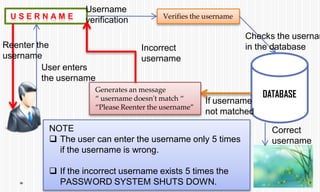
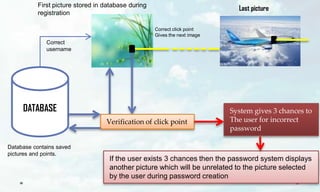
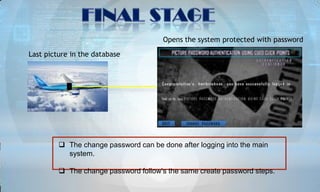
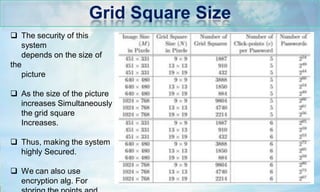
The document discusses picture password authentication, detailing recognition and recall techniques used in user registration and system login processes. It highlights advantages, such as improved security and user-friendliness, while also noting drawbacks like longer registration times and vulnerability to shoulder surfing. The document concludes that picture passwords offer a memorable yet secure alternative to traditional passwords, advocating for further research in this area.