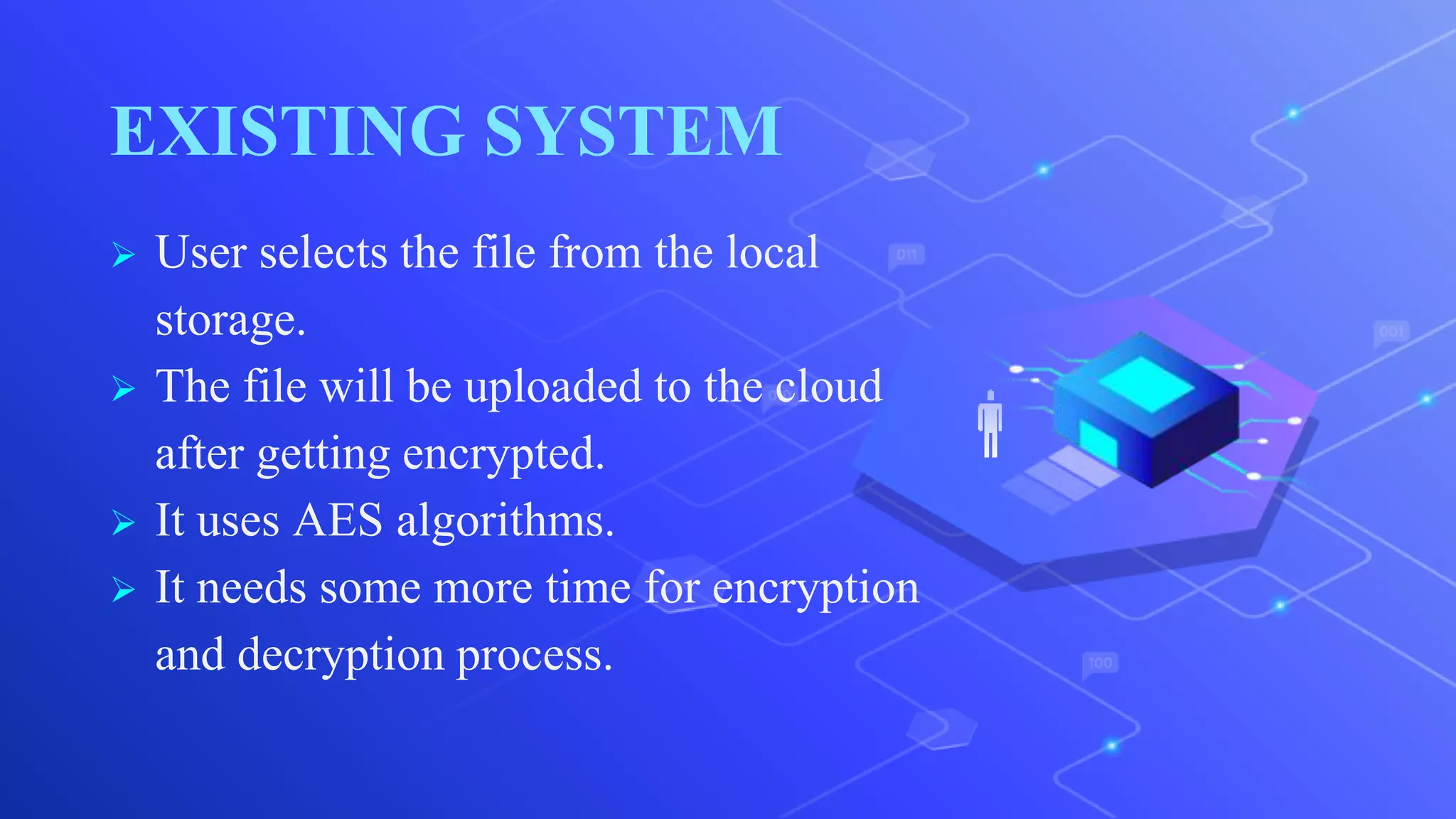
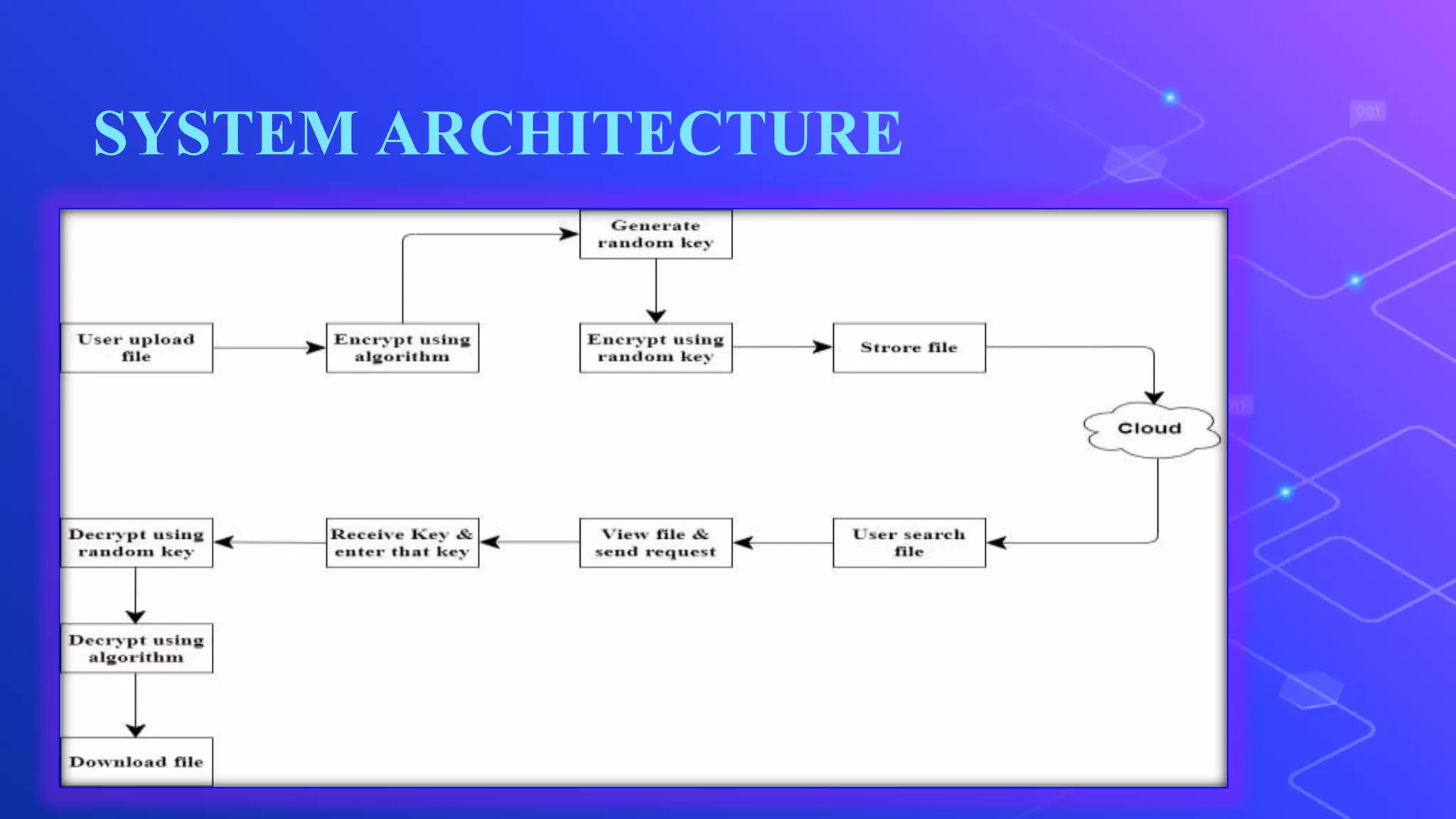
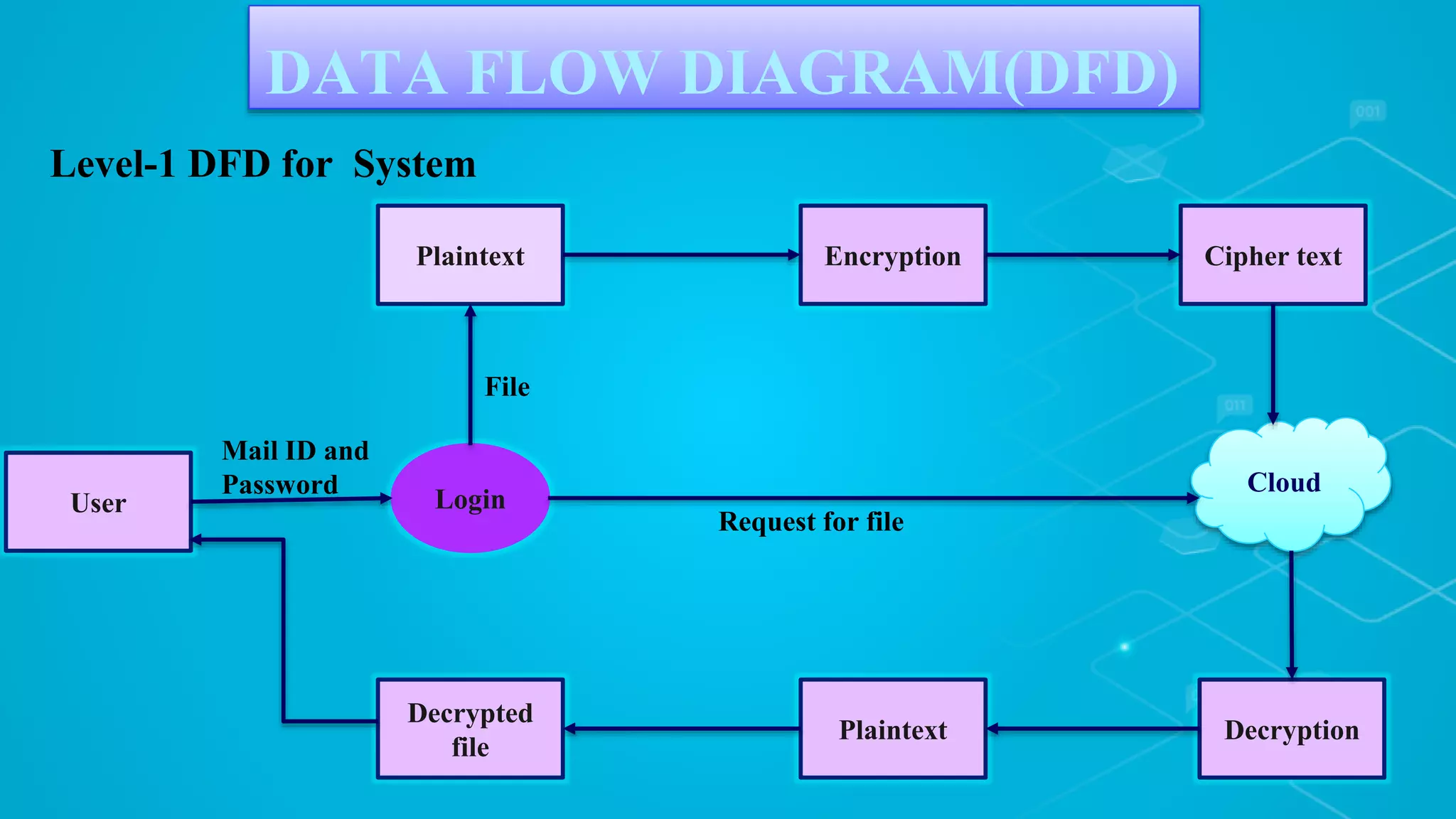
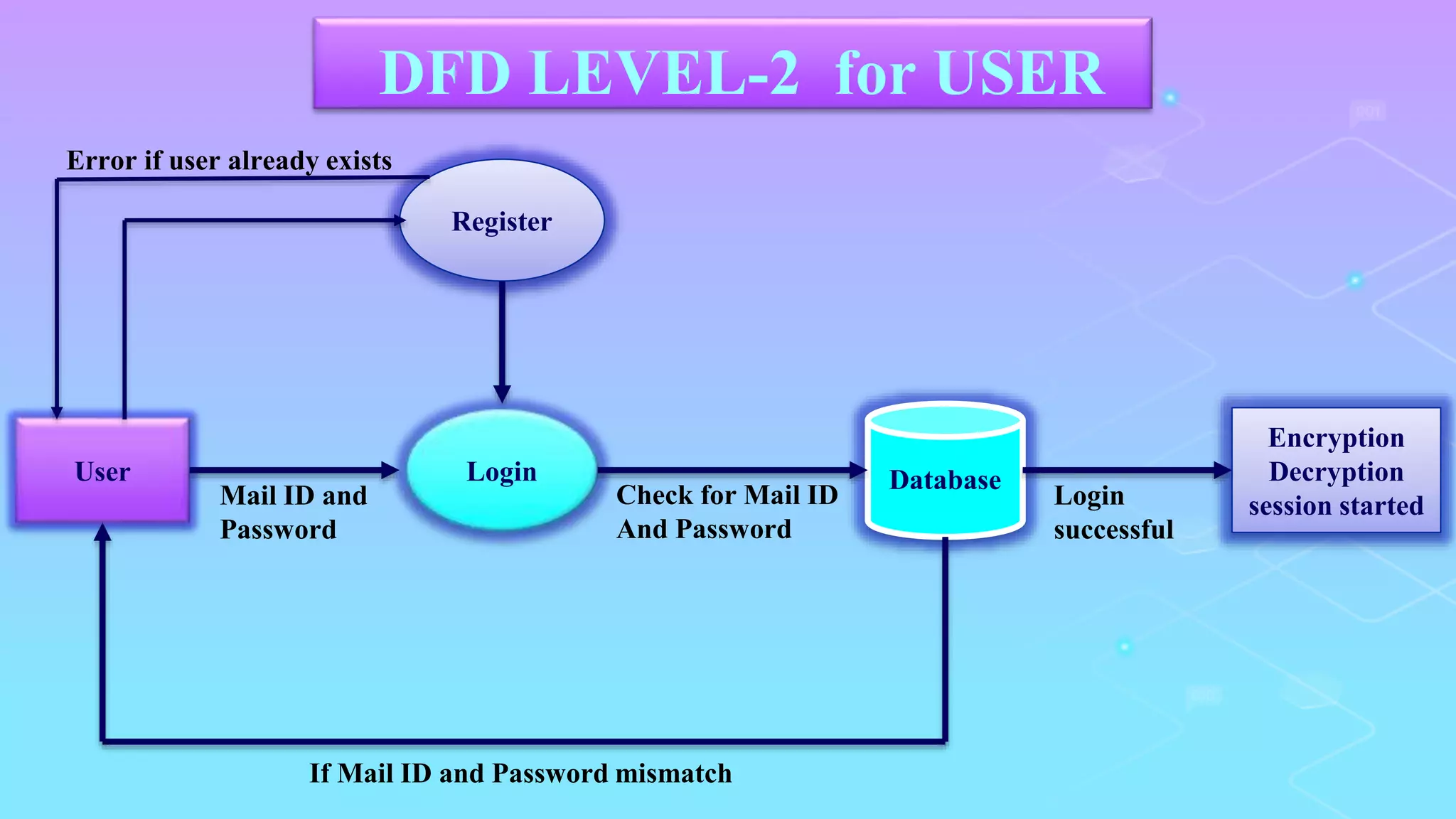
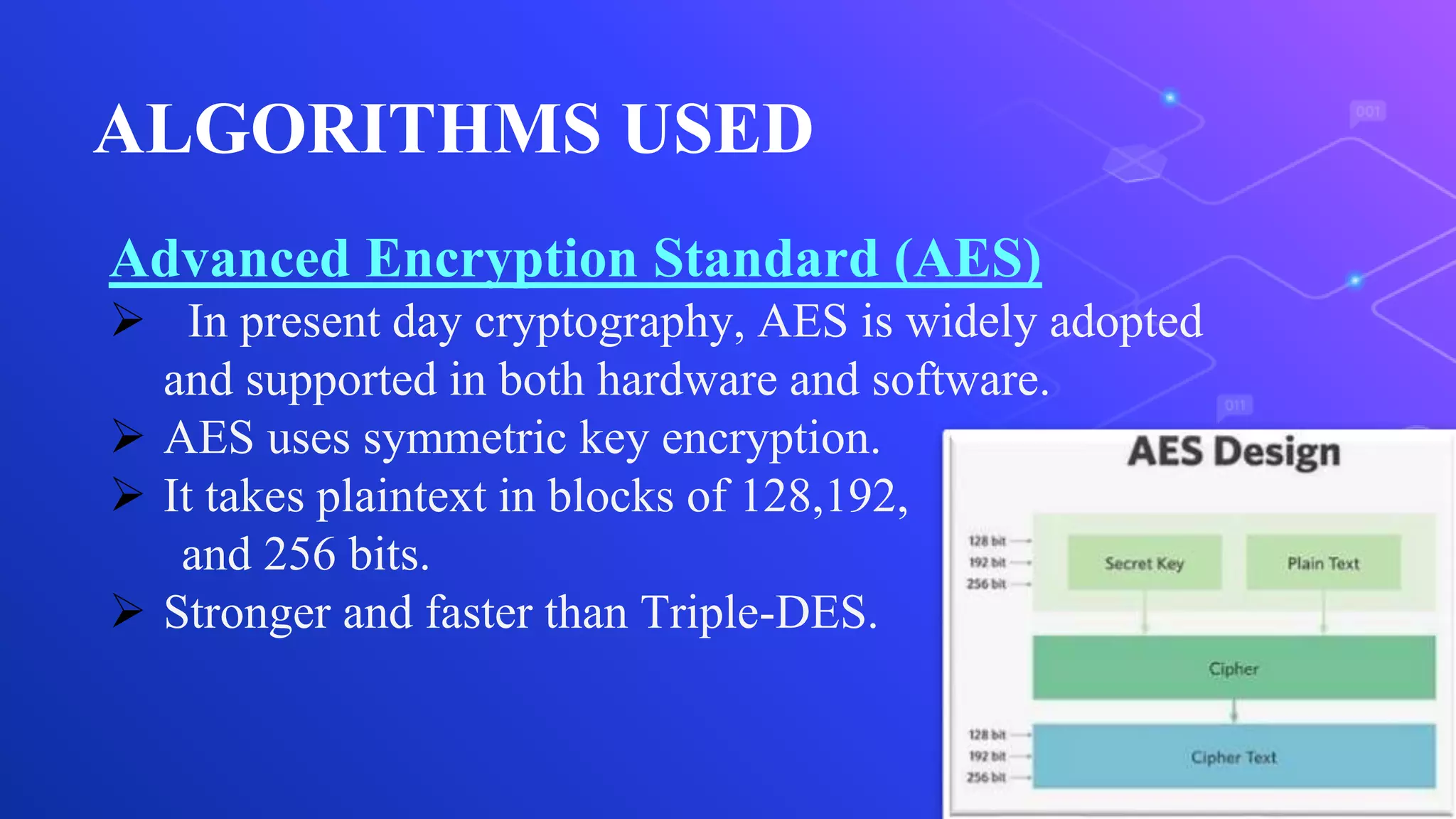
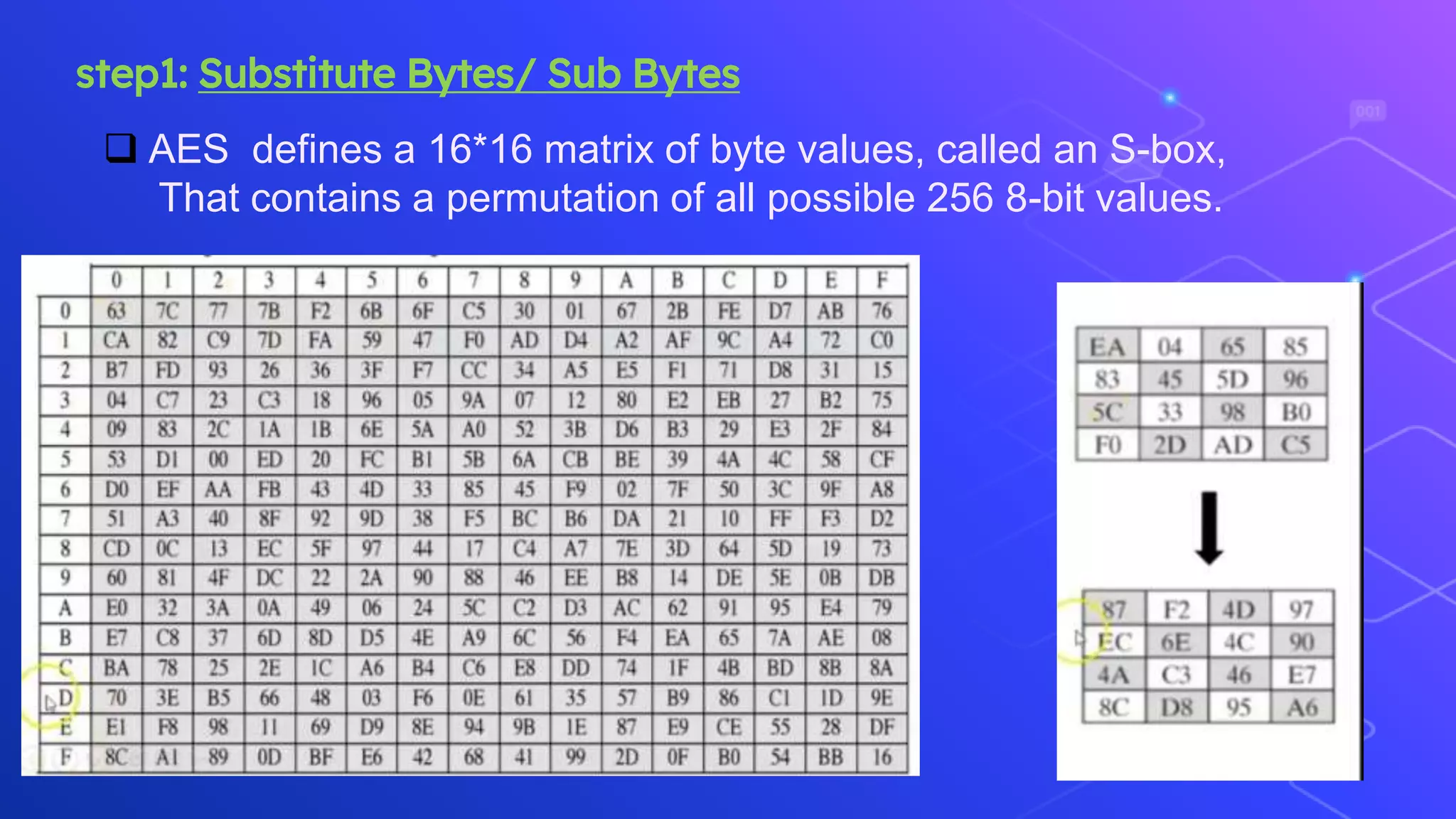
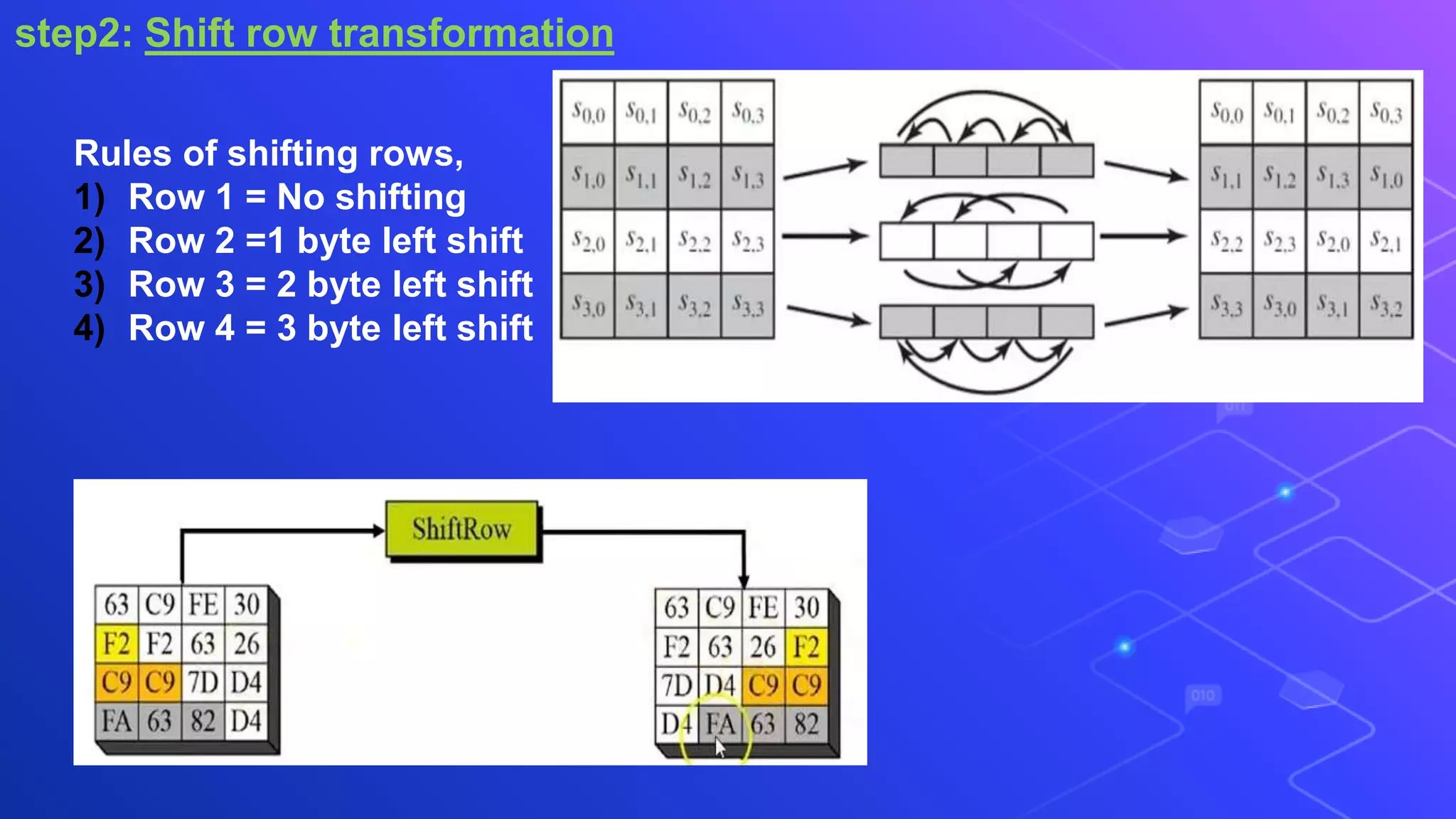
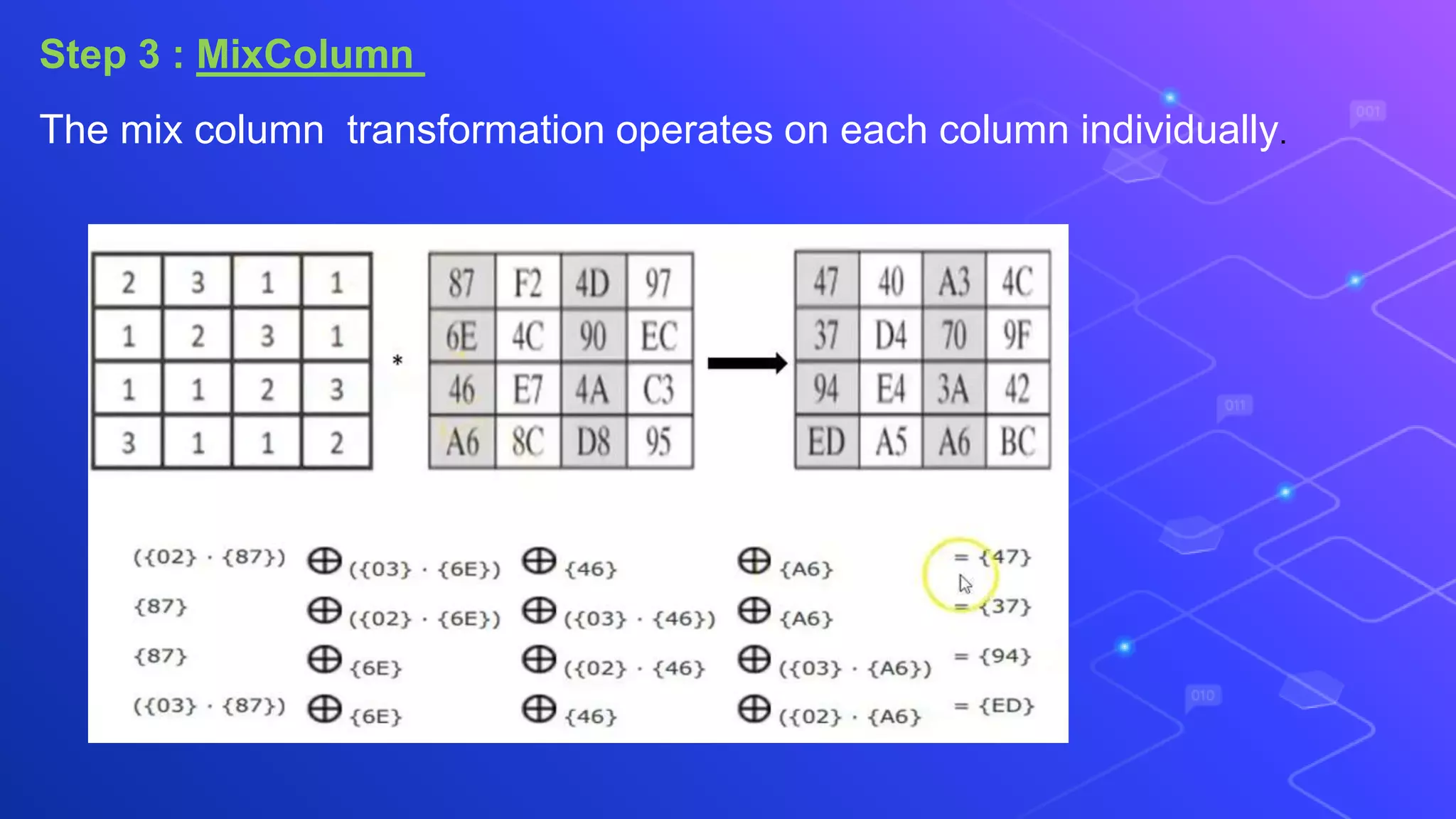
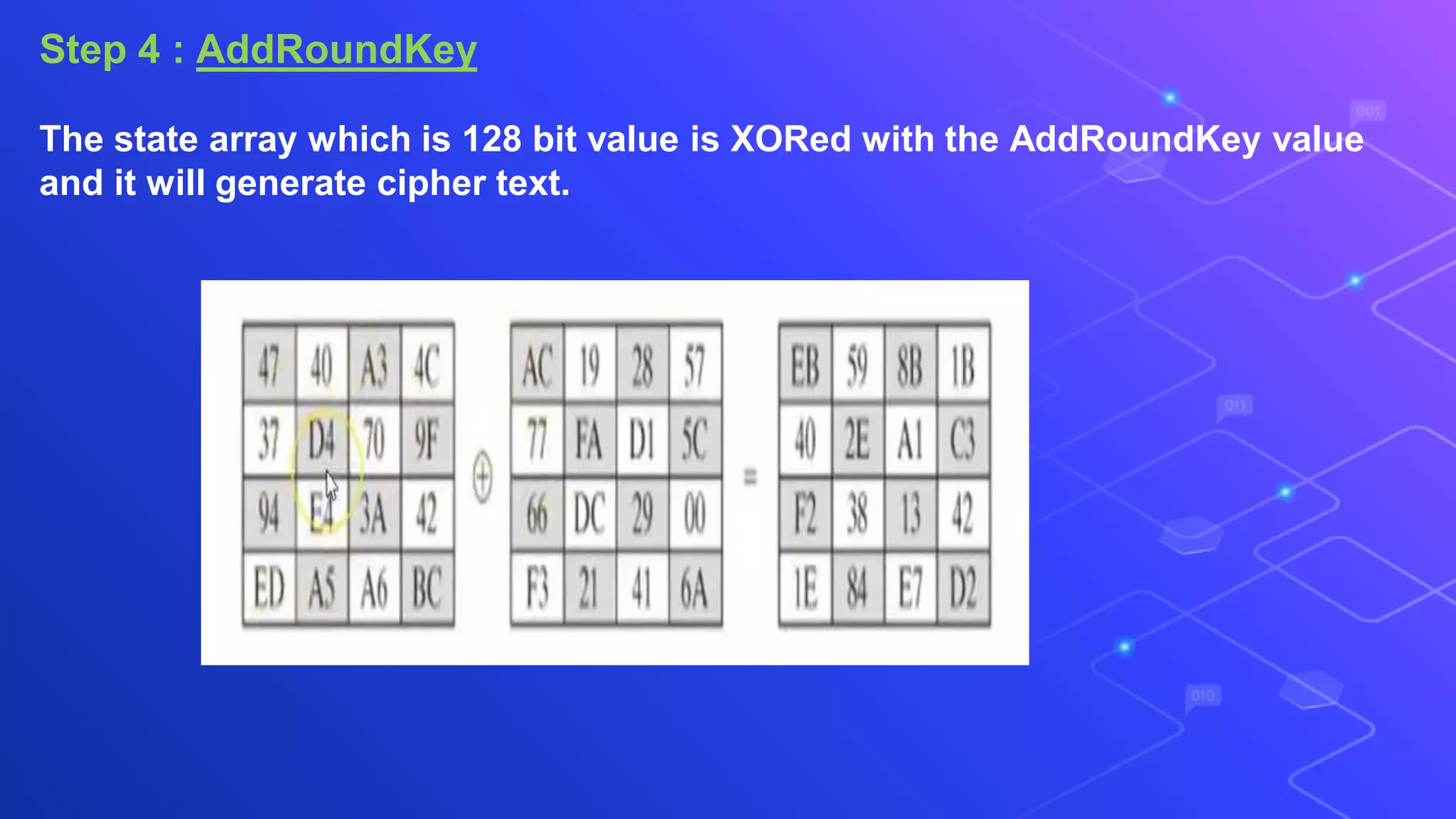
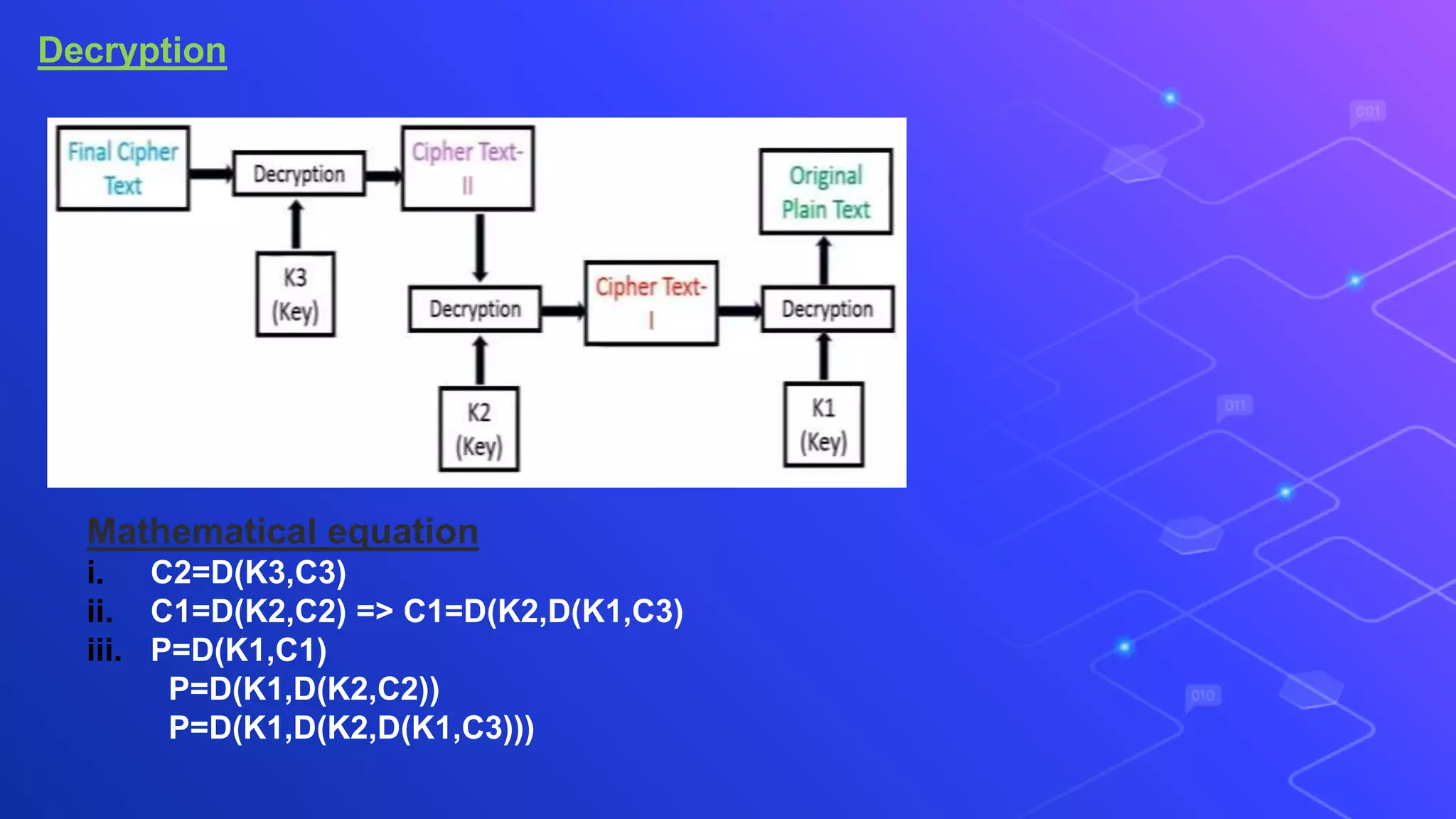
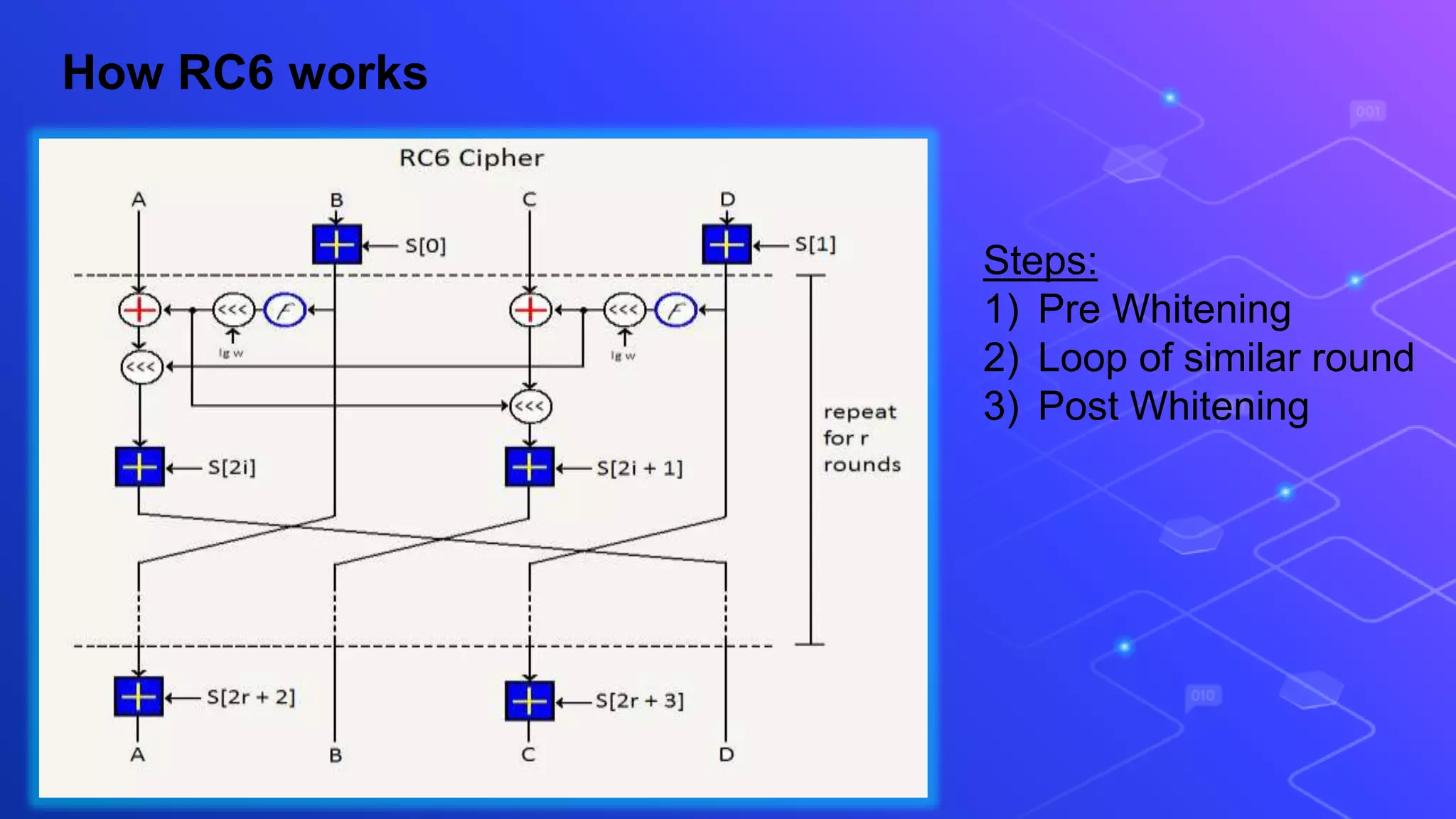
The document proposes a system for secure file storage on cloud using hybrid cryptography. It uses AES, 3DES and RC6 algorithms to encrypt files before uploading to the cloud. This provides higher security than using a single encryption algorithm. The system allows users to register, login, encrypt files, upload encrypted files to cloud, request files from cloud, decrypt files. It aims to provide secure data storage with less encryption/decryption time compared to existing systems.