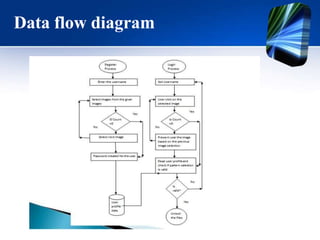
This document describes a graphical password authentication system project. The project aims to create a more secure authentication method than traditional text passwords by using images and click points. It will have hardware and software requirements and address problems with standard passwords like dictionary attacks. The objectives are to understand human memory for visual information and have users click points on an image as their password. It will provide security advantages over text passwords and be more user-friendly.