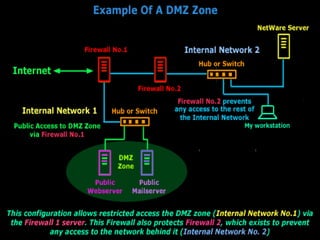
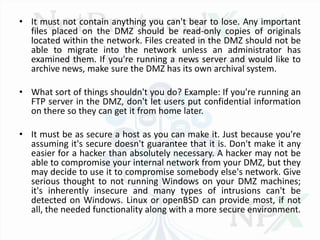
The DMZ, or De-Militarized Zone, refers to a portion of a network that is outside of the main security protections but still under the organization's control. Machines placed in the DMZ, like web servers and DNS servers, are less protected than internal machines and should not be brought back inside the network once placed in the DMZ. The DMZ acts as an isolated island that contains services to the public but should not contain any sensitive information or files that cannot be lost.