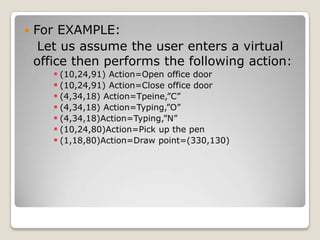
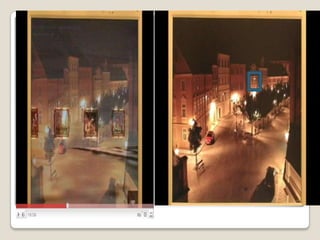
The document describes a 3D password scheme that enhances authentication by combining various methods: knowledge-based, token-based, biometric, and recognition techniques. This innovative system allows users to interact with virtual objects to create unique passwords, making them easier to remember and harder to guess. It also addresses common weaknesses of traditional password methods, including brute force attacks and intrusiveness of biometric systems.