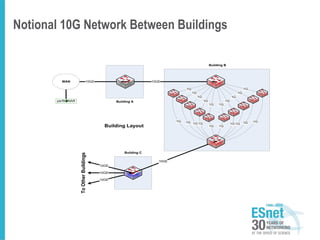
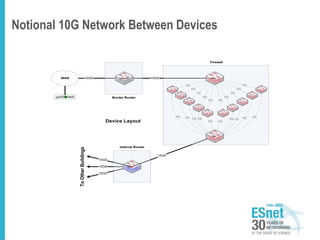
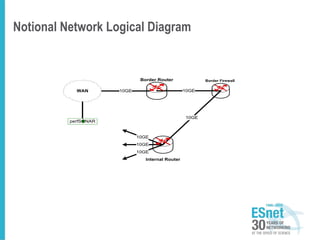
The document outlines the concept of Science DMZ as a security architecture designed to optimize security and performance for high-performance data transfer in scientific environments. It emphasizes the need for segmentation to manage risks and improve campus security posture while debunking myths about the role of firewalls in high-performance research networks. The document further discusses various security mechanisms and the importance of collaboration among stakeholders for effective implementation.